The post How DMARC Can Protect Against Phishing & Ransomware appeared first on eSecurityPlanet.
]]>This article will explore how this works in more detail:
- Ransomware & Phishing — a Toxic Combination
- How DMARC Counters Phishing & Ransomware
- Bottom Line: Adopt DMARC as an Essential Part of Email Security
Ransomware & Phishing — a Toxic Combination
Ransomware attacks accounted for approximately one out of every five cyber crimes in 2022 even as the number of ransomware attacks dropped by 23% compared to 2021. However, the impact of ransomware continues to grow as ransoms increase and attackers increase the magnitude of their overall threat with the addition of data exfiltration, extortion, and distributed denial of service (DDoS) attacks.
The costs of ransomware attacks can be massive, including downtime, data loss, business reputation damage, recovery expenses, forensic investigation expenses, and significant psychological damages for the teams. Ransomware depends upon phishing for the majority of ransomware attacks, yet phishing also delivers other types of attacks. Phishing, in turn, often depends upon email spoofing to trick users into falling for the phishing attack.
Ransomware Depends on Phishing
A ransomware attack can spring from a single email, and phishing provides the most common entry point for ransomware. However, in most cases, clicking on a bad phishing link does not launch ransomware. Attacks that do launch immediately can usually only encrypt the computer for the phishing victim, which limits the ransom-earning potential. More insidious, news-worthy, and revenue generating ransomware attacks need widespread access to the organization for maximum impact.
To achieve the broader goal, 63% of phishing attacks seek to compromise credentials. By stealing credentials, the ransomware gang can then infiltrate the network, expand access, and attack the organization as a whole.
Other Phishing-Delivered Attacks
Although ransomware makes headlines because of their highly disruptive and obvious impact, phishing attacks can deliver a number of other highly harmful attacks such as business email compromise (BEC), credentials harvesting, keyloggers, remote access trojans (RATs), cryptojacking malware, and other spyware. RATs tend to be the malware of choice because they offer the flexibility of future attack options and the hackers can also resell their access to ransomware-as-a-service providers, cryptocurrency mining groups, bot farms, and more.
Phishing Depends on Spoofing
Spammers send an estimated 3.4 billion emails every day, and Google blocks around 100 million phishing emails daily. Attackers use phishing to perform 47% of the attacks against North and South American organizations, 43% of the attacks against Asian organizations, and 42% of the attacks against European organizations. Microsoft even estimates that 94% of cyberattacks begin with a malicious email.
Yet no one clicks on an unconvincing email. Most people will be tricked by emails that appear to be legitimate and sent by a familiar brand. LinkedIn, Microsoft, Adobe, and Google are top brands used in broad phishing attacks, but smaller brands will also be used in more targeted attacks.
It’s not so difficult to fake an email. Attackers forge the “From” address to target victims with a fraudulent, “spoofed” email that appears to be from a legitimate sender.
For example, perhaps an administrator at the law firm of GenericContracts.com clicks on a phishing link and the attackers scope out the firm. The attackers may find the firm too small to be worth a ransom attack but also realize that the firm does local work for dozens of larger corporations.
The ransomware attackers may choose to spoof the GenericContracts.com domain and send phishing emails to the stolen contact names for those larger corporations with “Overdue Invoice” PDF files laden with malware. With an existing working relationship with GenericContractors.com, the corporate clients are more likely to click on the phishing emails and enable future ransomware attacks.
How DMARC Works to Stop Ransomware
Fortunately, DMARC provides a way to stop email using fake “From” addresses and reduce spoofing email attacks. DMARC provides email authentication not only to validate official emails but also to invalidate imposter emails by enhancing other email authentication standards.
How Email Authentication Works
DMARC is published with an organization’s Domain Name Service (DNS) and depends on the prior establishment of two other email authentication standards. The Sender Policy Framework (SPF) lists all domains authorized to send emails on behalf of the organization. The DomainKeys Identified Mail (DKIM) standard enables an organization to digitally sign emails from their domain using public key cryptography to verify that an email is delivered unaltered.
DMARC builds on SPF and DKIM to:
- Check for alignment, or consistency, between the “from” field in the body of the email and the SPF and DKIM domains
- Instruct the email server how to handle (ignore, quarantine, or discard) emails that fail SPF, DKIM, or DMARC checks
DMARC Alignment Example
Extending the example above, hackers may forge a fake email spoofing the accounts payable department of GenericContracts.com in the “From” field of the text the reader can see. However, the email itself will be sent from their own domain of SpammyPhishing.com, which shows up only in the header of the email (normally hidden from the reader).
However, if GenericContract.com deployed an effective DMARC policy, their clients’ email server would perform a DMARC check. The DMARC check would fail the email for being sent from a non-authorized domain and for having misalignment (or non-matching) header and email “From” fields. The receiving email server would be notified that the spoofed emails are fraudulent and likely send the impersonating email to the SPAM folder or even discard them.
Additionally, GenericContracts.com would receive a report from their clients’ emails servers that detail the campaign of phishing emails from SpammyPhishing.com. GenericContracts can then proactively warn customers about the phishing attack, search for their data breach, and report SpammyPhishing.com as a malicious URL.
How to Use DMARC
Security specialists recommend using DMARC to help protect against ransomware attacks as an essential email security tool. While DMARC primarily protects other organizations receiving emails attempting to impersonate the organization, DMARC makes the task of spoofing emails significantly more complicated for hackers and helps preserve the organization’s brand image.
Of course, it’s not the ultimate protection, as there are many other techniques hackers can deploy. Additionally, organizations need to enforce DMARC on their email receiving servers to perform the DMARC check. However, every protection deployed adds an additional layer of defense, and deploying DMARC also adds other benefits to the organization, such as improving the delivery of marketing emails.
Bottom Line: Adopt DMARC as an Essential Part of Email Security
DMARC can be challenging to configure correctly; however, it provides powerful email protection against spoofing, phishing, and related attacks such as ransomware. Organizations need to adopt DMARC to protect themselves and others against spoofing attacks and to help erode the threat of spam, which accounted for 48% of all emails sent in 2022.
For further reading on tools to secure email:
- How to Improve Email Security for Enterprises and Businesses
- 9 Best Next-Generation Firewall (NGFW) Solutions for 2023
- Top Secure Access Service Edge (SASE) Providers
- Top Secure Email Gateway Solutions
This article was originally written and published by Julien Maury on September 21, 2021 and updated by Chad Kime on June 6, 2023.
The post How DMARC Can Protect Against Phishing & Ransomware appeared first on eSecurityPlanet.
]]>The post How to Use Input Sanitization to Prevent Web Attacks appeared first on eSecurityPlanet.
]]>Attackers have been using classic flaws for years with a pretty high success rate. While advanced threat actors have more sophisticated approaches such as adversarial machine learning, advanced obfuscation, and zero-day exploits, classic attack techniques such as SQL injection, cross-site scripting (XSS), remote file inclusion (RFI) and directory traversal are still the most common attacks.
These techniques are often the first step on the way to privilege escalation and lateral movements. That’s why developers must sanitize and validate data correctly before processing transactions or saving any entry in a database.
Here we’ll focus on sanitizing and validating inputs, but other elements such as a server’s configurations must also be taken into account to properly secure forms.
See the Top Web Application Firewall (WAF) Solutions
What is the Difference Between Sanitizing and Validating Input?
Validation checks whether an input — say on a web form — complies with specific policies and constraints (for example, single quotation marks). For example, consider the following input:
<input id="num" name="num" type="number" />
If there’s no validation, nothing prevents an attacker from exploiting the form by entering unexpected inputs instead of an expected number. He or she could also try to execute code directly if submitted forms are stored in a database, which is pretty common.
To prevent such a bad situation, developers must add a validation step where the data is inspected before proceeding. For example, using a popular language like PHP, you can check the data type, the length, and many other criteria.
Sanitizing consists of removing any unsafe characters from user inputs, and validating will check to see if the data is in the expected format and type. Sanitizing modifies the input to ensure it’s in a valid format for display, or before insertion in a database.
Why You Should Use Input Sanitization and Validation
The most common techniques used against weak inputs are probably cross-site scripting (XSS) attacks, which involves attackers injecting malicious scripts into otherwise trustworthy websites.
Some XSS attacks are more obvious than others, which means that even if you take the time to sanitize and validate your inputs, a skilled attacker might still find a way to inject malicious code under specific conditions.
A classic attack demo consists of injecting the following script in a weak input, where the placeholder ‘XSS’ is arbitrary JavaScript:
<script>alert('XSS')</script>
If the content of the input is displayed on the page (or elsewhere), the attacker can execute arbitrary JavaScript on the targeted website. The typical case is a vulnerable search input that displays the search term on the page:
https://mysite.com/?s=<script>alert('XSS')</script>
It gets worse if the malicious entry is stored in the database. The demo code might look fun to play with, but in real-world conditions attackers can do a lot of things with JavaScript, sometimes even steal cookies.
When Not to Use Sanitization
The biggest problem with sanitization is the false impression of security it might give. Stripping unwanted chars and HTML tags is only one layer of checking. It’s often poorly executed and removes too much information like legitimate quotes and special chars while it does not cover all angles of attack. You cannot apply generic rules blindly.
