Identity and Access Management (IAM) once helped IT departments in large enterprises to manage employees in Active Directory. In a modern IT environment IAM plays a far more critical role in authorizing geographically dispersed workforces as they connect to internal resources, cloud resources, and especially software-as-a-service (SaaS) applications.
IT teams can no longer easily manage individual user rights and permissions with the rapid increase in SaaS applications and remote work. IAM offloads the burden of individual access management and automates the onboarding and offboarding processes as well.
To pick the best software for IAM needs becomes complicated as corporate needs surpass the traditional workforce requirements to encompass developers, customers, and even access from other applications. Some organizations require a dedicated IAM solution while others may only need a simler IAM tool within a portfolio of other security products. Jump to our top list for each of those:
Many more IAM providers exist than can be covered in this article, but we will highlight key providers, their features, pros, cons, and pricing (when available).
Best IAM Software Solutions
- CyberArk – Security-Focused IAM
- JumpCloud – Small Business Friendly IAM
- Okta & Auth0 – IAM Category Leader
- OneLogin – Education-Friendly IAM
- Ping Identity – IAM Category Challenger
- CyberRes NetIQ – For In-House IAM Installations
- IBM – Subtle IAM Security
- ManageEngine – In-House IAM + PAM
- Microsoft – Broadest IAM Coverage
- Oracle – For Enterprise Multi-Cloud IAM
After covering individual tools, this article will cover IAM Service Providers, How the Top IAM Solutions Were Selected as well as an Overview of IAM Trends.
1 Twingate
Twingate helps fast-growing companies easily implement a Zero Trust secure access solution without compromising security, usability, or performance. We believe that “Work from Anywhere” should just work. Twingate’s secure access platform replaces legacy VPNs with a modern Identity-First Networking solution that combines enterprise-grade security with a consumer-grade user experience. It can be set up in less than 15 minutes and integrates with all major cloud providers and identity providers.
Top Identity Access Management Solutions at a Glance
This chart covers some of the most basic features of IAM tools, as well as some less common capabilities like identity orchestration.
| Multi-factor authentication | Privilege access management | Identity orchestration / workflows | Secrets management | |
| CyberArk | ✅ | ✅ | ✅ | ✅ |
| JumpCloud | ✅ | 🟨 | 🟨 | ✅ |
| Okta | ✅ | ✅ | ✅ | 🟨 |
| OneLogin | ✅ | ➕ | ➕ | 🟥 |
| Ping Identity | ✅ | 🟨 | ✅ | 🟥 |
| CyberRes NetIQ | 🟨 | ✅ | 🟥 | 🟥 |
| IBM | ✅ | 🟨 | 🟥 | ✅ |
| ManageEngine | ✅ | ✅ | ✅ | 🟥 |
| Microsoft | ✅ | ✅ | ✅ | 🟨 |
| Oracle | ✅ | ✅ | 🟨 | ➕ |
✅ = Has feature 🟥= Not offered 🟨 = Unclear ➕= Available from vendor in another solution
Best Dedicated Identity and Access (IAM) Software
Organizations can deploy different options to encompass the capabilities of identity and access management, but sometimes the best option is to acquire a dedicated solution — such as the five IAM-centric tools in this section. These dedicated identity and access management tools integrate with human resources software and connect to an organization’s critical assets and applications on-prem, in the cloud, and SaaS tools.
CyberArk – Security-Focused IAM
CyberArk looks at identity as the basis for a security strategy and offers a portfolio of tools for identity management, privileged access, secrets management, endpoint privilege security, cloud privilege security, and both workforce and customer access. Behavior analytics set a baseline for users and can trigger alerts and access changes when anomalous behavior is detected.
Features
- Lets users in while using artificial intelligence (AI) to help keep threats out
- Continuously monitors behavioral signals to make sure users are who they say they are
- Single sign-on and multi-factor authentication
- Consolidate key security technologies and simplify policy enforcement
- A privilege-centric approach to securing identities
- Option for password management
Pros
- Great tool for those that want to easily add privileged and secrets management
- Self-hosting options for tools
Cons
- Opaque pricing and licensing makes it unclear what licenses may be required to match the capabilities of other IAM products or other pricing details (Per user or per app? Monthly or annual billing? etc.)
- Organizations that need only IAM features may not benefit from additional security features and options
Price
Cyberark does not list pricing on their website. Instead, the site encourages interested parties to start a free trial, contact the company for a quote, or reach out to resale partners for more information.
JumpCloud – Small Business Friendly IAM
The cloud-native JumpCloud provides IAM and options for device and patch management. The tool has options to implement zero-trust policies, use Cloud LDAP to manage users, and to deploy Cloud RADIUS to issue certificates to devices as one form of multi-factor authentication.
Features
- Centralized identity control and lifecycle management through the Cloud Directory tool
- Cloud-based LDAP and RADIUS services
- MFA, SSO, conditional access, and password management
- HR system integration
- API services for custom workflow development
- Incorporates mobile device management (MDM) and management for Windows, macOS, and linux endpoints.
