Security Information and Event Management (SIEM) is a critical enterprise technology that pulls data from IT and cybersecurity systems to assess threats and manage risks.
This guide evaluates the leading SIEM software solutions in the marketplace, focusing on the five SIEM tools we think are clear market leaders, followed by 10 strong contenders. We’ll also discuss what SIEM is, how it works, and how to choose a solution.
Also read: SIEM Explained: What is SIEM and How Does it Work?
- Splunk Enterprise Security: Best for IT Observability
- IBM Security QRadar SIEM: Best for Global Reach
- Securonix Unified Defense SIEM: Best for Future-Looking Vision
- Exabeam Fusion: Best for Log Storage and Searchability
- LogRhythm SIEM Platform: Best for On-Premises SIEM
- Honorable Mentions
- 15 Key Features of SIEM Tools
- How to Choose a SIEM Solution
- How We Evaluated the Top SIEM Tools
- Bottom Line: SIEM Tools
Comparing the Top SIEM Software & Tools
| MITRE ATT&CK Mapping/Support | Advanced Analytics Features | Starting Price | Free Trial Available | |
|---|---|---|---|---|
| Splunk Enterprise Security | Yes | Yes | Splunk offers entity and workload pricing; workload is positioned as the more value-oriented plan. Legacy ingest rates had started at $150 a month for 1GB of data/ day. | Yes, for Splunk Enterprise |
| IBM Security QRadar SIEM | Limited | Yes | QRadar Community Edition: Free. Software: Starting around $320 per month. SaaS: Starting around $2,340 per month. |
Available through certain MSSPs |
| Securonix Unified Defense SIEM | Limited | Yes | Contact Securonix for pricing information | Available for SaaS offering |
| Exabeam Fusion | Yes | Yes | Contact Exabeam for pricing information | Available for SaaS cloud offering |
| LogRhythm SIEM Platform | Limited | No | Based on needed MPS processing capacity; pricing typically starts under $30,000 | No |

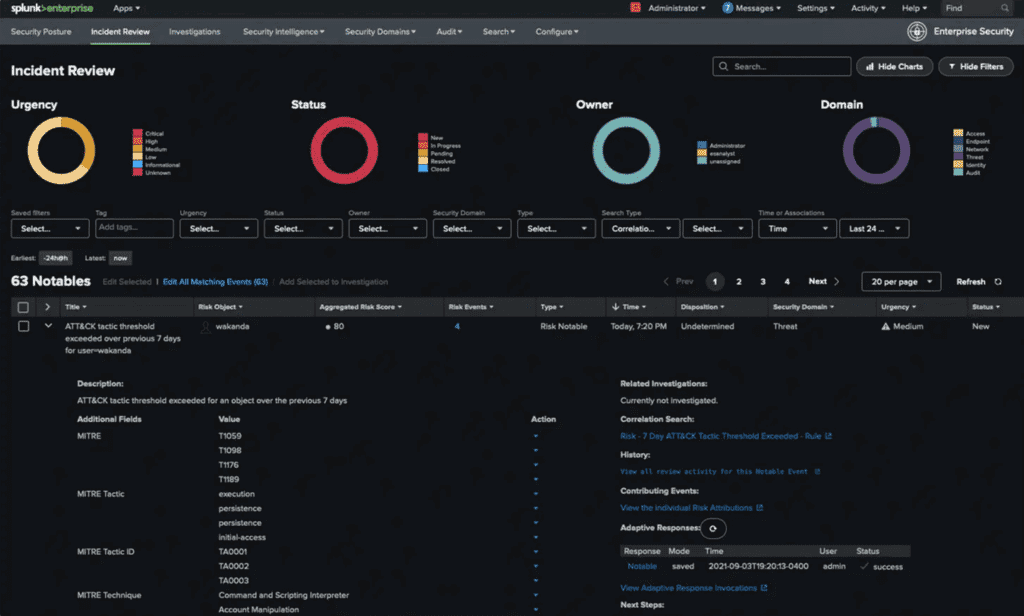
Splunk Enterprise Security
Best for IT Observability
Almost two decades after its launch, analytics-first Splunk offers plenty to consider in security and observability offerings. Splunk Enterprise Security — deployed on-premises or in multi-cloud environments — is designed to detect threats quickly and offer teams a flexible route to investigation and remediation. For SIEM capabilities, Splunk Enterprise Security is a scalable platform with over 2,800 apps that connect data and workflows.
Key Features
- Risk classification by users and systems against security and compliance frameworks
- Scalable platform for structured and unstructured data ingestion, as well as data federation
- Built-in threat intelligence via Threat Intelligence Management tool
- Deployable as a cloud-hosted, IaaS, software, hardware appliance, or hybrid solution
- Access to 700+ detections for frameworks like MITRE, NIST, Kill Chain, and CIS 20
Pros
- Has one of the most comprehensive, data-centric approaches to SIEM and enterprise security in the market
- Flexible infrastructure and deployment options
- Integrates with a wide range of network and security devices
Cons
- Smaller teams in particular may not have the resources to quickly configure and implement this solution
- Splunk ES’s pricing and licensing model is not straightforward and can get very expensive
- Fairly limited to the North American market
Pricing
Splunk no longer publishes pricing information so prospective buyers should contact the company for a quote. Splunk offers legacy ingest pricing in addition to entity pricing and workload pricing. Workload pricing is being positioned as the more value-oriented plan. Enterprise ingest rates had started at $150 a month for 1GB of data a day, with discounts per GB as volume increases. AWS also has some pricing info.