The context is the key, which includes the programming languages in use. More on this later, but it’s important to follow a principle called “escape late” (for example, just before output) because you know the exact context where the data is used.
In my experience, the trickiest situations are when you need to allow raw inputs and other permissive configurations. In such cases, it becomes very hard to sanitize data correctly, and you have to maintain a custom whitelist of allowed characters or manually blacklist some malicious patterns.
It’s recommended to use robust libraries and frameworks instead.
More generally, developers must not hesitate to return errors on bad inputs instead of resorting to guessing or fixing, which is prone to errors and flaws.
Best Practices: Sanitizing Inputs, Validation, Strict Mode
There are some principles and best practices that dev teams can follow for the best possible results. We’ll cover the broad categories, along with specifics to watch for.
Don’t Trust User Inputs
Some websites don’t bother checking user inputs, which exposes the application to the maximum level of danger. Fortunately, that’s getting rarer thanks to security awareness and code analysis. However, incomplete sanitization is not a great solution either.
Here are a few of the possible attack paths you need to think about.
GET requests
If developers don’t sanitize strings correctly, attackers can take advantage of XSS flaws such as:
https://mysite.com/?s=<script>console.log('you are in trouble!');</script>
Classic cybersecurity awareness usually highlights the above example with a simple console.log or even an alert. However, it shows that anyone can execute arbitrary JavaScript on your page by simply sending a shortened version of the malformed URL to unsuspecting victims.
Some XSS flaws can even be persistent (stored in the database, for example), which removes the hassle from attackers of making the victim click on something by automatically serving malicious payloads to the website’s users.
Cookies
Websites often use HTTP cookies for session management, customization, and tracking. For example, developers can log in users, remember their preferences, and analyze their behaviors.
The server generates a cookie, or an approximate piece of data, and sends it to the browser to save it for later uses. As a result, stealing cookies allows attackers to be able to impersonate the victims by providing them with immediate access to the targeted accounts without login.
Moreover, hackers don’t have to compromise the victim’s computer. Because HTTP cookies are sent along with each request, attackers can intercept those requests to steal data during man-in-the-middle (MITM) attacks, for example.
A more sophisticated approach can use an XSS attack to insert malicious code into the targeted website to ultimately copy users’ cookies and perform harmful actions in their name.
While Google plans to phase out cookies in its Chrome browser next year, it’s still important to develop best practices for cybersecurity. For example, as of 2022, SSL (Secure Sockets Layer) is no longer an optional layer. However, if the code sends non-SSL requests, cookies will be sent in plain text, so make sure you are using SSL everywhere.
Another good practice is to always use the httpOnly attribute to prevent hijacking with JavaScript. The SameSite attribute is also recommended for developers.
While cookies are convenient for both users and developers, modern authentication and APIs allow better approaches. As storing data in client-side databases allows for many safety and privacy vulnerabilities, it’s better to implement other more secure practices instead.
POST requests
POST requests are server-side requests, so they do not expose data in the URL, for example, when you upload an image on your online account or when you submit a contact form, such as:
<form action="https://my-website.com/contact" method="POST">
A common misconception is that POST requests are more secure than GET requests. However, at most, POST requests are security through obscurity. While it is better to use POST requests for user modifications, it’s not great for security-related purposes, and it won’t harden security magically.
One very simple way to sanitize POST data from inputs in PHP could be through the commands:
filter_var($_POST['message'], FILTER_SANITIZE_STRING);
filter_var('[email protected]', FILTER_VALIDATE_EMAIL)
Another good practice in PHP is to use htmlentities() to escape any unwanted HTML character in a string.
As with cookies, always use SSL to encrypt data, so only TCP/IP information will be left unencrypted.
Directory traversal
If the codebase includes an image tag such as
<img src="/getImages?filename=image12.png" />
then hackers may try using
https://yourwebsite.com/getImages?filename=../../../etc/passwd
to gain access to users’ information.
However, if your server is configured correctly, such attempts to disclose confidential information will be blocked. You should also consider filtering user inputs and ensuring that only the expected formats and data types are transmitted.
Also read: Top Code Debugging and Code Security Tools
Don’t Trust Client-Side Validation
A common misconception, especially for beginners, is to rely on HTML and JavaScript only to validate forms data. While HTML allows defining patterns and required fields, such as setting a character limit or requiring specific fields to be filled, there is no HTML attribute or JavaScript code that can’t be modified on the client side.
Hackers might also submit the form using cURL or any HTTP client, so the client side is absolutely not a secure layer to validate forms.
Enable Strict Mode
Whenever you can, enable strict mode, whether it’s PHP, JavaScript or SQL, or any other language. However, as strict mode prevents lots of convenient syntaxes, it might be difficult to enable if you have a significant technical debt and legacy.
On the other hand, if you don’t code in strict mode, the engine starts making guesses and can even modify values automatically to make the code work. This opens up vulnerabilities hackers can utilize to inject malicious commands.
For example, in 2015, Andrew Nacin, a major contributor to WordPress, explained how a critical security bug could have been avoided just by enabling strict mode in SQL. He demonstrated how hackers could exploit a critical vulnerability by using four-byte characters to force MySQL truncation and then inject malicious code in the database.
While a simple solution to prevent such an attack would be to execute the command SET SESSION sql_mode = "STRICT_ALL_TABLES" it is impossible to enable this without breaking all websites powered by WordPress.
Consult the OWASP Web Testing Guide
OWASP, the Open Web Application Security Project, maintains a comprehensive documentation called the Web Security Testing Guide (WTSG) that includes input validation.
This guide offers information on how to test various injections and other sneaky attacks on inputs. The content is frequently updated, and there are detailed explanations for various scenarios.
For example, you can check out their page on Testing for Stored Cross Site Scripting to learn how persistent XSS works and how to reproduce the exploit.
Also read: OWASP Names a New Top Vulnerability for First Time in Years
Bottom Line: Sanitize, Validate, and Escape Late
Sanitizing and validating inputs is a mandatory dev practice but you cannot apply a generic solution to all entries. You have to consider the specific contexts to be able to block injections. Moreover, don’t store anything in the database without validating it, but also escape values before displaying them, as some injections can poison database records.
Another essential practice is to escape data as late as possible, preferably just before display. This way, you perfectly know the final context and there’s no way to leave data unescaped.
Lastly, spend time on fine-tuning static code analysis. This process can tend to generate a lot of false positives, such as XSS flaws that can’t be exploited; however, every single HTML attribute and tag that gets its value dynamically should be escaped.
While hackers won’t be able to exploit all tags to grab sensitive data or trick logged in users, you should still incorporate static analysis to prevent as many vulnerabilities as possible.
Read next:
The post How to Use Input Sanitization to Prevent Web Attacks appeared first on eSecurityPlanet.
]]>The post ESET PROTECT Review: Features & Benefits appeared first on eSecurityPlanet.
]]>This article looks at the key features and benefits of the ESET PROTECT Advanced solution.
ESET PROTECT
The PROTECT platform is ESET’s solution for the hybrid infrastructure era. As organizations adopt more cloud and virtual workloads, tools like PROTECT are critical to transitioning from on-premises systems and protecting the digital infrastructure. Administrators can use a single cloud-based management console to quickly deploy ESET and configure policies.
ESET Protect delivers:
- IT Operations improves workflows and reduces costs with controls for managing and controlling devices
- Security Management to protect networks and data
- Security Operations to detect, analyze, and respond to threats
- ESET LiveSense multi-layered technologies to improve protection, inspection, and responses to attacks
- Premium Services for threat intelligence, managed detection and response (MDR), support and more.
ESET PROTECT IT Operations
Within the IT Operations solution of ESET PROTECT, IT managers can implement a variety of controls and workflows. These options reduce costs by automating many time-consuming tasks related to deployment and policy implementation: device control, firewall management, inventory (hardware and software), mobile device management, rogue device management, and web control.
ESET PROTECT Security Management
Security provides a key component of the ESET PROTECT product and legacy ESET technology. The Security Management solutions include: automated response, cloud office security, encryption, endpoint detection, ESET LiveGuard malware detection, and multi-factor authentication.
Together, these tools lock down data and provide security for a comprehensive range of business infrastructure for small and medium-sized businesses. Of special note are two key features: full disk encryption and advanced threat defense provided by ESET LiveGuard Advanced.
Full Disk Encryption
Using a combination of proprietary encryption and OS encryption tools, ESET PROTECT supports Trusted Platform Module (TPM) and OPAL self-encrypting drives. Full-disk encryption significantly reduces data risks and protects critical systems.
Read more:
ESET LiveGuard Advanced
ESET LiveGuard Advanced provides ESET’s fully automated cloud-based machine-learning sandbox to perform behavioral analysis and deep inspection of attacks and malware. This tool directly counters zero-day threats and ransomware strains with a critical protection layer for investigating suspicious traffic before it enters the network.
The sandbox simulates actual machine behavior for all physical and virtual hosts, giving malicious files the chance to launch in an isolated environment while critical segments stay protected.
