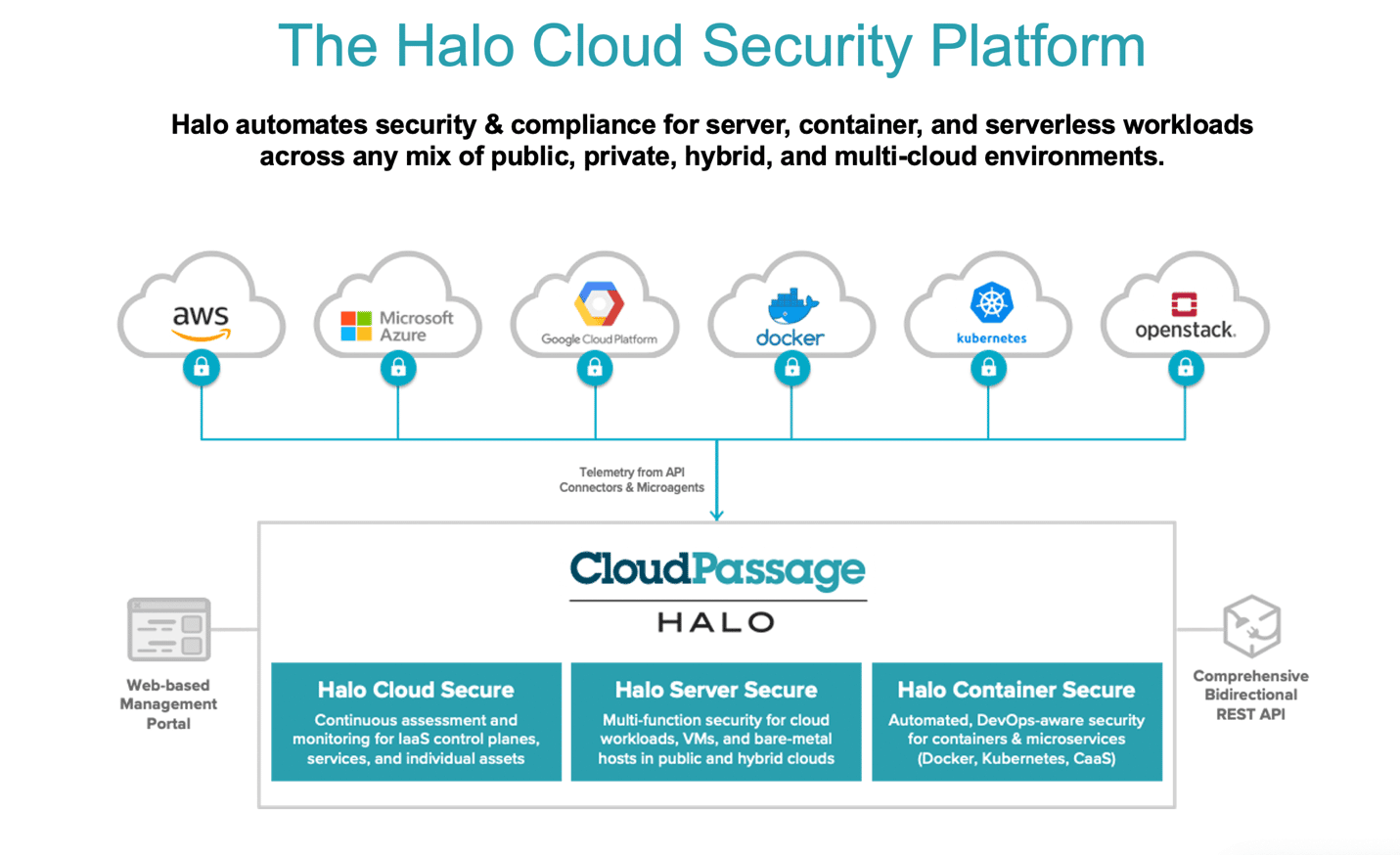
The widespread adoption of cloud and hybrid IT environments has created a need for new cybersecurity paradigms that address the expanded attack surface and new attack vectors that cloud computing brings.