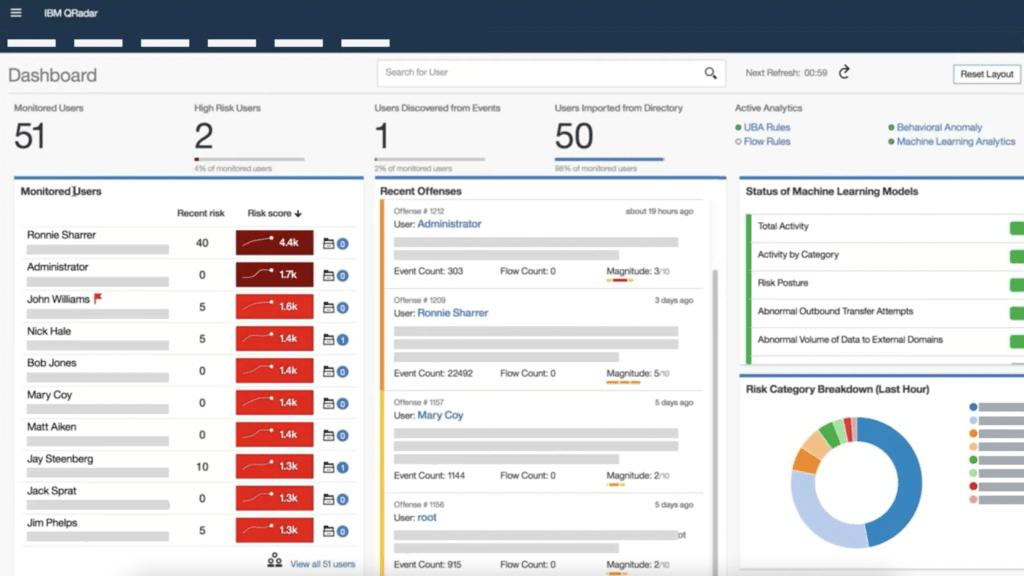
IBM Security QRadar SIEM
Best for Global Reach
IBM Security QRadar SIEM is an enterprise favorite that’s adapted alongside the evolution of the SIEM market. Most recently, IBM launched the IBM Security QRadar Suite to more effectively combine threat detection, investigation and response, SOAR, SIEM, EDR, and XDR in one platform service for hybrid cloud users.
Following rigorous frameworks for compliance and reporting, QRadar SIEM is one of the safest bets for enterprise companies. Its global reach is a definite advantage for many customers, with localized support services, regional regulatory knowledge, and distributed direct and partner channels in North America, Europe, APAC, the Middle East, and South and Central America.
Key Features
- Continuous monitoring of on-premises and cloud environments throughout the kill chain
- IBM’s Security X-Force and STIX/TAXII feed inform threat intelligence
- Compliance resources are available for HIPAA, SOX, ISO, PCI, NIST, GLBA, GDPR and CCPA
- Users can deploy QRadar SIEM as a hardware appliance, software, SaaS, or VM for on-prem and IaaS environments
- Access to 450 integrations, APIs, and a software development kit (SDK)
Pros
- IBM’s solution utilizes artificial intelligence (AI) to accelerate the detection of threats, along with user behavior analytics (UBA) and network flow insights
- IBM has the most widespread and diverse portfolio of global security solutions and security experts
- IBM’s security ecosystem is vast and integrates well with QRadar SIEM
Cons
- Initial onboarding and implementation is a difficult process for many users
- The user interface is outdated and somewhat difficult to navigate
- Some users have commented on a lack of product support and new developments in the platform
Pricing
IBM QRadar SIEM comes in a variety of formats and pricing packages. Here’s a breakdown of pricing information that the vendor provides on its site:
- QRadar Community Edition: Limited free version
- IBM QRadar SIEM (Software): Sliding scale based on the total workstations/employees and total servers in the environment. Depending on your requirements, the estimated price ranges from $320 per month to $26,540 per month.
- IBM QRadar SIEM (SaaS): Sliding scale based on the total workstations/employees and total servers in the environment. Depending on your requirements, the estimated price ranges from $2,340 per month to $25,922 per month.
- Managed Service: Pricing information is available upon request
- On-Premises Offering: Available in subscription and perpetual models. Pricing information is available upon request.
Pricing is also broken down by Usage and Enterprise models. The Usage Model is based on Events per Second (EPS) and Flows per Minute (FPM). The Enterprise Model is based on the number of Managed Virtual Servers (MVS) used.
See the Top Security Orchestration, Automation and Response (SOAR) Solutions

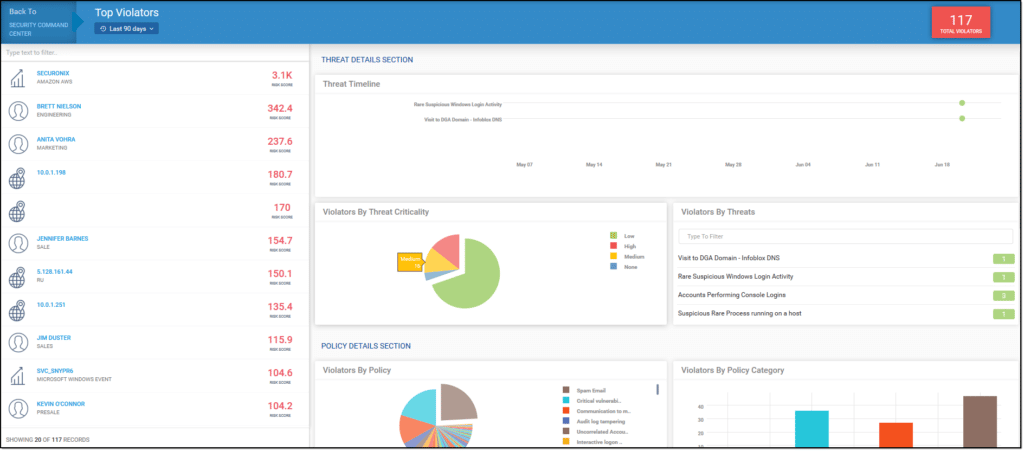
Securonix Unified Defense SIEM
Best for Future-Looking Vision
Securonix recently launched its new Unified Defense SIEM, which combines SIEM with threat detection, investigation and response (TDIR) and SOAR. It’s built on the Snowflake Data Cloud to maximize “hot” searchable data. Autonomous Threat Sweeper (ATS) searches for threats, and Threat Coverage Analyzer assesses security gaps and how your coverage stacks up against industry frameworks such as MITRE ATT&CK and US-CERT.
Securonix has long been recognized for its innovative approach to SIEM, especially when it comes to providing third-party data lake access and enabling data decentralization — a trending, cost-effective approach to SIEM.
Key Features
- Ingestion for cloud-based, on-premises, and hybrid environments on a central console
- Long-term search capabilities for slower threats spanning historical data
- Cloud-native platform with on-demand scalability and SaaS subscription pricing
- Access to 350+ cloud connectors for data collection and API-based cloud integrations
- Use case content and investigation workbench is available to create cases with industry examples
Pros
- Integrated SOAR allows teams to accelerate incident response.