- Provides Patch Management and device intelligence
Pros
- Simplified trouble-shooting and compliance monitoring of user activity
- Pre-built application catalog
Cons
- Changes can be easy to make incorrectly or recklessly without training
- Incorrect connections can overwrite user passwords
- Strictly a cloud-based tool
- Requires powershell module to make bulk changes
Price
JumpCloud offers a free version for up to 10 users and 10 devices. Paid versions require the Cloud Directory tool and are priced per user per month. Monthly billing is available but a discount is applied for annual billing.
| Service | Annual Price | Monthly Price |
|---|---|---|
| Cloud Directory base | $3 | $2 |
| Cloud Directory a la carte options | ||
| MFA, SSO, user lifecycle management, etc. | $3 | $4 |
| Device management | $5 | $6 |
| 24×7 support | $2 | $3 |
| SSO package that bundles MFA, SSO, user lifecycle management | $7 | $8.50 |
| SSO package a la carte options | ||
| Device management | $3 | $5 |
| Password manager or cloud insights (AWS users) | $4 | $4 |
| 24×7 support | $2 | $3 |
| Core Directory Package that adds Cloud LDAP, RADIUS and Directory insights | $11 | $13 |
| Core Directory Package a la carte options | ||
| Password manager or cloud insights (AWS users) | $4 | $4 |
| 24×7 support | $2 | $3 |
| JumpCloud Platform bundle that adds device management | $15 | $17 |
| JumpCloud Platform a la carte options | ||
| Patch management, password manager, or cloud insights (AWS users) | $4 | $4 |
| 24×7 support | $2 | $3 |
| PlatformPlus that adds support and zero trust options (conditional access policies, device trust, and network trust) | $18 | $20 |
| PlatformPlus a la carte options | ||
| 24×7 support | $2 | $3 |
| Patch management, password manager, or cloud insights (AWS users) | $4 | $4 |
JumpCloud offers professional services to help with implementation, migration or technical account management. JumpCloud also offers special pricing and discounts for MSP partners, educational institutions, and Non-profit organizations.
Okta & Auth0 – IAM Category Leader
Okta has long been a leader in access management, authentication and single sign-on. With a simple and easy-to-manage SaaS-based approach, Okta offers IAM solutions that enable zero trust principles with reduced complexity.
Okta recently acquired Auth0 to cement their position as the category leader and offer developers coded IAM solutions for customer IAM and applications. Okta is also an IAM specialist, independent of other major technology companies and publicly traded on the NASDAQ.
Features
- Securely manage identity for apps and multi-cloud environments
- Automated lifecycle management for user provisioning and deprovisioning.
- Secure password-less authentication options
- Options for multi-factor authentication (MFA) and single-sign-on (SSO)
- Privileged access management features
- Tailor Okta using no-code, low-code, or pro-code options
- Connect to third-party apps and systems to enhance security and user experience
- Directories securely store users and attributes at scale
- Okta Insights aggregates, analyzes, and disseminates data from the IAM tool
- Identity Engine offers customization of authorization, authentication, and registration
Pros
- More than 7,000 established integrations
- Options for managing identities for the workforce or customers
- Developers can use the established Auth0 IAM solution
- Recognized as a market leader by Gartner, Forrester, and G2
- 99.99% availability; built with self-healing nodes for greater stability
- Centralized admin and a single directory to manage users, groups, apps, devices, and policies
- Unified IAM and governance solution
- Advanced adaptive SSO and MFA capabilities for enhanced security
- Auth0 offers 14 pre-built software design kits (SDKs) with language-specific libraries
Cons
- SaaS app is not very customizable
- Cloud-based application, no on-premises option (other than agents for integration and connections)
- Requires multiple tools to be licensed for full identity and access management capabilities
- Contract minimums will be unsuitable for the smallest organizations
Price
The pricing for Okta can be complex because of the many options Okta offers.
Workforce IAM Options require a minimum $1,500 annual contract and offer volume discounts for enterprise customers with more than 5,000 users. Okta offers various tiers based upon the desired features and are priced per user per month.
| Price (USD) | Option |
|---|---|
| $2 | Single-sign-on (SSO) |
| $5 | Adaptive SSO |
| $3 | MFA |
| $6 | Adaptive MFA |
| $2 | Universal Directory |
| $4 | Lifecycle management |
| $2 | API Access management |
| $15 per server per month | Advanced server access |
| $3 | Access gateway |
| Workflows | |
| no cost | Up to 5 flows |
| $4 | Light – up to 50 flows |
| $5 | Medium up to 150 flows |
| $6 | Unlimited flows |
| Identity Governance | |
| $9 | Light – up to 50 flows |
| $10 | Medium – up to 150 flows |
| $11 | Unlimited flows |
Customer IAM Options support and secure customer interactions are acquired through the Auth0 app for developers. Auth0 is free for up to 7,000 users with unlimited logins. Paid categories depend upon the use case and the number of active users. Custom quotes for complex use cases and discounts for non-profit organizations are also available.
| Customer IAM Plan | Price | Note |
|---|---|---|
| B2B Essential | $130 / month | Up to 50 organizations |
| B2B Professional | $800 / month | Up to 100 organizations |
| B2C Essentials | $23 / month | |
| B2C Professional | $240 / month | Adds MFA, external database support, admin roles, and consolidated user stores |
Customized enterprise plans also are available with custom connections and user tiers, advanced deployment options, enterprise add-ons, and no admin or action limits.
OneLogin – Education-Friendly IAM
OneLogin, a division of One Identity which is owned by Quest Software, provides a dedicated identity and access management solution for both the workforce and customers. OneLogin also provides support to developers that want to integrate IAM capabilities into their own applications.
OneLogin offers an unusual option to place an application on the desktop of an endpoint computer. This desktop app launches with the login password and enables a completely controlled environment for all connected applications and users and may not need to use any other passwords.
Features
- Consistent experience with single-click access to SaaS and on-premises applications from any device
- Manage access for all your apps from a centralized platform with a single UI
- Offers Federation, single sign-on, and integrates with OneLogin SmartFactor Authentication
- Balances usability and security with adaptive authentication for dynamic, multi-factor authentication (MFA)
- Advanced directory synchronizes users across multiple directories such as Workday, Active Directory, G Suite, LDAP, etc.