Ensuring the security of your cloud-based services — and the ways they are accessed — is essential for modern enterprises. To help, we’ve analyzed a range of cybersecurity vendors and services to arrive at this list of the best cloud security companies for threat protection, data security, identity management services, and more.
Top cloud security companies:
- Fidelis: Best for DevSecOps
- Skyhigh: Best Security Service Edge
- Lacework: Best CNAP Platform
- Qualys: Best for Compliance
- Palo Alto: Best for Cloud Workload Protection
- Symantec: Best for CASB
- Tenable: Best for Vulnerability Management
- Trend Micro: Best for Hybrid Cloud Security
- Netskope: Best Overall Cloud Security
- Zscaler: Best for Advanced Threat Protection
- Methodology and cloud security buying considerations
Fidelis Cybersecurity: Best for DevSecOps
Fidelis Cybersecurity acquired CloudPassage in 2021 to help create Fidelis CloudPassage Halo, a cloud security platform that provides automated security and compliance monitoring for public, private, and hybrid cloud environments. It gives security teams an automated, unified platform for managing cloud infrastructure, IaaS, PaaS, servers, container applications, and workloads. The company also offers a range of network security solutions to extend that protection. Fidelis is capable of meeting broad security needs, but container and PaaS security are standout features.
The Halo platform adds visibility to your security operation center (SOC) so security teams can quickly protect, detect, respond to, and neutralize threats. Additionally, the platform offers continuous compliance monitoring to ensure that cloud infrastructure and workloads comply with data privacy and other regulations.
Key Features
- Three options: Fidelis CloudPassage Halo is a single platform with three SKUs – Halo Cloud Secure, Halo Server Secure, and Halo Container Secure. All three are licensed by usage level.
- Monitoring and compliance: Fidelis CloudPassage offers automated security visibility and compliance monitoring for workloads that run in any on-premises, public cloud, or hybrid cloud environment.
- Security features: File integrity monitoring, software vulnerability assessment and log-based intrusion detection are some of the standout security features.
- Identity control: A key differentiator for Fidelis CloudPassage Halo is the platform’s automated approach to identify when and if a given workload or configuration strays outside defined policies.
- Cloud platform support: Works across several cloud environments, including AWS, Azure, and GCP
Pros
- Provides real-time visibility, assessment, and control
- Multiple support channels (operations support, customer care, education, training and professional service)
- Integrates with third-party solutions, including SIEM, SOAR, CICD pipeline tools, EDR, ICAP-based products and log files
- Helps organizations reduce compliance costs, improve security posture, and adopt DevSecOps best practices
- Works for all sizes of businesses, including small, medium, and large
Cons
- Lacks transparent pricing
- Steep learning curve
Pricing
Fidelis Cybersecurity does not advertise pricing on its website. However, they offer a 15-day free trial so potential buyers can evaluate the product. Buyers can also request a product demo, which Fidelis Cybersecurity typically provides free of charge. To receive an accurate quote, buyers should contact the vendor directly for more information about their exact pricing structure.
Skyhigh Security: Best Security Service Edge
Skyhigh Security is the cloud security business spun off after McAfee Enterprise and FireEye merged to form Trellix. The company provides a suite of security solutions for cloud infrastructure, data security, and user access. It protects all data access, including a secure web gateway (SWG), cloud access security broker (CASB), and data loss prevention (DLP) capabilities. Skyhigh’s focus is primarily on edge use cases like SASE/SSE, and offers DLP capabilities in a joint offering with Trellix.