- Response times are also reduced with Securonix’s playbooks and workflow recommendations.
- Built-in threat intelligence at no additional cost.
Cons
- Historically, Securonix has had only limited role-based access control (RBAC)
- Users say Securonix is sometimes so focused on pioneering new features that it does not take time to perfect long-standing SIEM features
- Some limitations to out-of-the-box log collection
Pricing
Interested buyers should contact Securonix for pricing information. AWS also has some Securonix pricing information.

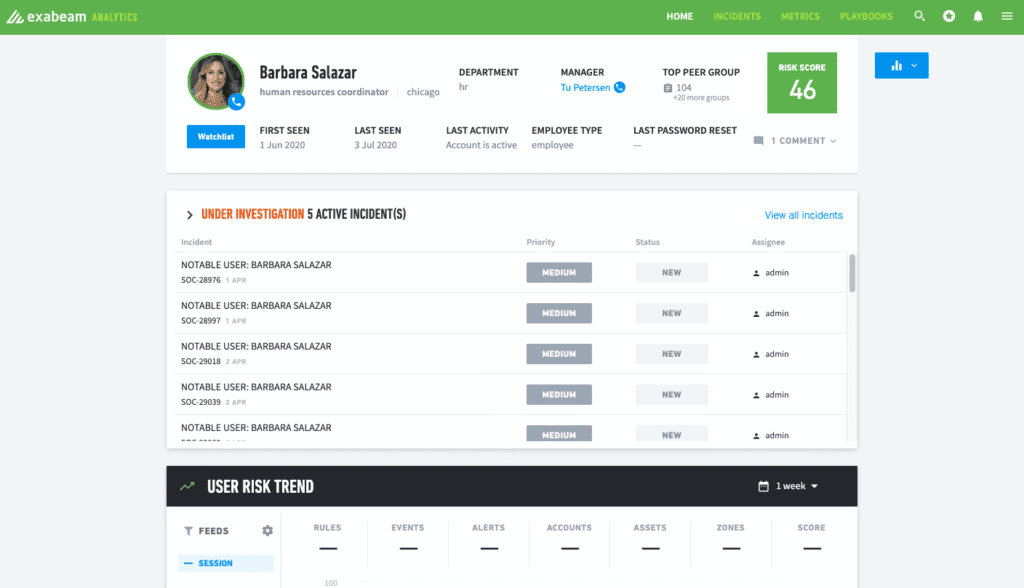
Exabeam Fusion
Best for Log Storage and Searchability
Exabeam Fusion is Exabeam’s threat detection, investigation, and response (TDIR) solution that brings together automated, next-generation SIEM and XDR capabilities. Beyond centralized log management, Exabeam Fusion includes a stack of security features to aid in an era of advanced threats. Companies can connect existing security tools with an extensive integration ecosystem or replace and condense security functions via Fusion’s capabilities.
Key Features
- User and entity behavior analytics (UEBA) for insider and zero-day threats
- Full indexing for log ingestion and advanced search capabilities
- Smart timelines gather and present evidence for incident timelines
- Access to hundreds of playbooks and dashboards for compliance reporting
- Integration options for over 500 security and IT tools in TDIR space
Pros
- Relatively straightforward interface and user experience
- Some of the best UEBA capabilities in the SIEM market
- Log storage is able to store and retain searchable data for up to 10 years
Cons
- Limited transparency in Exabeam’s pricing model
- Third-party alerts are occasionally delayed in Fusion
- Limited detection and response capabilities are built into Exabeam Fusion
Pricing
Exabeam does not clearly communicate Fusion pricing on its vendor pages. Interested buyers will need to contact Exabeam’s sales team directly for pricing information. Exabeam SaaS Cloud free trials are also available upon request.

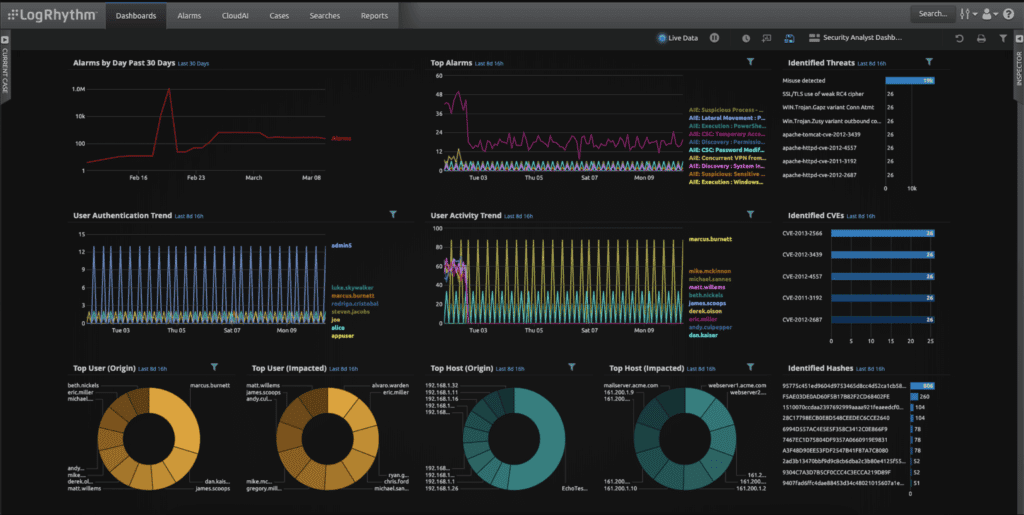
LogRhythm SIEM Platform
Best for On-Premises SIEM
LogRhythm is an undisputed industry leader in the SIEM space, with a cybersecurity solution portfolio that extends to SOAR, UEBA, and network detection and response (NDR). The vendor’s flagship product, the LogRhythm SIEM Platform, is available in hardware appliance, software, cloud, and hybrid solution formats with scalability for enterprise organizations. As full-featured as any SIEM solution, LogRhythm is a favorite among customers, especially those who require a capable on-premises SIEM for their legacy network infrastructure.