- Can control HR data and streamline on- and off-boarding of employees through automation
- Options to unify and secure remote access through on-prem windows servers and desktops
- Option for a OneLogin desktop environment where the device login acts as the credentials for all apps
- OneLogin offers a sandbox feature to test configurations
Pros
- More than 6,000 integrations
- Customer IAM can integrate with social media logins
- Effective alerts and reports of unauthorized login attempts
- Integrates with Student Information System (SIS) platforms popular for organizations in the education market
Cons
- Adding users to multiple roles can lead to multiple logins for the same app through each role
- Prices can add up with multiple a-la-carte options
Price
OneLogin offers a flexible array of offerings for their IAM products, but does not publish their pricing for Customer IAM or Developer licensing. OneLogin offers a self-service portal for technically savvy Small Businesses of less than 50 users, or provides references to certified MSP partners that can assist with deployment, provide day-to-day management, and offer volume pricing discounts.
- Workforce IAM Bundle Prices / user / month
- $4 Advanced bundle provides SSO, advanced directory, MFA, and policy-driven security
- $8 Professional bundle adds identity lifecycle management, and HR-Driven identity.
- Workforce IAM a-la-carte pricing / user / month
- $2 SSO
- $2 Advanced Direcotry
- $2 MFA
- $5 SmartFactor Authentication
- $4 Desktop
- $4 Identity Lifecycle Management
- $2 HR-Driven Identity
- $4 RADIUS
- $2 Workflows
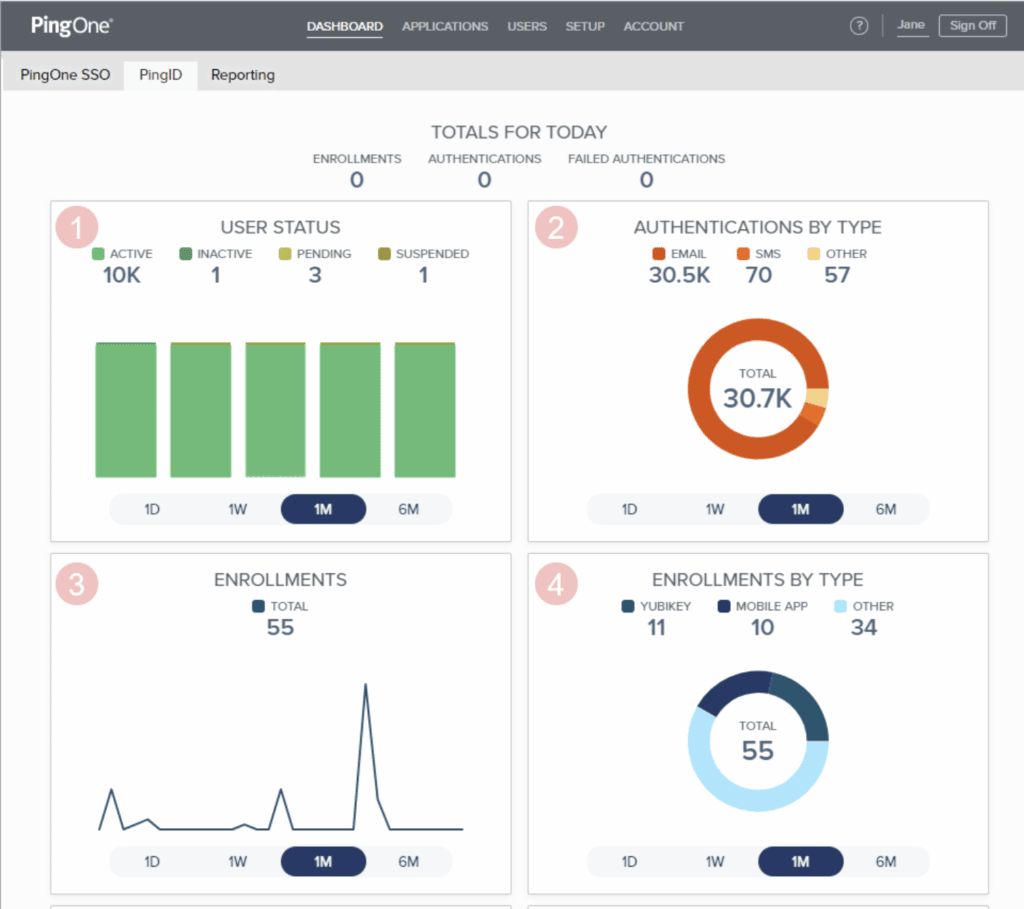
Ping Identity – IAM Category Challenger
Another publicly traded IAM pure-play on the NASDAQ, Ping Identity offers a range of identity and access management solutions that may be purchased separately. Ping offers IAM to cover both the workforce and the customers of clients as well as support for developers to add IAM features to websites and applications. Ping Identity lags behind Okta in revenue, but as of 2018, all 12 of the largest banks in the US used the Ping Intelligent Identity Platform.
Features
- Administer IAM across any cloud or user to manage IAM at scale.
- Integrate throughout a hybrid IT environment
- Confirm the identity of users and detect potential fraud
- Deliver consistent single sign-ons (SSOs) and multi-factor authentication (MFA) with options for dynamic authorization
- Protect access to resources, data and sensitive actions
- Continuously monitor risk signals and API traffic
- No-code drag & drop workflows, pre-built templates, and easy A/B tests to test identity orchestration for different workflows
Pros
- 99.99% uptime
- 100+ pre-built integrations
- Detects threats and anomalous or risky behavior
- Also available as a
- Dedicated tenant option managed and hosted by Ping for customers that require data isolation
- Cloud-ready containers for on-premise or private cloud deployment of some capabilities
Cons
- Some customers complain of complex role management and entitlement creation
- Requires multiple tools to be licensed for full identity and access management capabilities
- Contract minimums will be unsuitable for smaller organizations
Price
Ping offers a free 30-day trial of their product and prices their PingOne Workforce solution based on users per month based on an annual contract with a minimum of 5,000 users.