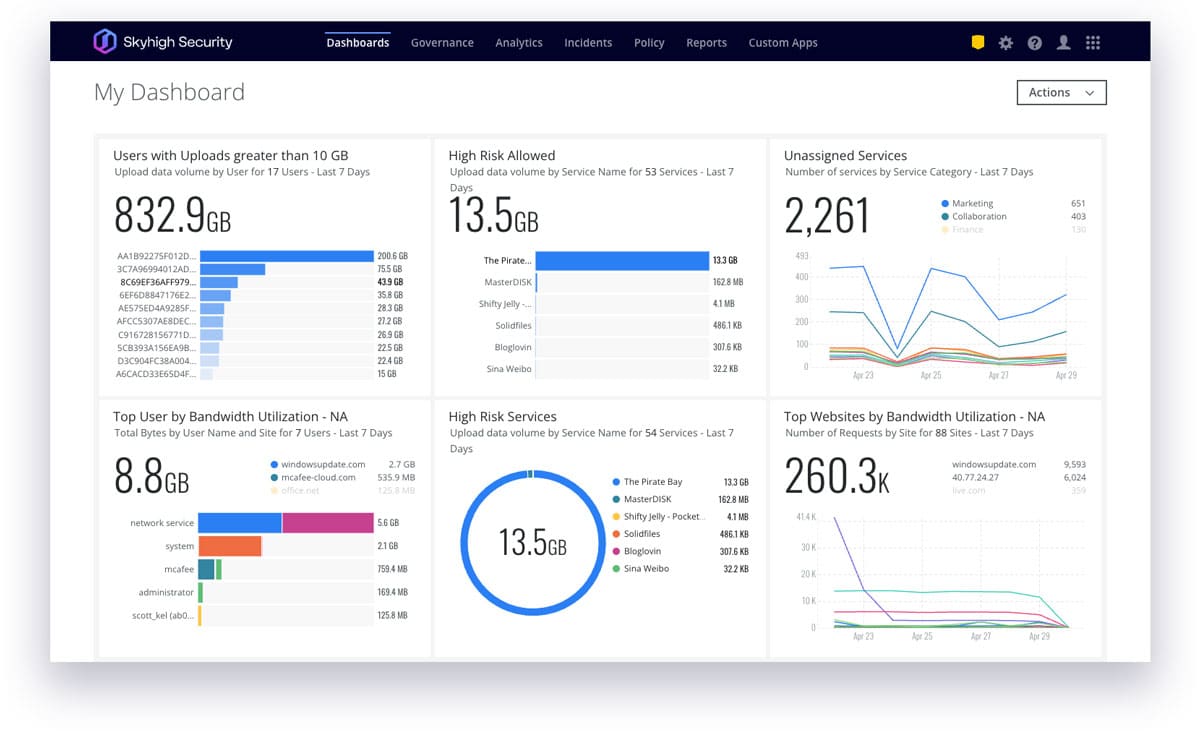
Skyhigh Security describes itself as a company that “provides a data-centric approach to security that offers 360-degree access control to wherever your data resides, expanding to include how your data is used, shared, and created.”
The company is designed to secure data across the web, cloud (SaaS, PaaS, and IaaS) and private applications to reduce risk for businesses using cloud applications and services.
Key Features
- Broad coverage: Adaptive risk-based enforcement (over 30K apps policy advisor)
- Performance: Offers 99.999%, ultra-low latency and over 85 global points of presence (PoPs)
- Isolation: Provides intelligent remote browser isolation and real-time emulation sandboxing
- Logging: Records a detailed log of every action taken by users and administrators to aid post-incident examinations and digital forensics
- Risk management: Offers a customizable 261-point risk assessment to help manage and govern cloud services, giving access to the most comprehensive and precise registry of cloud services globally
- Encryption: Secure sensitive structured data with enterprise-controlled keys using peer-reviewed, function-preserving encryption methods
- Consolidated management: Merges Private Access, CASB, SWG, and remote browser isolation (RBI) into a single platform that can be managed from a single console.
Pros
- Users find the solution stable
- Efficient URL filtering capability
- Unified architecture
- Comprehensive threat analysis
- Integration with third-party tools such as Office 365 and Salesforce
- Post-incident inspections and analytics
Cons
- Limited training resources
- The interface could be improved
- According to user reviews, this solution lacks support for unsanctioned apps
Pricing
Skyhigh Security pricing is available on request. Interested buyers can contact the Skyhigh Security sales team to learn more about the product and request a demo.
Lacework: Best CNAP Platform
Lacework is a cloud-native application protection platform (CNAPP) for modern IT environments. It provides automated security and compliance solutions for cloud workloads, containers, and Kubernetes clusters. With nearly $2 billion in venture funding, the fast-growing startup boasts one of the highest valuations of private security companies.