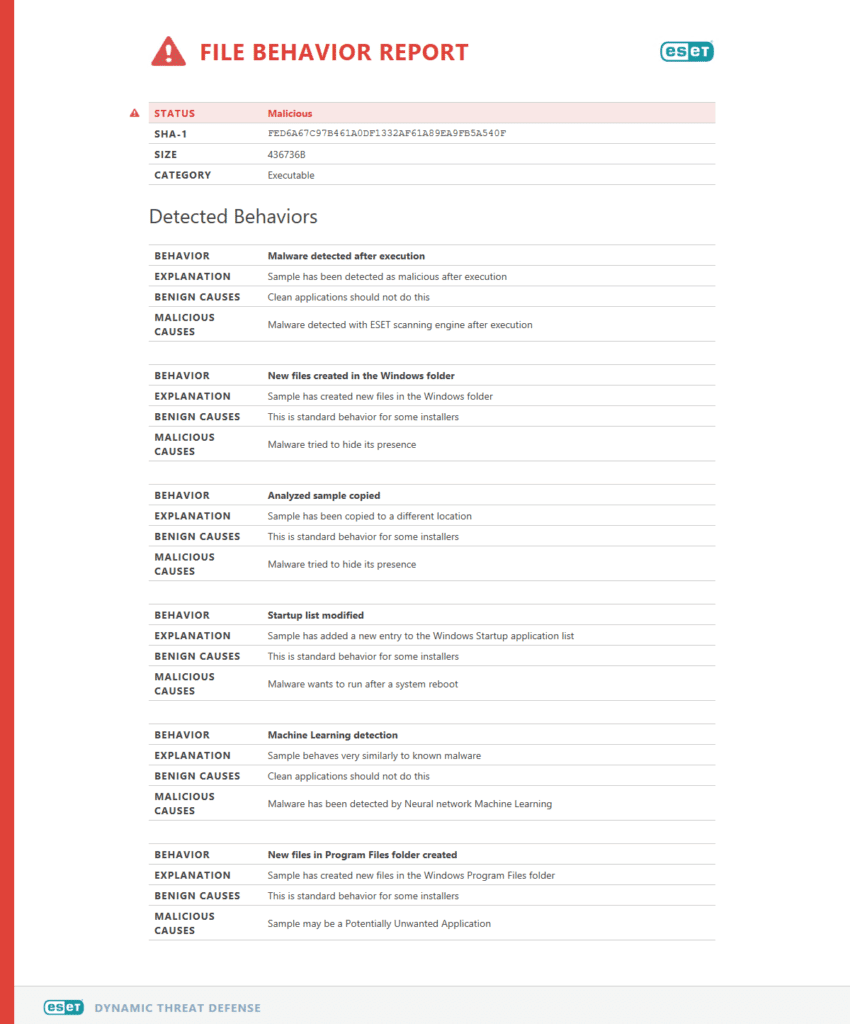
A sample ESET Dynamic Threat Defense sandbox file behavior report
ESET PROTECT Security Operations
The security operations tools within ESET PROTECT enable detection rules, enriched context for alerts, forensic tools, indicators of compromise, and tools for threat hunting and incident response. As part of this toolset, ESET Inspect enables eXtended Detection and Response (XDR) capabilities.
Using these tools internal security teams, managed detection and response (MDR) teams, or managed IT security service providers (MSSPs) have the tools and the information to rapidly detect, identify, investigate, and document an incident response.
ESET PROTECT LiveSense
The LifeSense technologies within the ESET PROTECT solution provide a host of cloud-based, multi-layered protections and tools. These tools include advanced machine learning, firmware inspectors, botnet protection, network attack protection, secure browsers, and more.
ESET PROTECT Premium Services
To complement the ESET PROTECT solution, ESET provides an array of premium services such as an infrastructure health check, deployment and upgrade services, premium support, threat intelligence, and managed detection and response (MDR) services.
ESET Competitors
- Bitdefender
- Broadcom
- Cisco
- CrowdStrike
- F-Secure
- Kaspersky
- McAfee
- Trend Micro
- Palo Alto Networks
Also read: Top Endpoint Detection & Response (EDR) Solutions
Recognition & Reviews
On Gartner Peer Insights, ESET has almost 700 customer reviews for ESET PROTECT with an average of 4.5 / 5 stars. ESET earned similar ratings from 166 reviews on TrustRadius (8.7 / 10) and 605 reviews on G2 (4.6 / 5). Highlighted features included the constant updates and upgrades, an easy onboarding and deployment process, and product capabilities.
Read more: Top XDR Security Solutions
PROTECT Business Pricing
ESET offers an interactive demo and a 30-day free trial of PROTECT. Pricing is listed on their website, but does not reflect potential discounts available through resellers and MSP / MSSP partners.
For businesses, ESET offers three versions of ESET Protect (Entry, Advanced, Complete) with licenses for a minimum of one year and five devices. Discounts are available for longer time commitments, more endpoints, and through occasional new customer promotions. ESET provides instant quotes on licenses for up to 3 years and 100 devices or less on its website and further needs can be explored with custom quotes.
ESET PROTECT Business pricing:
Entry
- $190 / 1 year / 5 devices ($38 / year / device) Minimum
- $4,940 / 3 years / 100 devices ($16.57 / year / device)
- Includes management console, endpoint protection, and file server security
- Detection and Response as well as Security Services are available on demand for additional fees.
Advanced
- $248.40 / 1 year / 5 devices ($49.68 / year / device) Minimum
- $7,560 / 3 years / 100 devices ($25.20 / year / device)
- Adds full disk encryption, and advanced threat defense
- Detection and Response as well as Security Services are available on demand for additional fees.
Complete
- $382.50 / 1 year / 5 devices ($76.50 / year / device) Minimum
- $11,610 / 3 years / 100 devices ($38.70 / year / device)
- Adds cloud app protection and email security
Quotes can also be obtained for separate ESET solutions for multi-factor authentication and Cloud Office security.
ESET: Company background
ESET’s roots start in 1987 in Bratislava, Czechoslovakia (Slovakia), developing its first anti-virus software, NOD. After the dissolution of the Soviet Union, ESET was formally established in 1992 and later started subsidiaries in the United States (1999), Czech Republic (2001), Poland (2008), and Canada (2012). With 35 years of anti-virus and endpoint protection experience, the vendor continues its threat research with 13 R&D centers worldwide.
As a security company, ESET’s name recognition may not be as high as other long-time cybersecurity brands. Yet with 35 years of experience, the Slovakia-based company has been around longer than most rivals.
In 2015, ESET made its sole acquisition of UK-based DESlock, a provider of encryption solutions for businesses. With over 1,800 employees in 24 branches around the world, ESET’s security solutions serve over 110 million users and business customers.
Also read: Why ESET makes our list for Best Cybersecurity Awareness Training for Employees in 2021.
This article was originally written by Sam Ingalls on October 9, 2021, and updated by Chad Kime on February 15, 2023.
The post ESET PROTECT Review: Features & Benefits appeared first on eSecurityPlanet.
]]>The post How to Prevent Cross-Site Scripting (XSS) Attacks appeared first on eSecurityPlanet.
]]>This is accomplished by tricking applications and websites into sending malicious scripts through the web browser. The most common method for taking over user sessions is to inject code using form fields or other data input fields. Developer best practices such as sanitizing and encoding user input are critical for preventing XSS vulnerabilities.
Risks of XSS attacks
XSS attacks pose vital security risks to both users and businesses alike.
Risk to users
Attackers that hijack a user’s session can take a number of malicious actions that affect them, such as making fraudulent charges using their bank cards or directly transfer money to other accounts.
XSS attacks can also be used to extract sensitive information from cookies and databases. This information can be used for identity theft.
Risk to businesses
If an attacker gets a hold of stolen user credentials, they can wreak havoc for the business as well. If the user has admin rights, an XSS attack can extend to the server-side.
Businesses can also suffer from a loss of credibility and brand trust if an XSS attack becomes public knowledge. Users and customers are likely not to return to a site if they know their information could be at risk.
Types of XSS attacks
Reflected XSS attacks
In reflected XSS attacks, malicious scripts are injected directly into an HTTP request. The script is reflected from the server in an HTTP response and then executed in a user’s browser. This is the simplest type of XSS attack.
DOM-based XSS attacks
Document-object model (DOM) based attacks require no interaction with the server. The vulnerability is the browser-side script. Web applications read the malicious script directly from a query string. They are similar in this way to reflected XSS attacks.
Persistent/Stored XSS attacks
Persistent, also known as stored, XSS attacks are the most dangerous type of attack because they have the potential to affect every user who visits the site. In this case, scripts are injected into a database through form fields.
The script is then stored indefinitely in the website’s database. Every user who then enters the site is vulnerable to having their session hijacked.
How to prevent XSS attacks
There are a number of precautions you can take to prevent XSS attacks.
Keep software up-to-date
Software should always be kept up-to-date for many reasons, including fixing bugs, improving performance, installing new features and patching security vulnerabilities. Regularly updating software will greatly reduce the vulnerabilities that leave a site or application open to XSS vulnerabilities.
You should also audit all of your applications to determine which you need and which you rarely use. Get rid of all the apps you don’t use to further reduce the number of vulnerabilities.
Scan for vulnerabilities
You should regularly scan all web-facing infrastructure for vulnerabilities. Many vulnerability scanning tools can identify applications and web sites that are vulnerable to XSS attacks. Here are three options that can help identify those vulnerabilities.