Key Features
- Advanced analytics detect malicious activity through compliance and security contexts
- Prebuilt playbooks include alert triage, threat context, and case grouping
- Accelerated threat detection and response comes with automated workflows for remediation
- Threat intelligence and defensive analysis from LogRhythm Labs
- Access to 950+ third-party data sources and 1,100 preconfigured correlation rule sets
Pros
- A longtime, established provider of on-premises SIEM
- A strong network of MSPs and reselling partners
- The product interface and administration features are considered relatively easy to use
Cons
- Fairly new to and struggling to gain its footing in the cloud and SaaS market
- Limited API key integration capabilities for LogRhythm apps
- Customers have historically disliked LogRhythm’s infrequent product, roadmap, and update releases; the company has since committed to quarterly product releases
Pricing
LogRhythm products are offered to users in four different pricing package formats: Software Solution, True Unlimited Data Plan, High-Performance Appliance, and Unified License Program (ULP). Specific pricing information is not provided for any of these plans, but prices typically start under $30,000. Prospective buyers will need to contact LogRhythm for specific pricing information.
Honorable Mentions
The SIEM market is packed with good solutions, and here are 10 additional SIEM tools that may meet your needs.
Fortinet FortiSIEM
Industry-recognized firewall vendor Fortinet offers FortiSIEM as just one part of an extensive cybersecurity portfolio. The Security Operations portfolio includes products for SIEM, SOAR, XDR, and advanced detection and protection like NDR, deception systems, and inline sandbox analysis. Available as a hardware appliance, virtual machine, or cloud-based solution, FortiSIEM offers a comprehensive array of specs to users.
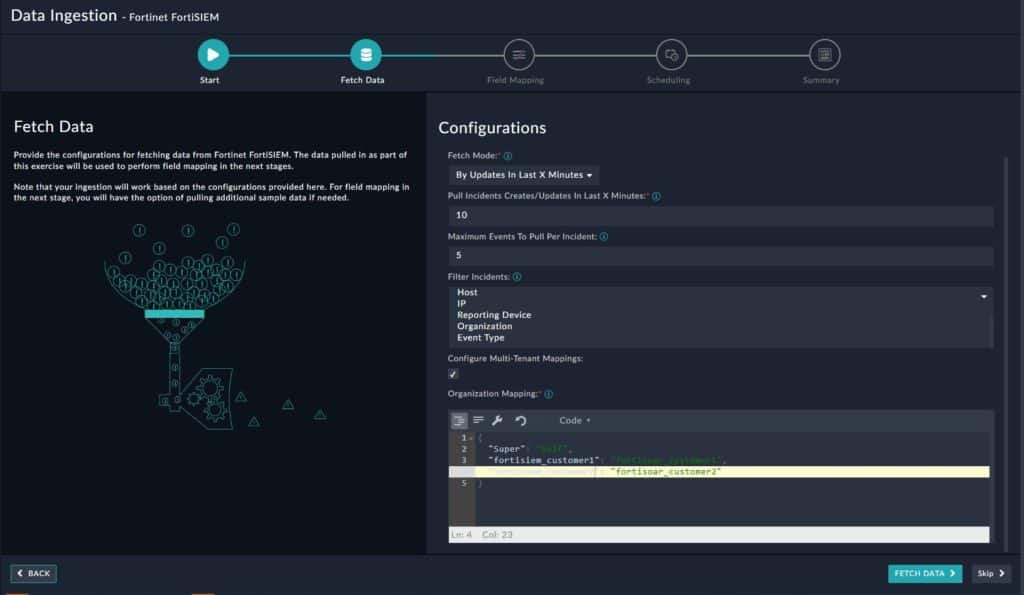
Fortinet FortiSIEM Features
- ML-based user and entity behavior analysis to identify insider and incoming threats
- Real-time monitoring of system performance, availability, and changes
- Risk scoring for users and devices to evaluate entities and correct behavior
- Configurable dashboards, shareable reports, and layered analytics
- Built-in support for vendor APIs and Windows and Linux agents
Logpoint Converged SIEM
SIEM specialist Logpoint has over twenty years of experience building a security platform that features UEBA, SOAR, and converged SIEM. With a blended focus on cybersecurity, business analytics, IT operations, and compliance, Converged Logpoint SIEM is a comprehensive cloud-based solution designed for enterprise or MSSP deployments. Logpoint holds particular expertise in infrastructure compliance monitoring, relying on its business-critical application security (BCAS) capabilities for SAP clients.
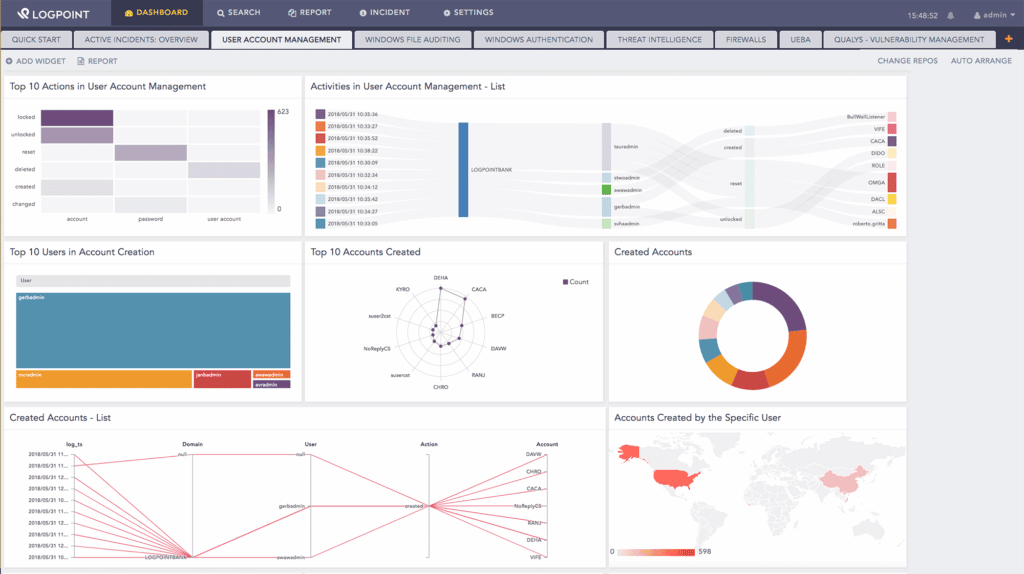
Logpoint Converged SIEM Features
- Central cloud-based console for data ingestion, event reporting, and analysis
- Alert aggregation and triage prioritized by severity
- AI-based profiling of normal behavior and patterns to identify suspicious activity
- Workflow and playbook automation for investigation and remediation
- Integrations for identity and access management (IAM), threat intelligence, EDR, and cloud APIs
Trellix Security Operations and Analytics
The merger of FireEye and McAfee Enterprise in 2022 created a new brand — Trellix — with a portfolio that includes security solutions for endpoints, databases, networks and email, while McAfee’s cloud security portfolio was spun off as Skyhigh Security. Previously a part of the McAfee Enterprise Security Manager and FireEye, Trellix’s SIEM solution is known as Trellix Security Operations and Analytics. The SecOps and Analytics stack includes Helix for next-gen SIEM integration, Trellix Insights for threat intelligence, and Trellix ePO for on-premises and cloud endpoint orchestration.