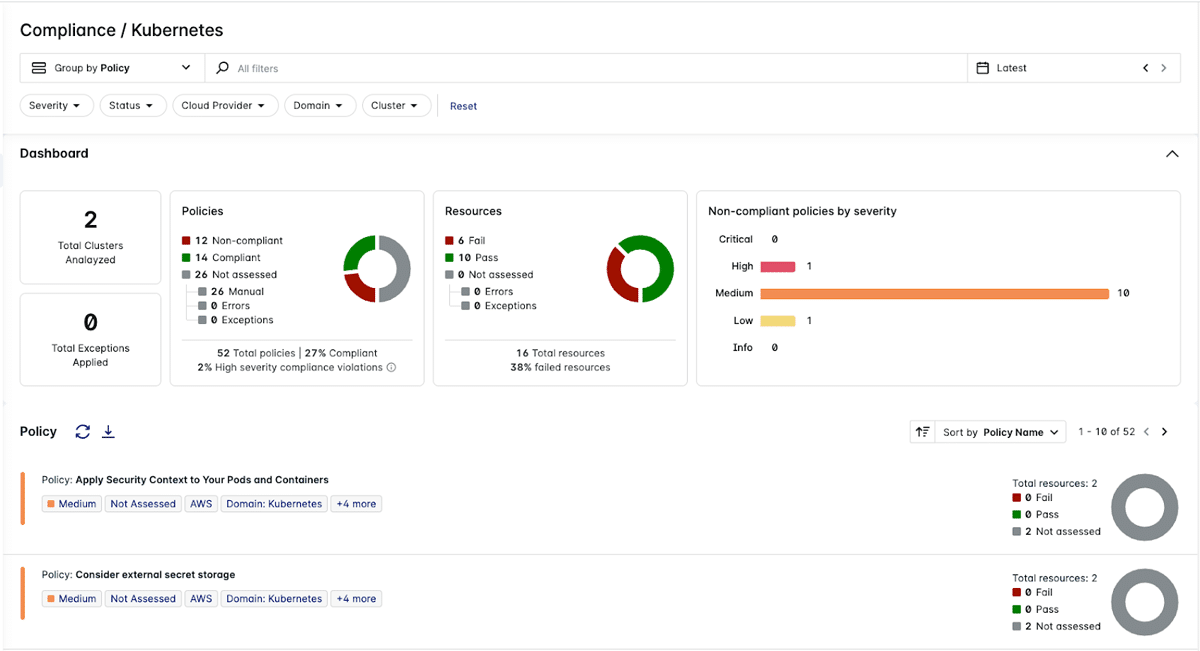
The Lacework Platform uses cloud security posture management (CSPM), infrastructure as code (IaC) scanning, cloud workload protection platform (CWPP), and Kubernetes security to help organizations protect their environment. It also provides cloud incident and event monitoring (CIEM) to quickly detect and respond to threats. With Lacework, developers can scan for security issues locally, in registries, and in CI/CD pipelines while building large-scale applications.
Key Features
- Contextual analysis: The Polygraph feature offers a visual representation of relationships across account roles, workloads and APIs to deliver better context.
- Compliance: Lacework provides monitoring of cloud workloads for both compliance as well as security concerns.
- Intrusion detection: Of particular value is the automated workload intrusion detection capability powered by machine learning to help reduce risks
- Configuration assistance: Configuration best practices support and guidance is another standout feature.
- Threat detection: Uses machine learning and analytics to detect threats in cloud-native environments.
- Vulnerability management: Lacework uses risk-based prioritization to help you identify, prioritize, and remediate known vulnerabilities in your environment.
Pros
- Ease of use
- Users find the dashboard visually appealing
- Users find the solution useful for container image scanning, compliance reports, and AWS CloudTrail
Cons
- Support could be better
- Reporting capabilities could be improved
Pricing
Lacework does not advertise its pricing on its website, as each customer’s needs can vary significantly. The best way to get an accurate quote is to contact Lacework directly. Lacework offers a 14-day free trial for customers to test features and services.