1 Intruder
Intruder is the top-rated vulnerability scanner. It saves you time by helping prioritize the most critical vulnerabilities, to avoid exposing your systems. Intruder has direct integrations with cloud providers and runs thousands of thorough checks. It will proactively scan your systems for new threats, such as Spring4Shell, giving you peace of mind. Intruder makes it easy to find and fix issues such as misconfigurations, missing patches, application bugs, and more. Try a 14-day free trial.
2 SanerNow Vulnerability Management Tool
SanerNow Vulnerability Management Tool is an all-in-one, continuous, and automated vulnerability management solution. Our advanced vulnerability management solution allows you to, -
• Run the industry’s fastest scans to discover all risks
• Get more than 160,000+ vulnerability checks
• Remediate vulnerabilities on all OSs like Windows, macOS, Linux, and 300+ third-party apps
• Monitor and control endpoints centrally
With SanerNow, you can manage multiple use cases from a single console.
3 Heimdal Security
A patch management solution that lets you deploy and patch any Microsoft and Linux OS, 3rd party and proprietary software, on-the-fly, from anywhere in the world and according to any schedule. With complete visibility and granular control over your entire software inventory. Patch anything, update everything, deploy, and upscale regardless of time-zone, machine availability or versioning.
Encode and sanitize user input
Input fields are the most common point of entry for XSS attack scripts. Therefore, you should always screen and validate any information input into data fields. This is particularly important if the data will be included as HTML output to protect against reflected XSS attacks.
Validation should occur on both the client-side and server-side as an added precaution. validating the data before it’s sent to servers will also protect against persistent XSS scripts. This can be accomplished using JavaScript.
Use escaping/encoding techniques for input uses where possible, such as HTML escape or JavaScript escape.
User input that must contain HTML can be cleaned via a trusted library for your development language.
Also, set the HttpOnly flag for cookies so they won’t be accessible via client-side JavaScript.
Use a web application firewall
A web application firewall (WAF) can be a powerful tool for protecting against XSS attacks. WAFs can filter bots and other malicious activity that may indicate an attack. Attacks can then be blocked before any script is executed and before it compromises the network.
Implement a content security policy
A content security policy (CSP) is an http response header that can define the functions a website is allowed to perform. They can be used to prevent a website from accepting any in-line scripts. This may be the strongest method at your disposal as it can completely block XSS attacks or at least greatly reduce the possibility of them.
Further reading:
- Top Code Debugging and Code Security Tools
- OWASP Names a New Top Vulnerability for First Time in Years
- How to Prevent SQL Injection Attacks
The post How to Prevent Cross-Site Scripting (XSS) Attacks appeared first on eSecurityPlanet.
]]>The post REMnux: The Linux Toolkit for Reverse Engineering and Malware Analysis appeared first on eSecurityPlanet.
]]>Whether you’re new to these specialties or an experienced investigator, REMnux contains many helpful Debian packages and configurations to perform advanced tasks, such as:
- Extracting IoCs (Indicators of Compromise)
- Disassembling/decompiling binaries or windows executables (such as PE files)
- Decoding, deobfuscating, decyphering, and decrypting
- Tampering (such as Burp Suite, Thug) and other network analysis (such as Wireshark)
- Investigating malicious code in various platforms (such as Android) and languages (e.g., Python, PowerShell, Java)
- Analyzing memory for code injections and other malicious activities
- Examining suspicious documents (such as PDFs, Microsoft Office, emails)
We’ll examine the pros and cons, but REMnux is definitely a great asset for those who want to focus on their work and skip the “installation hell.”
See our tutorials on Metasploit, Burp Suite and Nmap
Getting Started with REMnux
REMnux can be installed in a number of ways.
The tool is available as a ready-to-use virtual machine (.ova), which means it can run everywhere (Windows, Mac, Linux), but you can also add it directly to an existing system based on Ubuntu 20.04 with the REMnux installer (less than 60 MB).
Be careful if you have a next-gen Apple machine (m1++). At the time of writing, REMnux won’t run on an ARM processor such as Apple M1 or M2, as it’s based on an x86/amd64 version of Ubuntu (source: REMnux documentation).
I prefer using the virtual machine, as it provides an isolated environment and you can save snapshots, which is particularly convenient when you need to analyze ransomware and other sensitive binaries that can literally destroy your system.
So get the OVA image and import it into your favorite software, for example, Virtual Box or VMware.
What Problem Does REMnux Solve?
As the founder and primary maintainer of REMnux, Lenny Zeltser likes to say:
REMnux is for malware analysis as Kali is for penetration testing.
Kali Linux actually contains forensic tools, but the distro is meant for pentesting, and you usually have to install additional resources to perform malware analysis and reverse engineering correctly.
As these resources have their own dependencies, it’s sometimes a bit difficult to make them work properly on a system that is not meant for that, which can be very time-consuming, and sometimes frustrating because of the multiple incompatibilities and dependency conflicts.
See the Best Open-Source Distributions for Pentesting and Forensics
REMnux Pros
- It’s totally free and its components are open source
- It’s beginner friendly and well documented
- It’s easy to install (OVA, docker image, from scratch) and update (thanks to SaltStack technology)
- It’s very popular among malware analysts and security professionals
- The set is very comprehensive, so it’s unlikely you’ll need any additional resources
- Tools are pre-packaged, tested, and pre-configured
- You can use REMnux tools without even installing them, using Docker and REMnux containers
Cons
- The latest big release, at the time of writing, is v7 in 2020
- REMnux is a collection of open-source packages, which on one hand is great, but comes with the same dependency and update issues
- The distro won’t teach you how to master the various tools provided even if the documentation contains useful links and demos
Why Use REMnux?
REMnux is not just another Linux distro for ethical hacking or forensics. It contains pretty much everything you need to perform various analyses.
The added value is the “glue” REMnux uses to make these hundreds of tools work together and remove the hassle of installing and configuring everything by yourself. Those are some compelling reasons to try it.
The post REMnux: The Linux Toolkit for Reverse Engineering and Malware Analysis appeared first on eSecurityPlanet.
]]>The post Top Network Detection & Response (NDR) Solutions appeared first on eSecurityPlanet.
]]>
In the race to offer comprehensive cybersecurity solutions, the product known as network detection and response (NDR) is a standalone solution as well as a central component of XDR.
Whereas older solutions like antivirus, firewalls, and endpoint detection and response (EDR) have long focused on threats at the network perimeter, the intent of NDR is to monitor and act on malicious threats within organization networks using artificial intelligence (AI) and machine learning (ML) analysis.
Edward Snowden and the NSA breach of 2013, as well as dozens of other nightmares, point to the growing threat of inside threats for a universe of IT environments. Today, both outsiders with the right social engineering skills and disgruntled personnel pose risks to sensitive data when network architectures fail to implement microsegmentation and advanced network traffic analysis (NTA).
This article looks at the top network detection and response solutions in the budding sector, what NDR is, and what to consider in a NDR solution.
Also see the Top Network Monitoring Tools
Top Network Detection and Response Solutions
- Bricata
- Cisco
- Darktrace
- Exeon
- Extrahop
- Gigamon
- Vectra

Cisco
Almost 40 years after its start in Silicon Valley, Cisco remains one of the top IT and cybersecurity solution providers in the world. The Cisco Secure portfolio is massive, including next-generation firewalls (NGFW), MFA, vulnerability management, and DDoS protection. Alongside analytics solutions for cloud, malware, and logs, Cisco acquisition of Lancope in 2015 led to the development of its NDR solution, Cisco Secure Network Analytics. Built to detect and act on network threats faster, Cisco SNA is deployable as a cloud-based service, virtual machine, or on-premises appliance.
Cisco Secure Network Analytics Features
- Detection for signature-less, insider, and encrypted malware threats.
- Group-based policy adoption and reports to audit and visualize communications.
- The AnyConnect Network Visibility Module (NVM) for endpoint telemetry data.
- Malware analysis without decryption for advanced encrypted threats.
- Integrations with Akamai, Exabeam, Google, LogRhythm, Radware, and Sumo Logic.

Darktrace
Celebrating a decade in 2023, Darktrace was one of the fastest growing cybersecurity startups with a more turbulent ride since its listing on the London Stock Exchange in 2019. The Darktrace stack of solutions covers hardening, detection, and response for hybrid IT environments, including the vendor’s NDR solution, Darktrace DETECT, for applications, email, zero trust, operational technology (OT), and more. Today, the Cambridge, UK-based company puts artificial intelligence first in its security services for over 7,400 businesses in 110 countries.
Darktrace DETECT Features
- Self-learning AI to understand, secure, and optimize network interactions.
- Analyze thousands of metrics for known and unknown malware techniques.
- Integrations with AWS, Cisco, Fortinet, Microsoft, Okta, Rapid7, and ServiceNow.

ExtraHop Networks
Launched in 2007, ExtraHop’s success as a AI-based cybersecurity vendor led to its acquisition in July 2021 by Bain Capital for $900 million. Hailing from Seattle, Washington, the ExtraHop Reveal(x) 360 offers a unified threat intelligence platform for hybrid and multi-cloud IT environments. ExtraHop’s three core NDR solutions cover cloud security, network security, and IT operations. Whether it’s AWS, Google Cloud, or Azure, ExtraHop offers clients cloud-native security and comprehensive visibility into cloud workloads.