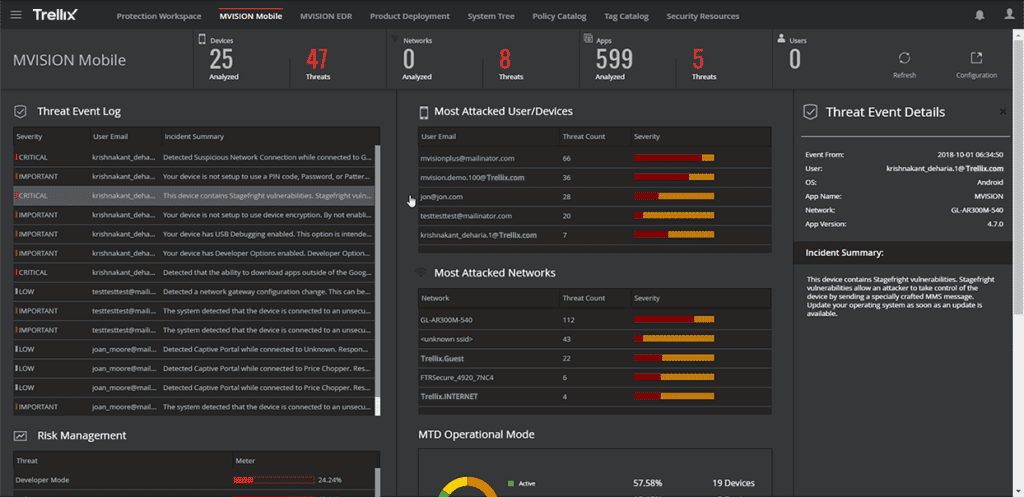
Trellix SecOps and Analytics Features
- ML-based user and entity behavior analytics identify and correlate risks
- An investigative workbench provides alert management, search, and analysis
- Access to 650 data sources for out-of-the-box integrations and connectors
- Proactive and preemptive action informed by the Advanced Threat Research team
- Threat intelligence exchange and advanced threat protection for effective sandboxing
CyberRes by OpenText ArcSight Enterprise Security Manager (ESM)
Previously owned by Micro Focus, the CyberRes by OpenText business line includes solutions for application security, data protection, IAM, and security operations through the ArcSight Enterprise Security Manager (ESM). ArcSight ESM combines SIEM and SOAR to alleviate the manual workloads of analysts and implement layered analytics across security tools.
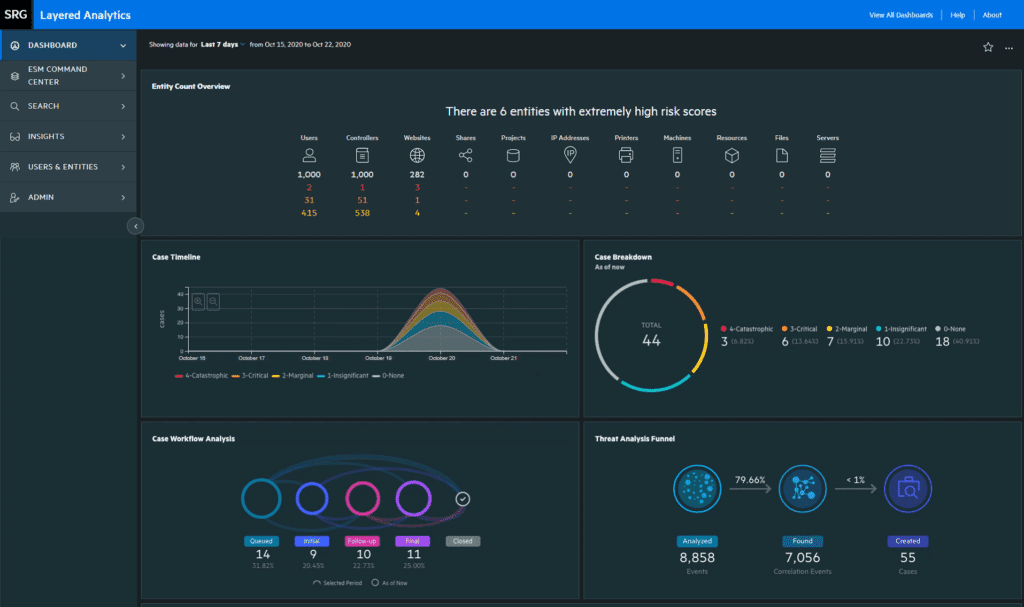
CyberRes by OpenText ArcSight ESM Features
- Unified log storage with big-data search and analytics visualization.
- Active scanning for reconnaissance, initial access, persistence, and more
- Native SOAR capabilities to automate, orchestrate, and enable incident response
- Real-time correlations and hypothesis-based threat hunting to identify risks
- Threat monitoring content packages that cover MITRE ATT&CK techniques and tactics
Rapid7 InsightIDR
Rapid7 offers a comprehensive SIEM platform with its flagship SIEM-XDR hybrid solution InsightIDR. Teams can use InsightIDR to automate everything from repetitive tasks to triage alerts to responses to threat behavior. Alongside products like InsightVM for vulnerability management, Rapid7’s SIEM solution includes EDR, network traffic analysis (NTA), UEBA, threat intelligence, and deception technology.