See the Top Cybersecurity Companies and Startups
Qualys: Best for Compliance
Qualys is a cloud security and compliance software platform that helps enterprises identify and protect their digital assets. It provides a unified platform for security, compliance and IT operations teams to detect and respond to threats, reduce their attack surface, and ensure regulatory compliance.
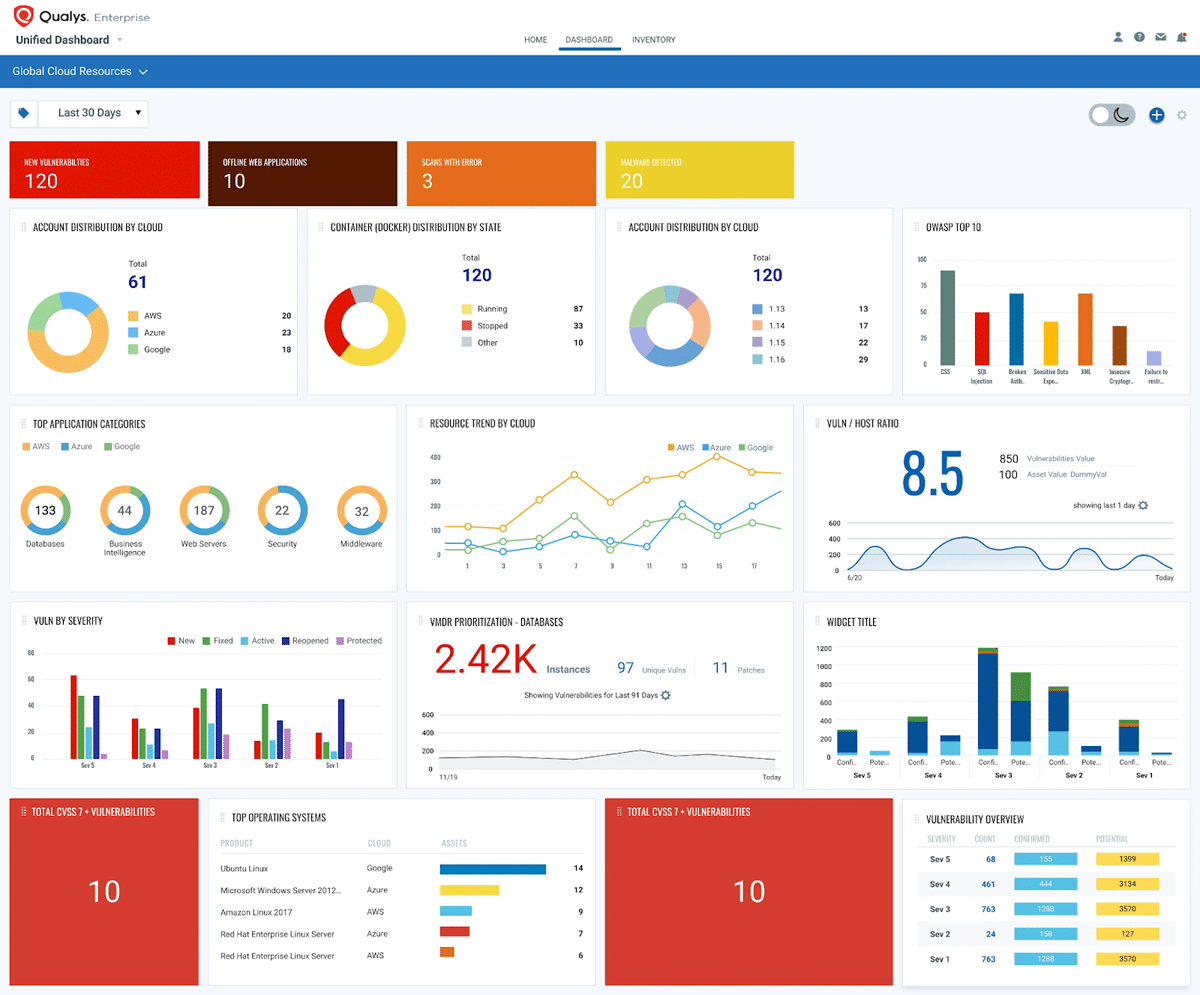
Qualys helps organizations automatically identify all known and unknown assets in their global hybrid IT environment, providing a complete, categorized inventory enriched with details such as vendor lifecycle information. The platform also provides continuous security monitoring, vulnerability assessments, malware detection and patching capabilities.