- $3 Essential includes identity orchestration engine, SSO, directory, employee dock
- $6 Plus adds adaptive MFA, integration with Microsoft, passwordless authentication, inbound provisioning, and LDAP
- Premium requires a custom quote but adds advanced authentication, access security, delegated administration, VPN and remote access integration, API access control, and more.
PingOne for Customers is priced annually in three tiers:
- $20k Essential includes identity orchestration engine, SSO,authentication policies, customizable registration/sign-on, unified customer profile, self-service preference management, secure user management, connections to apps with open standards, RESTful APIs, and a unified administration portal
- $40k Plus adds adaptive MFA, embedded MFA for mobile apps, customer device management, transaction approvals, API access management, LDAP, and passwordless authentication
Premium requires a custom quote but adds support for extreme demand spikes, connections to multiple data stores, and more customization.
Best IAM Tools in a Portfolio
Sometimes, identity and access management is only one of the problems an IT team needs to solve. In these cases, working with a vendor with a broader variety of tools can be advantageous because the IAM tool should automatically integrate with the other tools needed by the organization. The five vendors in this category offer a much broader suite of tools that an organization will include in its evaluation of the suitability of the IAM solution.
CyberRes NetIQ – For In-House IAM Installations
CyberRes, by Micro Focus, provides a suite of NetIQ tools for Identity and Access management. Its adaptive identity-centric approach offers an integrated platform for identity, access, and privilege management that integrates with other security and privacy tools in the collection.
Features
- The NetIQ Risk Service consumes contextual and behavior risk metrics to adapt the user authentication experience
- Tunes session authorization levels as needed to protect sensitive resources
- Provides visibility and control of privileged user activities to deliver actionable security intelligence to address evolving threats
- Allows configuration policy management and enforcement across critical systems on-premises and in the cloud across Unix, Linux, Windows, Azure, O365, and non-domain joined services
- Edit, test, review and compare changes before implementing environmental changes to prevent security gaps
- Automate and streamline access requests, access certification, identity lifecycle management, provisioning, and compliance reporting
- Policy-based remediation to automatically secure locations or lock down locations
- Installs within the organization’s architecture (local data centers or private cloud)
Pros
- Easy, centralized management of self-service access requests and approvals
- Continuous governance to detect high-risk changes
- Local installations provide full control to the organization
Cons
- Performance and uptime depends upon the organization’s infrastructure and resources
- Requires more management, support, and infrastructure costs than hosted solutions.
Price
MicroFocus offers free trials of their software but neither publishes prices on their website nor notes the nature of the licenses (perpetual, annual, etc.).
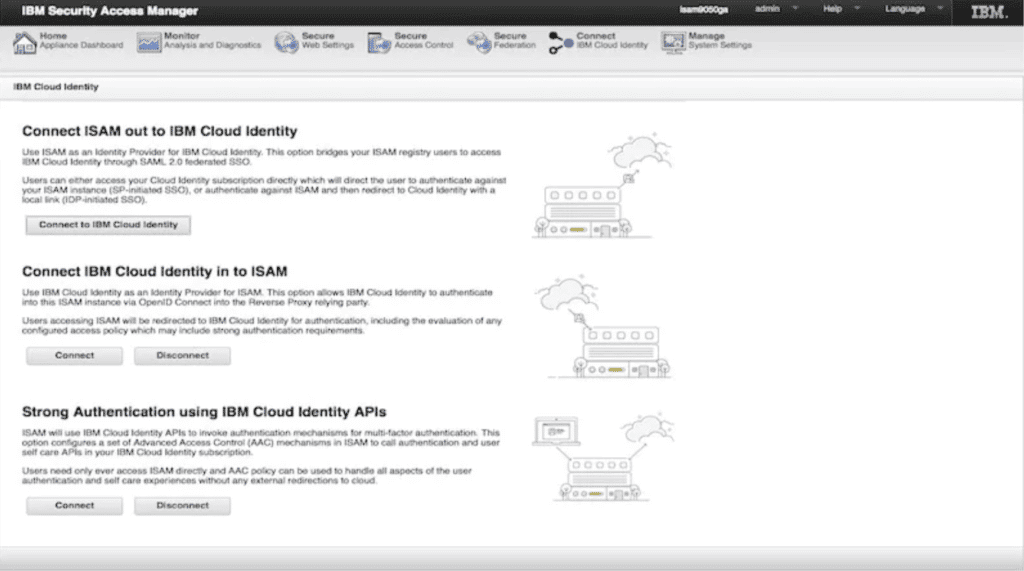
IBM – Subtle IAM Security
IBM Security Verify provides identity and access management solutions as part of a broader portfolio of security products. IBM’s IAM portfolio also extends into the related technology categories of governance and privileged access management (PAM).
IBM designs Security Verify to be invisible to users and operate in the background. This approach provides IAM and security with reduced user disruption.