ExtraHop Reveal(x) Features
- Monitor sensitive data and workloads to prevent data breaches.
- Detects lateral movement and software supply chain attacks and vulnerabilities.
- Behavior and rule-based analytics to detect and respond to known and unknown threats.
- Identify threats and unusual activity faster to respond and remediate vulnerabilities.
- Integrations with Check Point, Citrix, CrowdStrike, IBM, Palo Alto Networks, and Splunk.

Vectra AI
Started in 2012, Vectra already stands out among the NDR marketplace, offering managed detection and response (MDR) and its threat detection and response platform. The San Jose-based company solutions span attack surfaces for all major cloud services, data centers, and Microsoft 365, with specialized threat management for ransomware, supply chain attacks, data breaches, and account compromise. Companies have plenty of integrations to choose from for tools like EDR, SIEM, threat intelligence, and Secure Access Service Edge (SASE).
Vectra Threat Detection and Response Platform Features
- Capture public cloud, SaaS, identity, network, and EDR data for analysis.
- Multiple AI modeling techniques to audit network workloads.
- Threat and risk prioritization to inform administrator action and investigation.
- Automated and manual response options for securing networks in real-time.
- Integration with AWS, Azure, Juniper, Pentera, SentinelOne, VMware, and Zscaler.

Bricata
Launched in 2014, Bricata is another vendor specializing in NDR capabilities and successful enough to catch the attention of OpenText, who acquired the Maryland based vendor in November 2021. While OpenText continues its acquisition spree (notably, acquiring Micro Focus this week), Bricata’s next-generation NDR platform continues to give security administrators visibility into user, device, system, and application behavior inside networks. In addition to real-time context and alerts, Bricata offers clients advanced forensics and threat hunting tools to make the most of investigations and remediation actions.
Bricata Next-Gen NDR Features
- Software-based and hardware agnostic with consumption-based pricing.
- Signature inspection, ML-based malware conviction, and anomaly detection.
- Automated analysis for threats with prioritized workflows to respond fast.
- Extract and store metadata for investigations and future use.
- Technology partners with Cylance, Elastic, Garland, OISF, Proofpoint, and Splunk.

Gigamon
Started in 2004, Gigamon has long been in the network visibility game with a portfolio today consisting of traffic intelligence and cloud, network, and data center visibility. Within its network security stack, Gigamon ThreatINSIGHT is the company’s cloud-based NDR solution for high-fidelity adversary detection and response. Evidence of Gigamon’s strength as an NDR solution includes being a connector for almost every other top NDR pick. Their larger technology alliance partners is extensive with 60 of the best vendors for managing network performance, vulnerabilities, and cloud infrastructure. Previously a publicly traded company (NYSE:GIMO), Gigamon was acquired by private equity for $1.6 billion in 2016.
Gigamon ThreatINSIGHT Features
- Inspection of encrypted traffic and lateral movement for any device, network, and flow.
- Omnisearch triage and investigation with up to 365 days of network metadata.
- Ongoing detection tuning and QA with the Gigamon Applied Threat Research (ATR) unit.
- Sensor and traffic diagnostics via the Gigamon technical success and SaaS Ops teams.
- Integrations with AWS, Cisco, CrowdStrike, FireEye, New Relic, Nutanix, and Riverbed.
Exeon Analytics
Another budding NDR vendor, Exeon offers advanced security analytics to protect IT and OT environments. Launched in 2016 from the campus of the Swiss Federal Institute of Technology, the Zurich-based company’s ExeonTrace seamlessly analyzes security-related log data from existing infrastructure. With comprehensive visibility, Exeon can help client’s identify data leaks, misconfigured devices, shadow IT, and unusual services. While Exeon mentions the ability to connect SIEM, EDR, and IDPS systems, the list of connectors wasn’t immediately available.
ExeonTrace Features
- Fast deployment which doesn’t require sensors or agents.
- AI-based threat scoring to prioritize investigations.
- Insight-driven visualizations including a global map of traffic sources.
- Network log data analysis for lightweight solution vs. data-heavy traffic mirroring.
Honorable Mention NDR Solutions
| Arista Networks | Blue Hexagon | Broadcom Symantec |
| Corelight | Fidelis | Hillstone Networks |
| LogRhythm | Lumu | Progress Flowmon |
| Stamus Networks | Threatbook | VMware |
What is Network Detection & Response?
Network detection and response (NDR) solutions complement tools like EDR and SIEM to analyze and detect malicious network traffic. In the next generation of network traffic analysis (NTA), NDR solutions offer AI and ML-based techniques to evaluate the latest signature-less attacks and unusual traffic patterns. When threats are detected, NDR solutions alert administrators to act or automate pre-configured preventative measures.
NDR Features
- Cognitive modeling to monitor and analyze tactics, techniques, and procedures (TTP).
- Real-time and historical view of traffic for investigating suspicious behavior.
- Context-driven visibility, advanced analytics, and IoC identification for threat hunting.
- Built-in advanced detection with ability to fine-tune configuration management.
- Integration with EDR, SIEM, SOAR, and other network security solutions.
Network Security and NDR
NDR is a complementary network security tool, joining a handful of other critical systems for an enterprise cybersecurity architecture:
- Cloud security
- Endpoint detection and response (EDR)
- Intrusion detection and prevention systems (IDPS)
- Network traffic analysis (NTA)
- Next-generation firewalls (NGFW)
- Security information and event management (SIEM)
- Security orchestration, automation, and response (SOAR)
- User and entity behavior analytics (UEBA)
In 2015, Gartner Research Director Anton Chuvakin introduced the conceptual framework for what would become the “SOC visibility triad”. In a 2020 retrospective, Chuvakin explains how logs (via SIEM), endpoint data (via EDR or XDR), and network data (via NTA and NDR) are critical to security visibility.
How to Choose a NDR Solution
As an emerging security solution, NDR shouldn’t be the first priority for companies building out their cybersecurity infrastructure. That said, the above network detection and response solutions offer plenty for enterprise organizations with well-established cybersecurity postures.
While NDR vendors offer opportunities to bundle other network security tools, including robust portfolios from vendors like Cisco and Sangfor, a top consideration remains ease of integration with existing security systems for SIEM and EDR. Because most organizations aren’t starting from scratch, NDR vendors must strive for interoperability with the leading network security products.
In a crowded marketplace of cybersecurity solutions, NDR is yet another that is on the rise. Only time will tell how niche an audience it will serve. Keep an eye on how the NDR sector evolves in the years to come and whether it survives as a standalone solution and market or gets absorbed by more comprehensive frameworks like XDR.
The post Top Network Detection & Response (NDR) Solutions appeared first on eSecurityPlanet.
]]>The post Highly Sophisticated Malware Attacks Home and Small Office Routers appeared first on eSecurityPlanet.
]]>Such routers are rarely monitored or up-to-date, making them attractive targets for hackers to reach adjacent corporate networks. According to Lumen’s Black Lotus Labs, this sophisticated campaign “has been active in North America and Europe for nearly two years beginning in October 2020.”
The attacks include ZuoRAT, a multi-stage remote access Trojan (RAT) that specifically exploits known vulnerabilities in SOHO routers to hijack DNS and HTTP traffic. The goal is to pivot from the router to workstations in the targeted network, where other RATs will be deployed to establish persistent and undetected communication channels (C2 servers).
The name “ZuoRAT” is based on the Chinese word for “left” (after the actor’s file name, “asdf.a”, which suggests a keyboard progression of the left hand). For now, the advanced persistent threat (APT) group behind the campaign remains unknown.
See The Best Wi-Fi 6 Routers Secure and Fast Enough for Business
State-Sponsored Hacking Campaign
ZuoRAT is deployed to “enumerate a host and internal LAN, capture packets being transmitted over the infected device and perform person-in-the-middle attacks,” the researchers wrote, which suggests a complex operation, probably performed by a state-sponsored group. The schema below from Black Lotus Labs gives a nice overview of the campaign:
Evidence containing Chinese characters and references to “sxiancheng” were found in multiple Windows samples. C2 servers that interact with the Windows RATs were hosted on internet services from China-based organizations such as Alibaba’s Yuque and Tencent.
Researchers believe ZuoRAT is a “heavily modified version of the Mirai malware.” The campaign is pretty advanced, judging from the technical details and the TTP (tactics, techniques and procedures) used to evade detection.
The threat actors even disguised their server with fake landing pages like this one:
All these procedures and the use of proxy servers in multiple countries might seem like a labyrinth, but researchers believe hackers built it on purpose to cover their tracks.
See the Best Antivirus Software
How to Protect Against ZuoRAT
Defenders and security teams can find the complete list of IoCs (indicators of compromise) on this GitHub page.
It’s important to note that ZuoRAT won’t be cleaned after a simple reboot and may even require a factory reset. Because it can deploy other malware on various operating systems, including Windows, Linux and macOS, it will likely spread to any connected device, so it’s not just about the router.
The shift to remote work can be problematic for the security of corporate networks, as even the most secure organizations have to allow in some external traffic. However, while users and admins won’t be able to catch everything, good practices do help, for example:
- Users of SOHO routers should apply security updates. Aggressive patching is often a good approach, even if it can have some inconveniences like incompatibilities and bugs.