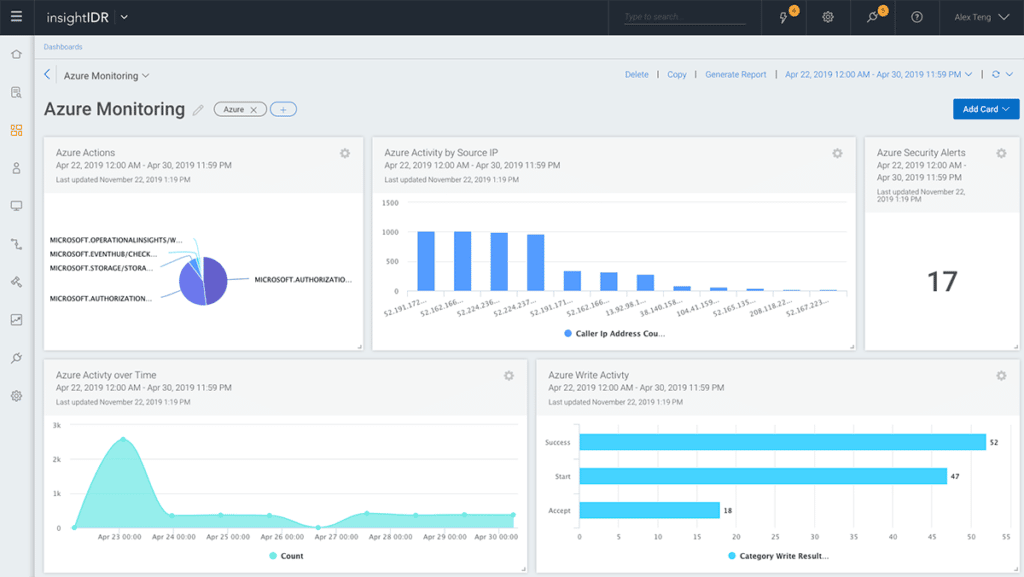
Rapid7 InsightIDR Features
- Deployable Insight agents for any asset in on-premises environments or the cloud
- Execute containment actions across Active Directory, IAM, EDR, and firewalls
- Enhanced endpoint telemetry for historical activity investigations
- File integrity monitoring meets compliance frameworks for GDPR, HIPAA, and PCI
- Access to 300+ IT and security system plugins
AT&T USM Anywhere
AT&T USM Anywhere goes beyond traditional SIEM solutions with a stack of advanced enterprise security capabilities. These built-in capabilities include EDR, vulnerability assessment, incident response, and monitoring for file integrity and cloud infrastructures like AWS, Azure, Google Workspace, and Microsoft 365. Backed by a reputable threat intelligence unit with Alien Labs, the USM Anywhere solution is a top choice for small businesses and enterprise organizations alike.
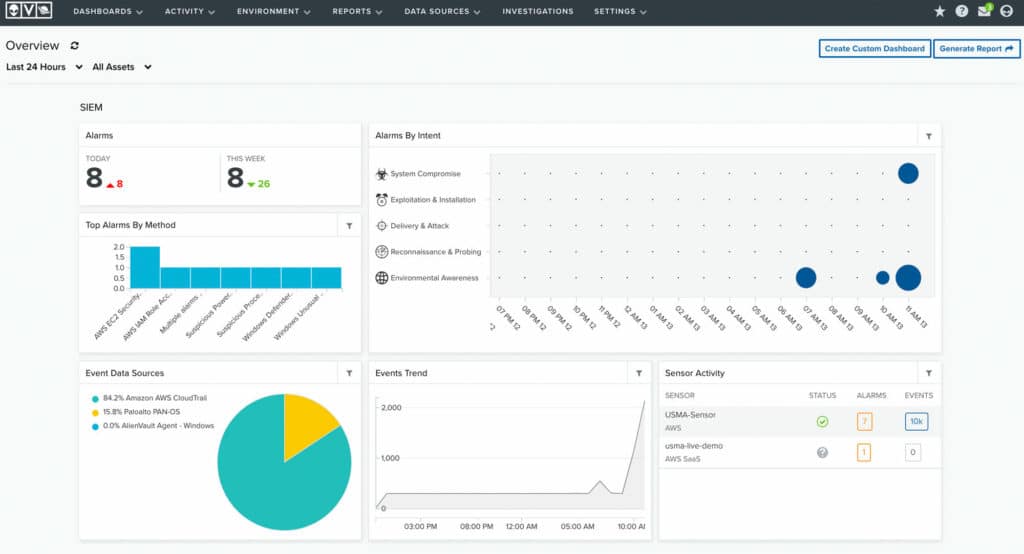
AT&T USM Features
- Utilize kill-chain taxonomy to identify behavior in five understandable categories
- Filter searches by event name, IP address, and more
- Determine business-critical asset vulnerabilities and prioritize remediation
- Orchestration rules are available for select action alarms and raw data related to alarm activity
- Built-in continuous threat intelligence via a unified management console
Elastic Security SIEM
Founded a decade ago in Amsterdam, Elastic rose quickly within the SIEM space with the Elastic Stack (formerly the ELK stack) for infrastructure monitoring, application performance, logging, and more. With acquisitions like Endgame in 2019, Elastic Security continues to extend its automated threat protection, incident response, and continuous monitoring capabilities. While Elastic Security SIEM alone is a considerable solution, Elastic also offers XDR, endpoint security, and cloud security.
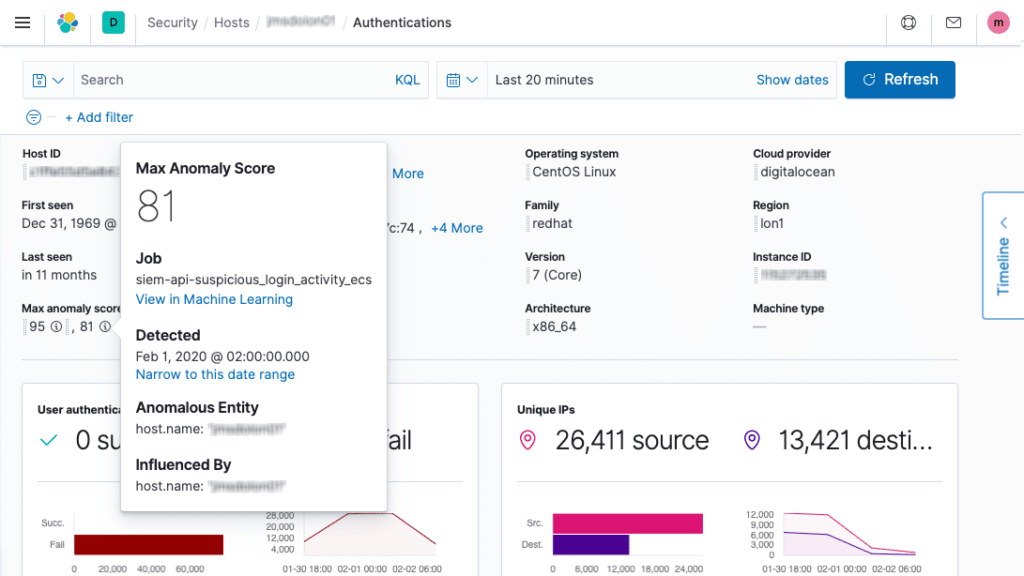
Elastic Features
- Uniform analysis from different data sources using the Elastic Common Schema (ECS)
- Block malware, zero-day threats, and ransomware and conduct remote actions
- Attack detection using MITRE ATT&CK knowledge base to identify adversary behavior
- ML-enabled anomaly detection, analytics, and insights for threat hunters
- Interactive timelines for visualizing and working through case management
ManageEngine Log360
Twenty years after the launch of ManageEngine, the multi-dimensional IT solutions provider has a portfolio covering identity and access management, IT service management, EDR, and low-code app development. ManageEngine’s stack of SIEM solutions includes on-premises tools for security auditing, log and compliance management, and its flagship Log360 SIEM for cloud or on-premises deployment.