Features
- Discreetly verifies user identities when they log in and throughout the session
- Uses AI to uncover outliers and dangerous combinations of entitlements
- Enables access to resources and applications, whether in the cloud, on-premises, or in a hybrid cloud
- Centrally manages and automates access certifications, on- and off-boarding, and separation of duties violation detection
- Provides single sign-on and risk-based multifactor authentication
- Admins can securely grant access rights and entitlements
- Provision, audit and report on user access and activity
- Allows self-service options for access request and password reset
Pros
- Both cloud-based and on-prem solutions available
- Heavy emphasis on security and governance reporting
- Integrates tightly into the IBM ecosystem
- Role-based IAM
- Can connect with local applications and services such as virtual private network (VPN)
- Detects and monitors the passwords for high-access accounts
Cons
- Best suited for high-volume enterprise customers
- Small businesses will not need many features and tools
- Not known for a large number of app integrations
- On-prem management requires much more IT labor than SaaS solutions
- Customers complain that the interface does not work as well on mobile
Price
IBM offers Security Verify for both workforce IAM and customer IAM (CIAM) with both solutions also available as turnkey consulting and managed services. IBM sells through business partners and also quotes prices through their internal representatives.
IBM provides a cost calculator on their website and sells licenses in one, two, and three-year durations. Costs will vary depending upon the modules licensed. Published examples of pricing include:
- IBM Website: Example costs for 5,000 users (workforce license)
- $1.71 / user / month SSO
- $1.71 / user / month MFA
- $1.71 / user / month adaptive access
- $2.01 / user / month lifecycle and provisioning
- $2.13 / user / month identity analytics
- AWS Marketplace: Example 12 month contract
- $15,000 / year / 100 users for Verify Workforce
- $12,000 / year / 10k consumer users for Verify Consumer
Prices for turnkey consulting and managed services are not published.
ManageEngine AD360 – In-House IAM + PAM
ManageEngine’s portfolio of tools includes several related to identity and access management, but the key tool is ManageEngine AD360. Other tools can add capabilities for privileged management, auditing, active directory management, and key management.
Features
- Automated identity lifecycle management
- Adaptive MFA and secure SSO
- Approval-based workflows
- Identity threat protection
- AI-powered behavior analytics
Pros
- Local installations provide full control to the organization
- Quick and easy to install and implement
- Bundled pricing includes many different capabilities beyond IAM
Cons
- Performance and uptime depends upon the organization’s infrastructure and resources
- Requires more management, support, and infrastructure costs than hosted solutions.
- Requires multiple tool installations to match capabilities of IAM-dedicated tools
- Companies may not need the non-IAM capabilities that come with the AD360 bundle.
Price
ManageEngine provides a 60-day free trial for AD360 and a price calculator to estimate the licensing costs. Customers can choose between the standard or the professional edition and prices include annual maintenance and support fees.
Minimum prices are $2,870 for Standard and $5,020 for Professional and covers licenses for:
- ADManager Plus – 1 domain, 2 help desk technicians
- ADAudit Plus – 2 domain controllers, 2 file servers, 5 member servers, up to 100 workstations
- ADSelfService Plus – Up to 500 users
Other add ons, onboarding, implementation, and training are also available.
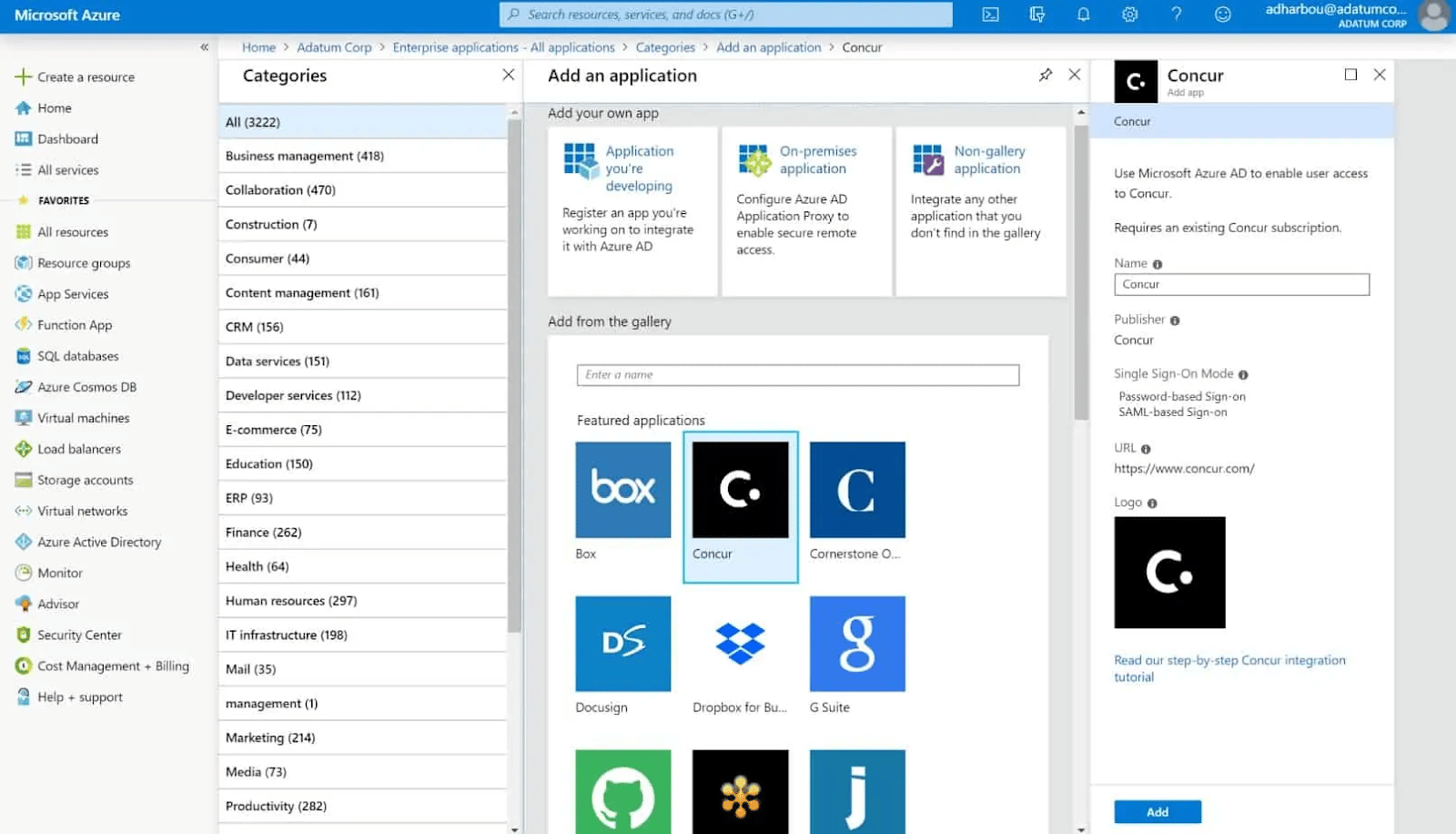
Microsoft – Broadest IAM Coverage
Microsoft’s Active Directory provides the foundation for identity management for many organizations around the world, but does not reach outside of local networks. To embrace the expanded needs for modern IAM, Microsoft offers a collection of tools, called Microsoft Entra, that can be used to implement identity and access management for multi-cloud and multi-network needs.