- EDR solutions can spot unusual activities or agents on the machines connected to a network.
- And a zero trust framework can help verify users and limit access.
It’s always the same process: attackers look for easy prey to gain initial access. APT groups usually focus on stealth, which often involves taking bypaths and pivoting from compromised routers.
Read next: Best Wi-Fi Security & Performance Testing Tools
The post Highly Sophisticated Malware Attacks Home and Small Office Routers appeared first on eSecurityPlanet.
]]>The post IT Buyers Don’t Take Security Seriously Enough: HP appeared first on eSecurityPlanet.
]]>Security is weird that way. I grew up in the security business – my family owned one of the largest tech security firms when I was a kid. I worked for Pinkerton’s Security undercover, as a Sheriff’s Deputy. Security teams and analysts have reported to me in a couple of positions, at development and analyst firms. I worked as a security auditor. In short, I know security and take it very seriously. The problem in HP’s case is that buyers aren’t taking security seriously enough – and that could probably be said for hardware buyers in general.
Security is always about two things: Being good enough so that if there’s a problem you don’t look negligent, and being better than your peer companies so that attackers attack them and not you. Now, there are different levels of security. Financial institutions, healthcare, pharma, government and critical infrastructure often require high levels of security, but even then, it is just a different level of “good enough” – although in an era of advanced persistent threats and software supply chain attacks, “good enough” probably means that a lot more security is needed than there used to be.
HP’s Security Investment
Most tech vendors are on the same “good enough” page. But HP stands out and excels at security. There is a method to the madness, and while I respect and appreciate HP’s extreme efforts, with some noted exceptions, HP’s security efforts go further than most buyers think they need to go, even though it is clear to me and a lot of other people that the bar has been set way too low.
HP has created a company within a company called Wolf Security, which operates uniquely as a unit to address security problems broadly. They have a unique AI implementation that looks for behavioral changes in the user or environment and moves to stop irregularities allowing for a relatively robust zero day defense. They put a unique security chip in their commercial hardware that provides a level of hardware security that is currently unmatched. And their security screen implementation is currently market-leading (you can only see the information if directly facing the screen when this is on). They’re even publishing their own unique, cutting-edge cybersecurity research.
The problem is that IT buyers don’t appreciate all that and rarely even it give it their full attention, resulting in under-utilized and underappreciated security features – and it also means that HP investors don’t get the full potential return from their investment.
Let’s explore HP’s security investment conundrum – and what it tells us about the IT market in general.
Also read: Top Endpoint Detection & Response (EDR) Solutions
HP’s Security Not Valued by IT Buyers
I refer to HP’s high security standards as a “problem” because they adversely impact the company’s bottom line, but really, it’s also a public problem because we are all vulnerable to attack. Even though we are facing massive efforts from nation-states and others to disrupt and damage our cyber infrastructure, we still don’t take device security seriously enough. CSOs (Chief Security Officers) are rarely involved in setting equipment specifications, and on the rare occasions when they do, they don’t often get all their requirements met.
I met with HP’s security team last week and they expressed frustration that their intensive focus on security wasn’t resulting in a higher ranking by corporate RFQs (requests for quotes). When they did get CSOs involved, they would only set the specifications but wouldn’t assure they were met, and the competing vendors just clicked the box saying they were compliant when they weren’t.
With China, Russia, North Korea and a growing number of criminal organizations funding attempts to steal data or disrupt operations on a global scale at ever-growing levels, we should be taking security far more seriously, but devices and employees remain overexposed to attacks that range from phishing to malware insertion.
The resulting breaches are presented as unavoidable when they are anything but. This is because security is still not a high enough priority to not only ensure that systems are more secure, but also to ensure that IT doesn’t strip out the security functionality off these systems when they reimage them prior to deployment.
So HP’s problem (and it’s really everyone’s problem because we are the ones exposed) is that purchasing and CSOs aren’t taking device security seriously enough and, as threats continue to escalate, this leaves us badly exposed and HP’s products not performing to their potential.
HP’s Security ‘Problem’ is Our Problem
The bar is set too low for device security given the current global cyber war environment we live in. Companies, employees and individuals are at risk because we just aren’t taking security seriously enough. CSOs should be engaged when it comes to connected hardware to ensure that hardware can stand up to the current threat challenges.
For me this is less about HP’s financial performance than it is about keeping me and the people I care for safe. HP’s deep defenses should be the standard but they’re not. That’s why HP’s big security problem is an even bigger problem for all of us.
We need IT buyers to begin to value HP’s security investments – and for other vendors to follow suit.
Read next: The Best Antivirus Software of 2022
The post IT Buyers Don’t Take Security Seriously Enough: HP appeared first on eSecurityPlanet.
]]>The post Why You Need to Tune EDR to Secure Your Environment appeared first on eSecurityPlanet.
]]>This allows EDR to deploy very quickly, but it also allows for a number of security vulnerabilities. Here we’ll discuss why EDR vendors choose these configurations, and how organizations can tune their EDR systems to fit their organization and improve security.
Why Do EDR Vendors Deploy Generic Installs?
When an EDR vendor sends a product out for installation, they need the process to go smoothly. If the product causes issues, the client might pull the plug early and cancel the install.
A major factor in a smooth installation is to avoid false positive security alerts that might overload a security team. To avoid these false alerts, the vendor will supply a rather generic version of the EDR tool that will avoid such issues.
Even more importantly, the vendor will deploy EDRs with minimal conditions that would automatically quarantine or isolate the endpoint. Customers generally want to prioritize uptime, so vendors will err on the side of caution to merely generate alerts when isolation might be a more appropriate response for the malicious action.
Hackers Are Prepared for Generic Installations
While the generic installation may not trigger false alarms, it may also miss legitimate indicators of an attack. However, what those specific attack alerts should be vary from organization to organization and from user group to user group, so development of these alerts will be left up to the installation team.
Cyber criminals go after endpoint protection software all day, every day. Since many organizations fail to change the default setup, these attackers know the EDR defaults and understand how much they can do without triggering alerts.
Customization is not an overall solution to defeat attackers; however, it can create tripwires to trigger early alerts or block basic tools to make attacks more difficult. Because a custom environment doesn’t conform to generic expectations, attackers will be slowed and need to test boundaries.
EDR Customization Objectives
When determining what changes will help a company without flooding their security team with false alerts that waste time and money, the fundamental consideration should be to deeply study the organization and understand the answers to three basic questions:
- What should never happen?
- What should be expected all of the time?
- How do certain user groups behave differently?
These questions should be answered and prioritized within the context of:
- Risk: Which are the most valuable resources? What data cannot afford to be stolen? Which systems and operations cannot afford to be disrupted? And what are the most expensive resources to replace if destroyed (in terms of money and time)?
- Attack Exposure: Which resources are most exposed to the web or public access?
- EDR Dependence: What other controls are protecting assets? Which primarily depend on EDR?
- Vulnerabilities: Which MITRE ATT&CK techniques are most relevant and not currently generating alerts?
The answers for these questions should create a fairly unique matrix of assets to protect and behavior norms for each organization. This matrix will be the basis of customization and what types of alerts to add.
Also read: How to Use MITRE ATT&CK to Understand Attacker Behavior
Context-Specific Alerts
Covering all possible alerts would be a never-ending task, but specific categories of behavior and attacks can be considered as a place to start.
Atypical User Behavior
Determine what is normal for this company and for user groups. Atypical or abnormal behavior should be flagged for an alert.
Most users will never need to use an operating system (OS) command line, edit the Windows registry, or use red team attack tools such as Mimikatz or Cobalt Strike. Yet, we often see that generic installations will not send an alert on these events.
Similarly, in most companies, the sales team should never be trying to access the corporate server’s Active Directory. Therefore, the EDR tool for the devices used by this user group should generate alerts on those activities.
The larger an organization, the more difficult it will be for an IT team to understand what is normal and what is not normal across all groups. However, communication with managers can provide a good starting point, and many tools harness artificial intelligence (AI) and machine learning (ML) algorithms to improve visibility into typical activities.
Also read: 10 Top Active Directory Security Tools
Critical Data Access
The most critical data should have tightly restricted access. User groups without proper access rights should always generate alerts when they attempt to access critical data.
For example, the marketing department in a pharmaceutical company should never be trying to access the drug research data, and the warehouse employees of an e-commerce company should not be trying to access employee personal information from the file server’s human resources (HR) folders.
In a sprawling organization, data could be split up over cloud resources, data center servers, local network attached storage (NAS), and local devices. However, critical data should be tracked, and proper management and secure control of this data should be required and enforced.
Data Backup Access and Changes
The rise of ransomware and data wiper attacks makes data backups more important than ever. Access to data backups should be tightly controlled, and anyone attempting to modify or delete data backups should generate alerts or simply quarantine the device from the network to prevent widespread damage.
These alerts should even apply to legitimate deletions by authorized personnel. This will be important not only for maintaining strong security, but also for many compliance requirements that would be met by tracking verified deletion of old data.
See the Best Backup Solutions for Ransomware Protection
Significant Data Changes
Data will often be added, moved, or removed from servers or across the network. However, the volume of the data and the number of files involved will usually fall within a specific range or be limited to specific users.