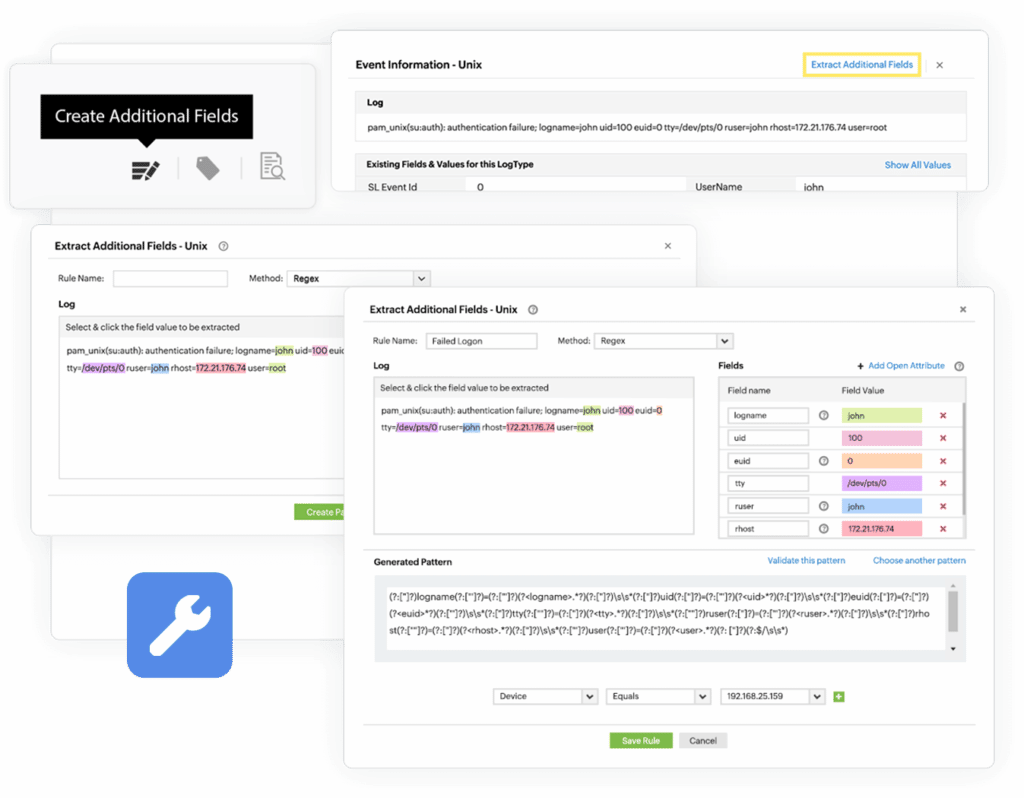
ManageEngine Features
- Integrated DLP, UEBA, and CASB capabilities detect and respond to threats
- Collect logs from IDPS, AV, firewalls, servers, networks, and end-user devices
- Monitor and audit Active Directory with change management and threat tracking
- Threat intelligence from STIX/TAXII-based feeds for blocked IP address and URL activity
- Advanced threat analytics are available to inspect log data and detect suspicious behavior
RSA NetWitness
NetWitness, the longtime cybersecurity unit within RSA Security, emphasizes an evolved SIEM in an era of expanding attack surfaces and increasingly sophisticated threat actors. Through the NetWitness platform, teams can centralize all monitoring data for events, endpoints, and networks with threat intelligence and detection analytics. Features like NetWitness Detect AI offer an adaptive machine learning algorithm to detect and inform security analysts about threats. Users looking for a SIEM solution have the option to choose any of the following products:
- Evolved SIEM
- Cloud SIEM
- Log Management
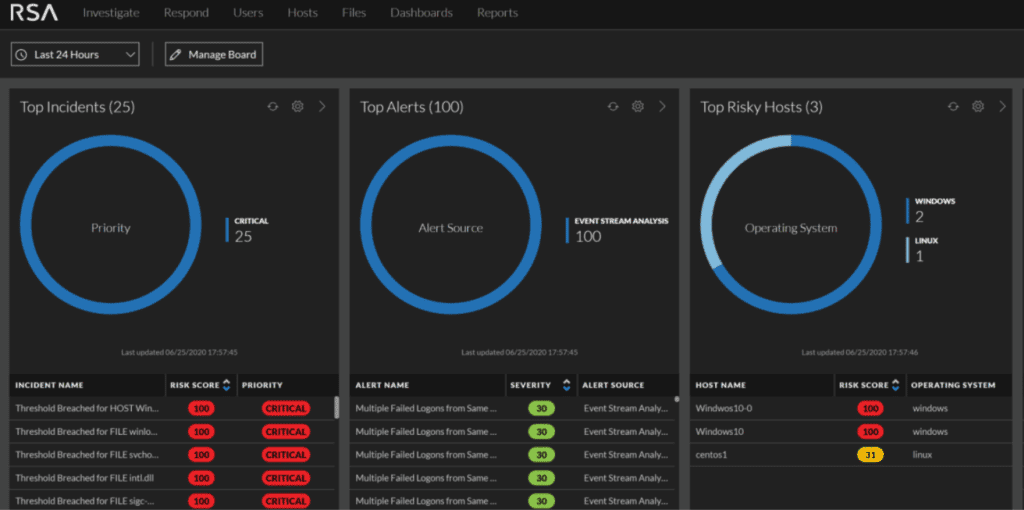
RSA NetWitness Features
- User and entity behavior analytics monitor and identify malicious behavior
- Deployment options include virtual, on-premises, or cloud (AWS, Azure, and Google)
- Orchestrator for automating security operations and easing SOC analyst workflows
- Unified taxonomy across data sources to accelerate threat detection
- Threat intelligence via industry research, business context, and client data sources
Sumo Logic Cloud SIEM
Sumo Logic’s portfolio of observability and security products covers infrastructure monitoring, cloud logs, and application development environments. For security solutions, Sumo Logic excels in cloud security, offering monitoring, analytics, audit, and SOAR tools alongside its SIEM. Sumo Logic Cloud SIEM can cover millions of security-related data points across multi-cloud, on-premises, and hybrid environments while mitigating the traditional manual workload usually designated for security analysts.