Launched in May, 2022, the Entra suite of tools now also encompasses Azure Active Directory so that it covers the broadest range of IAM needs when used together. However, some tools only currently exist in preview mode and have not been released commercially.
Features
- Azure Active Directory
- Centralized, cloud-based, unified identity management
- Simplified identity governance for users and admins
- Fast, easy sign-in experience across a multicloud environment
- Secure access through strong authentication policies and risk-based adaptive access policies.
- Options for SSO, MFA, passwordless, and conditional access
- Incorporates external identities
- Automates and simplifies access lifecycle (on- and off-boarding)
- Embedded privileged access management
- Entra Identity Governance:
- Govern access between resources, users, and apps
- Set up requirements for recurring reviews of users, group membership, and access
- Automate employee, supplier, or partner access to apps and services both in the cloud and on-prem.
- Can delegate day-to-day resource access requests to business groups
- Entra Permissions Management:
- Unified cloud access policies and infrastructure entitlement management
- Discovers identities accessing cloud platforms
- Automates the principle of least privilege
- Continuous permissions monitoring
- Entra Verified ID:
- Verifies and validates identity information and credentials
- Self-service account recovery
- Provides digital integration of background checks
- Entra Workload Identities:
- Secures identities for apps and workloads for zero-trust
- Detects compromised workload identities
- Simplified workload lifecycle management
Pros
- From one of the most trusted brands in IT and security – Microsoft
- The broadest perspective on what IAM should encompass to encompass human identity verification (Entra Verified ID) and treating apps and workloads as users to be verified (Entra Workload Identities)
- Basic identity management is included with other Microsoft subscriptions
- AAD already manages over 1 billion identities
Cons
- Requires multiple tools to achieve basic IAM
- The full suite of tools will be unnecessary for many users
- Too new to know how well it works compared to competition
- May be overwhelming for inexperienced IAM professionals
- Integrations may require significant trouble-shooting
Price
Pricing is not yet available for all tools in the suite, but some are also included with other Microsoft Office 365 subscriptions. Prices are quoted on a per month basis.
- Azure Active Directory (AAD) – Free version is bundled with the commercial online service such as Azure, Dynamics 365, etc.
- Includes cloud authentication, AD federated services, SSO, MFA, role based access control, user/group management, directory synchronization, passwordless access, automated user provisioning to apps, and limited end-user self-service.
- AAD Free with a customizable user sign-in page comes free with some Office 365 subscription levels.
- $6 / user AAD Premium P1 is included Microsoft 365 E3 or for purchase
- Adds group assignments to applications, cloud app discovery, application proxies, conditional access, SharePoint limited access, session lifetime management, custom security attributes, advanced group management, global password protection and management, Microsoft Identity Manager client access license, automated group provisioning to apps, and more.
- $9 / user AAD Premium P2 is included with Microsoft 365 E5 or for purchase
- Adds identity protection, access certifications, entitlement management, privileged identity management, and more
- $10.40 / resource for Entra Permissions Management
- $3 / workload for Entra Workload Identities Premium
Oracle – For Enterprise Multi-Cloud IAM
Oracle’s Cloud Infrastructure Identity and Access Management and Access Governance tools manage identity and access across a variety of cloud and on-premise applications and devices. The context-aware access products integrate with a wide range of applications, servers and systems, including custom applications.
Features
- IAM services can be self-managed, co-managed in the cloud, or fully managed via SaaS
- Cloud-native enterprise access management that supports heterogeneous and multi-cloud needs
- Governance features provide both a software delivered/self-managed model for managing on-premises and cloud resident identities, as well as running as microservices
- 33 global data centers provide the capability, scalability, and flexibility to manage access and governance needs
- Oracle embeds OCI IAM capabilities into its Fusion Application Cloud services to simplify the provisioning and role management
- Blends with existing cloud frameworks from Azure, AWS, Google and others
- Automates user lifecycle management across all resources
Pros
- Admins assign apps to groups and users to groups so that users can easily self-provision available apps without an IT burden
- Enables an identity-based perimeter for Zero Trust
- Can provide customer-oriented IAM
- Integrates with social media platforms
- Customizable user interfaces
- Best for large enterprise customers
Cons
- The complex architecture can be very difficult to learn
- Does not support many third-party integration tools
- Pricing can be complex and confusing because it is unclear which licenses grant which capabilities or if multiple licenses may be needed
Price
Oracle posts basic pricing on their website, but customers can also consider going through partner resellers for possible discounts. Pricing is listed per user per month with possible charges for tokens and SMS texts when used in high volume.