For example, a company that does subtitles for feature films will need to move huge files and use a lot of data bandwidth but only for the technicians working on the subtitled videos. For this organization, videos could be restricted to a specific server and a specific transmission method, and alerts would only be generated outside of that process.
However, in a lumber company, sending huge data files should be very rare and might merit an alert because the huge file might be a data exfiltration event. Similarly, most companies would want to be alerted if a huge number of files were suddenly moved or deleted from any source.
Unusual Software and Tool Use
The larger the organization, the harder it will be to monitor all of the different software in use regionally and in what languages. Still, there will be baseline software use that can be monitored using alerts.
In a big multinational electronics manufacturer, for example, the accounting team may need to enable macros for their complex Excel spreadsheets, but the sales executives may not have any reason to do so. In this case enabling macros by users such as the sales team should trigger alerts about potential malware being activated.
Even more fundamentally, most users would not know what a command prompt is, let alone how to launch it. Many users have never heard of Net.exe or even PowerShell.
Only a small percentage of lawyers, business executives, or warehouse employees would be inconvenienced by being denied access to command prompts, PowerShell, or other dangerous programs. While these can and should be controlled by Work Groups in Active Directory, alerts should also be enabled through the EDR system to flag such unusual behavior or even automatically quarantine the endpoint.
AI-enhanced EDR uses programming to detect similar behavior, but AI can always be bolstered with hard rules that reinforce expectations. Even if the alert is applied universally across all systems and users, admins may still use these tools for legitimate purposes, and since they triggered the alarms, they will have no problem verifying that the alert can be ignored.
Also read: PowerShell Is Source of More Than a Third of Critical Security Threats
Consider Gaps in Coverage, Detection and Monitoring
When setting up EDR or any security tool, consider and verify what assumptions may be in place. For example, is there an assumption that EDR coverage is applied to all endpoints, that the EDR detects all attacks, or that the EDR is being monitored?
Gaps in Endpoint Coverage
Applying alerts and tightening security on corporate desktops and laptops doesn’t help the security team much if mobile devices and BYOD (bring your own device) devices go unsupervised. In addition, Internet of Things (IoT) and operational technology (OT) devices within the network should be accounted for and controlled.
Asset discovery should be one of the first steps in EDR installation. If the EDR, for whatever reason, cannot be installed on a class of endpoints, then other devices might want to alert the security team if that unsupervised class of devices attempts to access a protected device.
For example, is there any condition under which a security camera IP should be the source of a user login to a shared server? For most organizations, they can safely create an EDR alert that checks for unusual sources of a login or access attempt.
Gaps in Attack Detection
Be sure to also inspect the gaps in EDR solutions against categories or specific types of attack.
Check the MITRE ATT&CK evaluations for when an EDR only provides minimal data or telemetry or does not provide any information at all. The IT security team can plug the gaps by creating custom alerts to catch specific actions.
Also read: Latest MITRE Endpoint Security Results Show Some Familiar Names on Top
Gaps in Attack Monitoring
Make sure the alerts are delivered to a team that is focused and paying attention.
For example, on March 31, 2021, the Conti ransomware gang gained PC access in Ireland’s Public Healthcare and anti-malware successfully detected their use of Cobalt Strike and Mimikatz.
Unfortunately, no one responded to the warning, and their country’s healthcare system was crippled two months later. The security setup failed in two fundamental ways:
- The anti-malware was set to monitor only and not interfere.
- The anti-malware sent the alert, and the alert was ignored.
The IT team establishing the endpoint protection justifiably decided that doctors and nurses generally don’t need to deploy hacking tools. Unfortunately, they did not set up the EDR or user group to deny access, they merely set an alert.
However, many security teams suffer from alert fatigue. With a rising number of attacks and a constant shortage of qualified security personnel, many security teams find themselves working longer hours and dealing with a longer list of issues to deal with in their queues.
EDRs can be customized to help security teams avoid alert fatigue by categorizing certain actions for immediate responses. It will be much easier long-term to deal with an angry user that triggered a quarantine than to restore the entire infrastructure of an organization.
Also read: Best Antivirus Software
Consider Customizing Your EDR Solution
EDR customization will take time, effort, and probably money. While a security team may determine many possible alerts that could be added, financial limitations may limit the number of alerts and automated actions that can be realistically implemented.
However, customized defense provides an enormous advantage to a security team. Advanced warning from optimized alerts reduces attack windows. Optimized automated responses can also reduce alert fatigue and cut off attacks in process.
Short-term customization costs will need to be balanced against the potential long-term savings from a customized EDR deployment. Security teams can use risk analysis to prioritize key assets and users to prioritize alerts to implement.
As time progresses, improved budget circumstances may allow for the number of alerts or automated remediations to be increased and improved. The most important thing is to start now.
For those that choose not to customize their EDR at installation, future successful attacks may force customization. Unfortunately, it is guaranteed that the forced customization will be far more expensive than the voluntary customization.
Read next: Top Security Orchestration, Automation and Response (SOAR) Solutions
The post Why You Need to Tune EDR to Secure Your Environment appeared first on eSecurityPlanet.
]]>The post Top Data Loss Prevention (DLP) Solutions appeared first on eSecurityPlanet.
]]>Every organization has data, and some of that data is more sensitive than others. Sensitive data can include personally identifiable information (PII) that can impact user privacy. Sensitive data also includes payment and financial information that could lead to identity theft and fraud if the data is lost or stolen and winds up in the wrong hands. Other critical sources of data include intellectual property (IP) and trade secrets.
How DLP Works
DLP technology provides a mechanism to help protect against sensitive data loss—and thus could also be something of a mitigating factor when dealing with compliance agencies in the wake of a data breach. As such, DLP has become a top IT spending priority in many organizations.
By classifying data and users and identifying or blocking anomalous behavior, DLP tools give enterprises the visibility and reporting needed to protect sensitive data and satisfy compliance reporting requirements.
Key DLP Trends
A number of trends are all driving an increase in DLP adoption and strategic importance – and in some cases changing how DLP is delivered and deployed.
The Great Resignation
Businesses are currently struggling with the number of workers leaving for alternate employers. Often leaving with them is the sensitive data that fuels the business. Whether intellectual property or regulated data, employee flight creates a situation where data loss or theft is more prevalent and more costly.
Hybrid Work Model
Prior to the COVID-19 pandemic, the common model was to have the vast majority of employees within the office and in a controlled technology environment. That model has flipped in favor of remote work and won’t likely ever fully return to the way it was. More workers in more locations means more sensitive data in more locations – and more potential points of data leakage.
Cybersecurity Talent Shortage
Hiring, training, and retaining the staff needed to effectively run an information security program can be a challenge for any size business given the cybersecurity talent shortage. Relying on a third party like a managed security service provider (MSSP) to be your eyes and ears delivers the simplicity and efficacy needed for an effective data protection program. Like other security defenses, DLP is also increasingly being offered as a service.
Cloud Security Platform Delivery
The cloud delivery model has proven itself to be efficient and often more secure than what companies can deliver on-premises relying on their own resources. Cloud-delivered DLP, or DLP as a Service, eliminates the complexity and overhead that can burden IT teams.
Platform Consolidation
Organizations rely on an ever-increasing stack of security vendors. This increase in vendors leads to excess complexity – and often reduced information security. Consolidating internal and external data protection programs with a single solution delivers a simplified view that analysts can use to achieve their main goal, which is to protect sensitive data.
Data Explosion
IDC estimates that by 2025, 463 exabytes of data will be created every single day. Information security teams have a rapidly expanding challenge to find, understand, and protect all that data. Whether it be on the endpoint, in the cloud, or somewhere in between, data protection programs are a critical piece of the solution to stop data loss or theft.
Profiling
Customers and companies are moving away from the registration model. Maintaining spreadsheets with millions of rows to identify PII is too difficult to maintain and secure, especially as customers are moving to a profiling mode of operation.
Also read: Top GRC Tools & Software
DLP capabilities
There are a number of key capabilities that the top DLP products and services support.
- Cloud: The DLP market, much like the broader IT market, has been shaped in recent years by the rise of the cloud. No longer is enterprise data confined to on-premises deployment. DLP solutions therefore must monitor sensitive data in the cloud.
- Privacy compliance: With GDPR, CCPA, and other data privacy regulations on the rise, DLP has become a useful tool for helping organizations protect customer privacy.
- Data labeling: DLP tools have long enabled users to self-assess and identify what types of data should be protected.
- Machine learning: Among the latest advances in DLP is machine learning capabilities that automatically identify potentially sensitive information, so it can be protected.
How to choose a DLP solution
When choosing a DLP technology or services, there are several key considerations organizations must take into account, including:
- Scope: Where is the data that needs to be protected, and does the solution you’re looking at have full visibility into those deployments?
- Compliance: If the DLP service is being used to help enable regulatory compliance, be aware of integration with GRC (governance, risk, and compliance) tools.
- Reporting: It’s important for some organizations to have visibility and reporting into what data is protected and how it is being accessed, particularly for compliance purposes.
8 Top DLP Solutions
Jump ahead to:
After reviewing the market for DLP solutions, here are eSecurity Planet’s top picks for DLP.
Digital Guardian

The Digital Guardian Data Protection Platform by HelpSystems, powered by AWS, performs on traditional endpoints, across the corporate network, and on cloud applications, making it easier to see and block threats to sensitive information.