The Qualys cloud platform has multiple modules that enable different facets of cloud security, including compliance, vulnerability scanning, and cloud workload protection.
Key Features:
- Vulnerability detection: The Web Application Scanning module provides automatic scanning capabilities for web apps to help detect and rank security vulnerabilities.
- Compliance: Qualys offers multiple modules for compliance use cases, including the PCI-DSS module that scans all devices to identify compliance status.
- Configuration: The Policy Compliance module offers automated security configuration assessments across on-premises and cloud assets.
- Asset detection: Qualys automatically identifies all known and unknown assets on your global hybrid IT environment — on-premises, endpoints, clouds, containers, mobile, OT and IoT.
- DevOps: Integrates with CI/CD toolchains such as Jenkins and Azure DevOps.
- Security: The Qualys platform also includes a range of threat detection and response protections, web application firewalls, container security, and more.
Pros
- Patch and vulnerability management
- Ease of use
- TotalCloud solution offers fast remediation with no-code, drag-and-drop workflows
- Users find Qualys solutions scalable
- Enables DevOps team to test for vulnerabilities throughout their development cycle
- Public cloud infrastructure and workload inventories
Cons
- Users report false positives
- Support could be better
Pricing
Qualys doesn’t advertise pricing on its website and notes that pricing depends on the number of apps, IP addresses, web apps and user licenses.
See the Top Vulnerability Management Tools
Palo Alto Networks: Best for Cloud Workload Protection
Palo Alto Networks boasts a comprehensive product portfolio for protecting against cyberattacks — and the cybersecurity leader has brought that same comprehensive approach to its cloud security offerings.
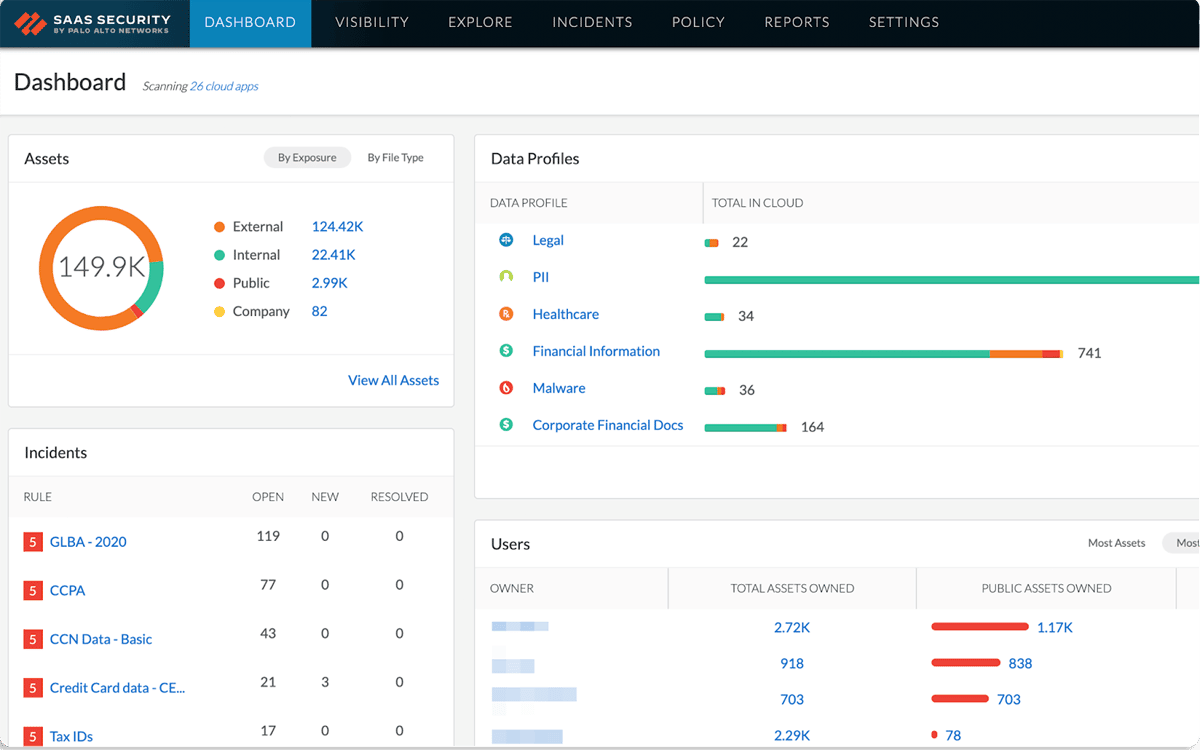
Palo Alto Networks has one of the most comprehensive cloud native security platforms in the market in Prisma Cloud, with deep capabilities to help organizations manage workload security. The company’s solutions are designed to provide visibility and control over applications, users, and content, helping to reduce the risk of a data breach.