- Identity and Access Management
- $0.016 per external user (customers, vendors, etc.)
- $0.25 Oracle Apps Premium
- $3.20 Identity and Access Management Premium
- Access Governance
- $0.69 for first 10k users
- $0.63 for > 10k to < 50k users
- $0.54 for 50k users and more
Identity and Access Management (IAM) Service Providers
The hidden assumption in selecting a software solution, even SaaS, is that an organization has access to the time and expertise needed to install, configure, and use the tool. For resource constrained organizations that require IAM, sometimes the best option will be to outsource IAM to a service provider.
For better or worse, the number of service providers greatly exceeds the number of potential IAM tool vendors, so it isn’t possible to create a reasonable list of the ‘best’ 5 vendors without the context of an organization’s needs. Instead, we’ll focus on the type of vendors and what they may offer.
IT Consultants
Many consultant companies offer technology services as part of their service portfolio. The largest global enterprises may look for global names to provide their IAM services such as KPMG or EY. However, there are consultants of all sizes and an organization with a high comfort level with their local consulting team may be quite satisfied with expanding their services to cover IAM.
IT and Security Specialists
Some organizations prefer to keep their IT and security services with managed IT service providers (MSPs) and managed IT security provider (MSSP) specialists. A wide variety of big and small vendors provide IAM services to an equally broad variety of customers. Each vendor will have their favorite IAM tools and techniques, so organizations will need to verify that the provider can meet their specific needs and integrate with their critical applications.
Organizations seeking IAM services can start by talking to their current IT and security vendors to explore options. For competing quotes, a quick internet search will unveil IAM service providers such as:
- GlobalSign by GMO
- Infosys
- Intervision
- Optiv
- Veritis
- Verizon
Another good resource is to examine the websites of tools that the organization might consider for their IAM needs. For example, IBM offers managed IAM services and most vendors, such as OneLogin, will list sales and technology partners that can help outsource some or all of the IAM needs.
How the Top IAM Solutions Were Selected
To create the pool of candidates for this year’s top IAM solutions, we consulted a variety of internet sources such as Gartner’s Magic Quadrant for Access Management, the Forrester Wave for Identity as a Service (IDaas), the Identity Management Institute, and customer reviews on websites such as G2. We also checked the vendor websites and examined their capabilities and features.
To remain under consideration, the tool needed to deliver robust capabilities for both identity management as well as access management. Some otherwise capable tools did not make the cut because they might only deliver some of those capabilities.
Identity management requires the creation, administration, and deployment of identifiers, credentials, and attributes. Access management requires focus on the control of permissions assigned to users and evaluating those permissions against identity whenever information or asset access is requested.
Some tools might deliver the equivalent benefits of IAM, but using other technologies such as controlling remote access. Our assumption is that organizations searching for IAM are looking specifically for IAM solutions so those tools were not included.
Examples of tools that were excluded from this article include:
- Cisco / Duo – Cisco deploys an impressive array of access control tools from Duo’s MFA, to robust network access control. However, their lack of features for identity management on their website and light documentation of those capabilities meant they did not make the cut.
- Prove – Prove uses phone numbers to help prove identities and provide robust identity confirmation. However, the tool does not provide access management or true identity management features such as groups.
- Semperis – Sempris offers very important security tools to protect Active Directory, but while this is identity management adjacent, it does not qualify as IAM.
- Twingate – Twingate provides the equivalent of IAM for cloud applications by offering a web-based alternative to VPN, however, it does not explicitly offer IAM capabilities.
The remaining tools were compared for capability and we picked the most notable 5 dedicated IAM solutions and most interesting 5 IAM solutions that are part of larger tool sets for this article. Given the number of quality vendors and fast pace of change in this space, we can expect this list to change over time.
Why Are IAM Tools So Popular?
Identity and access management tools become important once an organization has multiple locations, remote workers, and the need to control access to cloud-based resources or SaaS applications. Smaller organizations often manually control access to each resource, but once the cloud resources reach a certain value or the organization reaches a certain size, then delays in lifecycle management become more costly.
Organizations that delay access to applications for new employees wind up wasting time and money. Organizations that delay removing access to employees leaving the organization risk data theft or sabotage. IAM can also provide the basis for implementing other security initiatives such as zero trust or secure access service edge (SASE).
How Do You Select an IAM Solution?
Once an organization recognizes the need, they need to find a suitable solution. The key factors in the decision will likely revolve around:
Integration Capabilities: If you have a critical app a superior application that does not integrate with or support that critical app will be useless. Actual usability is more important than potential capabilities.
User Experience: How much hassle is introduced or reduced by implementing IAM? Many tools introduce self-service application requests, automated approvals, and single sign-on (SSO) capabilities that reduce friction for users to obtain and use internet-based resources. Organizations with heavy mobile users will also need to ensure their solution delivers a smooth mobile experience for their users.
Security Needs: Organizations with advanced security requirements will need to deploy MFA options, execute granular control over access, as well as track and report on access by asset or by user.
Resources Needed: Some tools will be resource-light SaaS solutions and others will require local system deployments. The cost of the required resources to run the tool will also need to be added to the potential personnel costs for installation, configuration, maintenance, and use.
Delivered Value: Ideally, tools don’t just deliver features, they should deliver benefits. The value of additional security and control may be difficult to quantify, but time savings compared to manual execution of IAM tasks has led to Return on Investment (ROI) estimates between 482% and 548%.