Cloud-delivered means simplified deployment, cross platform coverage for no gaps, and flexible controls to stop risky behavior. And available either as a software-as-a-service (SaaS) or managed service deployment, Digital Guardian gives deployment flexibility.
Key Differentiators
- Digital Guardian supports both a use case-based approach (known data types or user groups) or a data risk discovery approach (identifying unknown use cases).
- Users can gain visibility into their data by seeing where sensitive data is located, how it flows in the organization, and where it is put at risk, all without policies.
- Users can benefit from rapid deployment, reduced overhead, and instant scalability.
- DLP coverage is available for all endpoints, browsers, and apps.
- Controls are able to align data protection programs with business needs. These controls include log, alert, prompt, block, and encryption.
- The platform can be deployed as a fully managed security service program (MSSP) with a 24/7 global analyst team.
- Users can discover, classify, and protect data throughout the extended enterprise via an endpoint agent that can be installed on Windows, Mac, or Linux machines or a network appliance, either physical or virtual.
- All data-centric events collected are reported up to the Analytics & Reporting Cloud (ARC). This web-based console, powered by AWS, correlates and analyzes system, user, and data events from endpoint agents and network appliances to provide the visibility and context to identify and remediate insider and outsider threats.
- Digital Guardian provides intellectual property and regulated data protection.
Fidelis

Fidelis Network gives a clear picture of bi-directional, encrypted traffic along with its context, all in one place. Deep Session Inspection technology extracts metadata and monitors 300+ different attributes.
In addition, Fidelis can retrospectively detect and investigate threats and stop sessions that violate policies with details about who is sending and receiving data and what type of data is being sent. As an integrated feature of a larger security stack, Fidelis DLP provides increased data visibility, protects intellectual property, and ensures compliance.
Key Differentiators
- Fidelis offers visibility into all ports and protocols.
- Users can analyze encrypted traffic and detect anomalies within that traffic.
- Fidelis enables users to inspect objects, text, and attributes buried deep in layers of applications, archives, or compression.
- Custom file decoders extract text and attributes from PDFs, MS Office files, etc.
- Decrypt for deeper analysis to detect malware on the wire, encrypted attacker communications, data theft, and insider threat; inspect; and re-encrypt traffic without slowing down network traffic.
- Understand what’s moving across the network, how it’s moving, and who is seeing it.
- Prevent data theft or unauthorized sharing.
- Fidelis provides a flexible and customizable policy engine.
- A prevention capability is available even in real-time sensors, including prevention by hash, using partial file matching.
- The platform offers an extensive list of profiling in addition to data registration processes. By using profiling, Fidelis customers can sufficiently describe the data rather than painstakingly collecting the data.
- PII profiling is covered by a multivariate data analysis technique that detects violating data without creating huge lists.
- Email handling with bi-directional quarantine blocks threats coming in and sensitive data going out.
Check Point

Check Point Data Loss Prevention (DLP) combines technology and processes to move businesses from passive detection to active DLP.
Data classification integrates user, content and process information to make accurate decisions, while UserCheck empowers users to remediate incidents in real time. Check Point’s network-based DLP solution frees IT and security personnel from incident handling and educates users on proper data handling policies—protecting sensitive corporate information from both intentional and unintentional loss.
Key Differentiators
- Deploy predefined policy in monitor mode in a few minutes.
- Track and control the movement of sensitive data in the organization.
- Stay compliant with regulations and industry standards.
- Educate users on proper data handling policy.
- Check Point has two options for securing data: Content Awareness and a full-featured DLP.
- Choose from 60+ or 700+ predefined data content types for PII, PCI, HIPAA, and more.
- Customize predefined data types or create new ones as needed.
- Customizable, multi-language user notifications are available.
- Inspect and control SMTP, FTP, HTTPS webmail, and Exchange traffic.
- Harmony Cloud Email Security secures Office 365 and Google Workspace applications.
- DLP is integrated directly into Check Point security gateways and firewalls, and they also check SSL/TLS encrypted data to prevent data loss.
Clumio

Clumio Protect & Discover offers backup and recovery for AWS, VMC, and Microsoft 365. It simplifies and automates AWS data protection for Amazon S3, EC2, EBS, and RDS; SQL Server on EC2; DynamoDB; VMware Cloud on AWS; and Microsoft 365.
Key Differentiators
- Ransomware protection is offered with air-gap backups that are immutable and end-to-end encrypted.
- Meet compliance requirements with global policies and protection groups.
- Restore data in minutes with granular, one-click recovery to reduce RTO (recovery time objectives).
- Get real-time visibility and recommendations to reduce data risks and stay on top of AWS backup spend.
- Validate defined RPO (recovery point objectives) across all accounts to ensure compliance on recovery points.
- With all backup and recovery management and optimization in one easy-to-use place, IT teams can spend less time on AWS backup and focus more on strategic initiatives.
- Backups in Clumio SecureVault are stored outside of AWS accounts by default so no additional actions are needed to protect backups from malicious attacks.
- Clumio backups are immutable; they cannot be changed, and there is no delete button.
- Centralized dashboards and reports plus calendar view, global search, and browse functionalities make it easy to see data and customize protection.
- Lifecycle management rules allow users to automate and streamline backup plans.
Trellix

Trellix – formed from the merger of McAfee Enterprise and FireEye – remains tightly coupled with its former cloud business, Skyhigh Security, in the area of DLP. Trellix Data and User Security provides DLP features such as real-time visibility and security of data, protecting against data leakage through dynamic access adjustment, intelligent threat identification, and automated response.
Key Differentiators
- The platform protects data everywhere.
- Trellix provides continuous data security from any device with multi-vector DLP.
- Data is deployed and updated with a zero-trust approach.
- Applies AI (artificial intelligence)/ML (machine learning) insights at scale to identify anomalous user behavior (UEBA), while also automating and simplifying data access policy orchestration.
- Trellix Data and User Security adapts across the enterprise.
- Threat research is combined with intelligent automation to adapt to new risks, allowing you to flexibly address ever-growing data security needs.
Code42

Code42 plays in the DLP market yet believes DLP isn’t the answer. Instead, it advocates a risk-based approach via its Incydr solution. It monitors all the places data lives to identify when files move outside the trusted environment.
Key Differentiators
- Code42 prioritizes the highest risk employee activity using 60+ contextual Incydr Risk Indicators (IRIs).
- Watchlists allow you to programmatically protect data when files are most at risk, such as during employee departure.
- A range of controls are available to contain, resolve, and educate on events via Incydr Flows and SOAR.
- The platform acts as a cross-platform endpoint agent for Windows, Mac, and Linux.
- Incydr Exfiltration Detectors are available for cloud (OneDrive, Google Drive, Box), email (Office365 and Gmail), and Salesforce.
- Tailored views identify data exposure, training gaps, and corporate policy.non-compliance as well as measure program performance company-wide.
- Prioritizes the risks that need immediate attention through contextual risk scoring based on file, vector, and user characteristics and behaviors.
- Automates management workflows and get focused visibility into file activity for a subset of users who are more likely to put data at risk, such as departing employees.
- Investigates event details and custom query a comprehensive, cloud-based index of activity metadata without putting strain on employee devices.
- Documents and retains investigation evidence for malicious and high-impact incidents, and creates reports for key stakeholders.
Forcepoint

Forcepoint DLP offers tools to manage global policies across every major channel, whether it is an endpoint, network, cloud, web, or email. Predefined templates, policies, and streamlined incident management, among other features, enable organizations to address risk by bringing visibility and control where people work and data resides.
Key Differentiators
- Meet and maintain compliance with more than 1,500 predefined templates, policies, and classifiers applicable to the regulatory demands of 83 countries.
- Locate and remediate regulated data with network, cloud, and endpoint discovery.
- Take advantage of central control and consistent policies across all channels.
- Coach employees to make smart decisions, using messages that guide user actions, educate employees on policy, and validate user intent when interacting with critical data.
- Securely collaborate using policy-based auto-encryption that protects data as it moves outside the organization.
- Automate data labeling and classification by integrating with third-party data classification solutions (e.g., Microsoft Azure Information Protection, Boldon James).
- Identify data at rest, in motion, and in use with Forcepoint DLP.
Proofpoint

Proofpoint Endpoint DLP takes a people-centric approach to protecting data. It provides integrated content awareness and behavioral and threat awareness, which gives granular visibility into user interactions with sensitive data. In addition, Proofpoint Endpoint DLP offers the ability to detect, prevent, and respond to data loss incidents in real time.
Key Differentiators
- Simplifies response for data-loss incidents and out-of-policy violations.
- Identifies risky user behavior and sensitive data interaction.
- Detects and prevents insider-led security incidents and data loss from endpoints.
- Proofpoint Endpoint DLP extends the capabilities of the Proofpoint Information and Cloud Security platform to the endpoint.
- Visibility and context into user and data activity is available.
- Proofpoint Endpoint DLP simplifies deployment with a pure SaaS back end and lightweight endpoint agent architecture.
- The platform collects telemetry on user interactions with data.
Read next: Best Incident Response Tools and Software
The post Top Data Loss Prevention (DLP) Solutions appeared first on eSecurityPlanet.
]]>