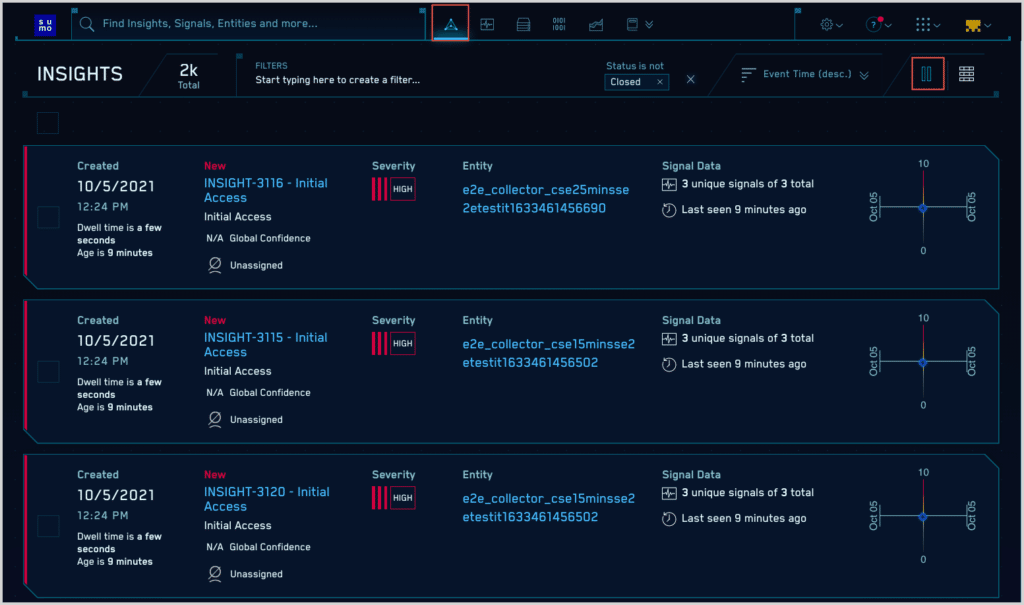
Sumo Logic Cloud SIEM Features
- Correlation-based detection to cluster and prioritize signal and relevant context
- Automated alert triage and analysis to inform security analyst decision-making
- Adaptive Signal Clustering (ASC) engine groups related calls for human review
- Security monitoring with deep packet inspection, which reassembles flows into insights
- API integration options, including Amazon GuardDuty, Microsoft 365, Okta, and Carbon Black
Additional SIEM Vendors
| Blumira | Datadog | Devo |
| Fortra (HelpSystems) | Graylog | Gurucul |
| Huawei | Microsoft | NETMONASTERY |
| Netsurion | Odyssey Consultants | OSSEC |
| SolarWinds | Stellar Cyber | Venustech |
15 Top Features of SIEM Tools
SIEM platforms often incorporate the best factors of other network security tools in order to comprehensively detect vulnerabilities and threats. The top features and capabilities you should look for when selecting a SIEM tool include the following:
- Endpoint detection and response (EDR) and/or extended detection and response (XDR) integration
- Advanced threat detection
- User and entity behavior analytics (UEBA)
- Database, app, network, email, and file integrity monitoring
- Vulnerability monitoring
- Threat hunting, digital forensics, and incident response
- Unified management, asset discovery, and compliance reporting
- Automated correlation, risk prioritization, IoC, and responses
- Native access or integration with security orchestration, automation, and response (SOAR) tooling
- Advanced analytics
- Out-of-the-box content availability
- Integration with ERP, big data, IAM, and threat intelligence platforms
- Flexible infrastructure and deployability via on-premises, cloud, hybrid, and/or virtual environments
- Industry-specific use cases and features
- MITRE ATT&CK mapping and support
How to Choose a SIEM Tool
SIEM tools are differentiated by cost, features, and ease of use. Generally, the more you pay, the greater the capabilities and range of coverage, so buyers must weigh their needs, budget, and expertise as they decide on a SIEM system.
Small businesses might focus on automation, ease of use, and cost. In contrast, an enterprise with a sophisticated security operations center (SOC) might focus on the breadth of threats and assets covered as well as machine learning capabilities for discovering new and emerging threats. Regardless of an organization’s size, deploying and integrating such a complex technology can take time, so look for vendors that offer the help of consultants and MSPs.
Also read: SIEM vs. SOAR vs. XDR: What Are The Differences?
How We Evaluated the Top SIEM Tools
We gather information from various IT industry sources for our top security product reviews. We interview company officials, users, and impartial experts, scouring data sheets and aggregating all information to best inform our content and readers. Our most frequently used sources have been studies and reports from analyst firms like Gartner and Forrester, independent tests, and user review sites like Gartner Peer Insights. Where possible, we utilize demos and hands-on experience to gain a deeper understanding or products.
Bottom Line: SIEM Tools
To get an idea of how vital a SIEM platform is to enterprise security, consider the scale of security incidents and the data involved. A large enterprise may generate more than 25,000 events per second (EPS) and require 50 TB or more of data storage.
A SIEM’s ability to filter through all the data and prioritize the most critical security issues makes security more manageable. An effective SIEM tool will often be expensive, but it will also pay for itself in staff time saved and security incidents thwarted.
Read next: 34 Most Common Types of Network Security Protections