Each organization will need to verify that the capabilities of the tools meet their needs and estimate their accompanying resources and ROI. Many tools provide trial periods for testing, but keep in mind that integrations can be time consuming and should be reserved for finalists.
Frequently Asked Questions (FAQs)
The following questions emphasize the importance of IAM tools in enterprise environments and the ways they work with other solutions.
Why Are IAM Tools So Popular?
Identity and access management is a critical technology for any business with applications that use and store sensitive information. This information includes both proprietary and customer data.
Because IAM tools help businesses manage employee access to data, they also help companies stay compliant with regulatory standards. Most data protection standards have access requirements, such as auditing which employees can access specific information. Using IAM solutions helps businesses meet those requirements.
What is the Difference Between IAM and Active Directory?
A directory service like Active Directory is only one component of an identity and access management platform. It records user data and stores it for IAM solutions to use. Many IAM tools integrate with AD because it’s one of the most popular directories.
AD is useful, but it’s not a substitute for an IAM solution. Directories don’t provide the level of access and policy management that many IAM tools do, and they won’t be able to protect applications and data on their own.
How Do You Select an IAM Solution?
Once an organization recognizes it needs IAM, it must find a suitable solution. The key factors in the decision will likely include:
- Integration capabilities: If you have a critical app, a superior application that does not integrate with or support that critical app will be useless. Actual usability is more important than potential capabilities.
- User experience: How much hassle is introduced or reduced by implementing IAM? Many tools introduce self-service application requests, automated approvals, and single sign-on (SSO) capabilities that reduce friction for users to obtain and use internet-based resources.
- Security needs: Organizations with advanced security requirements will need to deploy MFA options, execute granular control over access, and track and report on access by asset or by user.
- Resources needed: Some tools will be resource-light SaaS solutions and others will require local system deployments. The cost of the required resources to run the tool will also need to be added to the potential personnel costs for installation, configuration, maintenance, and use.
- Delivered value: Ideally, tools don’t just deliver features; they should deliver benefits. The value of additional security and control may be difficult to quantify, but time savings compared to manual execution of IAM tasks has led to Return on Investment (ROI) estimates around 500%.
Each organization will need to verify that the capabilities of the tools meet their needs, and they’ll need to estimate their accompanying resources and ROI. Many tools provide trial periods for testing, but keep in mind that integrations can be time consuming and should be reserved for finalists.
Overview of Identity Access Management Trends
Identity and Access Management and ID-as-a-Service does not provide a miracle cure for security risk as Okta customers discovered last year. However, IAM done well can reduce the risk of human error and contain the impact of mistakes.
As more organizations evolve, their need to control workforce and consumer access to their applications, identity and access management naturally increases in importance and adoption rate. As adoption of IAM increases, the capabilities and uses of IAM also continue to increase. The big trends in IAM consist of increasing scope, incorporation of artificial intelligence, and enabling new standards for secure access.
Expanding Scope of IAM
Organizations used to only worry about verifying the identity of employees and granting them access to internal resources such as shared servers and network devices (printers, workstations, etc.). However, as IT explodes in scope, the definition of IAM also evolves in definition.
We still secure the workforce, but now IAM can expand the scope of users to incorporate customers and even applications that need to access corporate resources. We still secure servers and network devices, but we also expand IAM to control access to containerized cloud resources and internet based SaaS apps.
AI-Powered IAM
As artificial intelligence improves, more vendors incorporate AI and machine learning to develop behavior analytics modules that detect and warn against anomalous user behavior. These tools improve the overall security for the organization without adding significant requirements for security personnel or other security tools.
IAM: Enabling New Secure Access Standards for Zero Trust and SASE
With more users than ever accessing applications remotely, limiting access for remote employees, partners, and customers has become as complicated as it is critical. A static single sign-on (SSO) or multi-factor authentication (MFA) product isn’t going to cut it at the enterprise level, where the cost of a breach is high.
Breach costs can include lost data, stolen intellectual property, damaged customer trust and reputation, incident response costs, and downtime. Steep fines may even be incurred stemming from breached compliance regulations like HIPAA, GDPR and CCPA if medical or personally identifiable information (PII) is involved.
To reduce risk and secure assets outside of the local network, many organizations turn to secure access service edge (SASE) and zero trust principles. IAM helps to fulfill the requirements of these principles by verifying user identities, managing the principle of least privilege, defining access policies for assets, and complying with the access requirements (MFA, etc.) defined by the policies.
The Future of IAM: Decentralized Identity
Gartner sees the IAM market eventually delivering decentralized identity. Instead of a user-focused system of identity and verification, an “identity trust fabric” will provide a layer of security between users and applications.
However, the current concept of decentralized identity relies upon blockchain technology and is also tied to the still-emerging concept of the cybersecurity mesh that will unify the vast distributed enterprise networks and resources into a centralized policy management and orchestration layer.
Bottom Line: Developing the IAM Ecosystem
The selection of an identity and access management solution can dramatically increase security and control over SaaS and cloud resources. For organizations seeking to further improve security, there are many adjacent technologies that compliment and strengthen an IAM solution.
For example, Privileged Access Management (PAM) provides specialized tools to manage administrator and other elevated and dangerous access levels. Active Directory security, machine identity security, password managers, and encryption key management also address key factors of identity and permissions security that could pose enormous risk to a breached organization.
Although it might seem that there will always be another tool needed to fully secure an organization, implementing broad, fundamental security layers will always be the first important steps to take. For today’s dispersed IT environment, adopting an effective IAM tool should be one of those effective first steps.