Key Features:
- Cloud native: The Prisma Cloud platform is a new approach that Palo Alto Networks defines as a Cloud Native Security Platform (CNSP).
- Broad protection: Prisma integrates components from multiple companies that Palo Alto Network has acquired in recent years, including evident.io, RedLock, PureSec and Twistlock, providing container and cloud workload policy, threat detection and control.
- Visibility: Full cloud workload visibility, including serverless functions, is a key differentiator for Palo Alto, with capabilities to secure an end-to-end cloud-native deployment.
- Cloud app protections: Vulnerability management and runtime protection against threats are other key features of the Prisma Cloud offering.
Pros
- Palo Alto has leveraged its many years of network security innovations in developing solutions for SASE, CNAPP, cloud-delivered security services, and more
- Protects hosts, containers, and serverless environments on any cloud platform
- Prisma Cloud maintains support for over 20 compliance frameworks
- Offers more than 700 pre-built cloud security policies
Cons
- Users report that Palo Alto solutions are pricey
- Support could be better
Pricing
Palo Alto Networks does not publish prices on its website, and buyers should contact the company for custom quotes tailored to their specific needs.
The company will consider various factors to provide an accurate quote, including the number of users, the type of product, and any additional features or services. Additionally, Palo Alto Networks offers various pricing models such as subscription, perpetual licensing, and metered usage to meet the different needs of customers.
See the Top Cloud Workload Protection Platforms
Symantec: Best for CASB
Symantec, one of the most recognizable names in cybersecurity, has been part of Broadcom since 2019. The company provides a data-centric hybrid security platform that helps enterprises protect their data, networks, applications, and devices from threats.

Symantec offers endpoint security, cloud security, email security solutions, and threat intelligence services. Symantec has multiple cloud security functions within its portfolio, including workload protection and the CloudSOC CASB.
Key Features:
- Workload protection: The Cloud Workload Protection suite can identify and evaluate security risks for workloads running in the public cloud.
- Compliance: Cloud Workload Assurance offers automatic compliance reporting and remediation, including the ability to benchmark security posture for a given configuration.
- CASB: The CloudSOC CASB is one of the leading cloud access security broker technologies, according to analyst firms Forrester and Gartner.
- Endpoints: Symantec endpoint security can detect, block, and remediate known and unknown threats across laptops, desktops, tablets, mobile phones, servers, and cloud workloads.
Pros
- Simplified and centralized management
- Prevents inbound and outbound web-based threats
- Provides automated cloud reporting, compliance, and remediation for IaaS
- Benchmark security postures and configurations against standards such as CIS, NIST, SOC2, ISO/IEC, PCI and HIPAA
Cons
- Technical support could be better
- User interface could be improved
Pricing
Symantec doesn’t list product pricing on its website, as it can vary widely depending on the size of the organization, number of licenses, and other factors. Customers should contact the company directly through its website or partners.
Tenable: Best for Vulnerability Management
Tenable provides cybersecurity software and services that help organizations better understand and reduce cyber exposure. It provides security solutions such as vulnerability management, compliance, and file integrity monitoring, and has also turned its vulnerability management expertise toward the cloud.
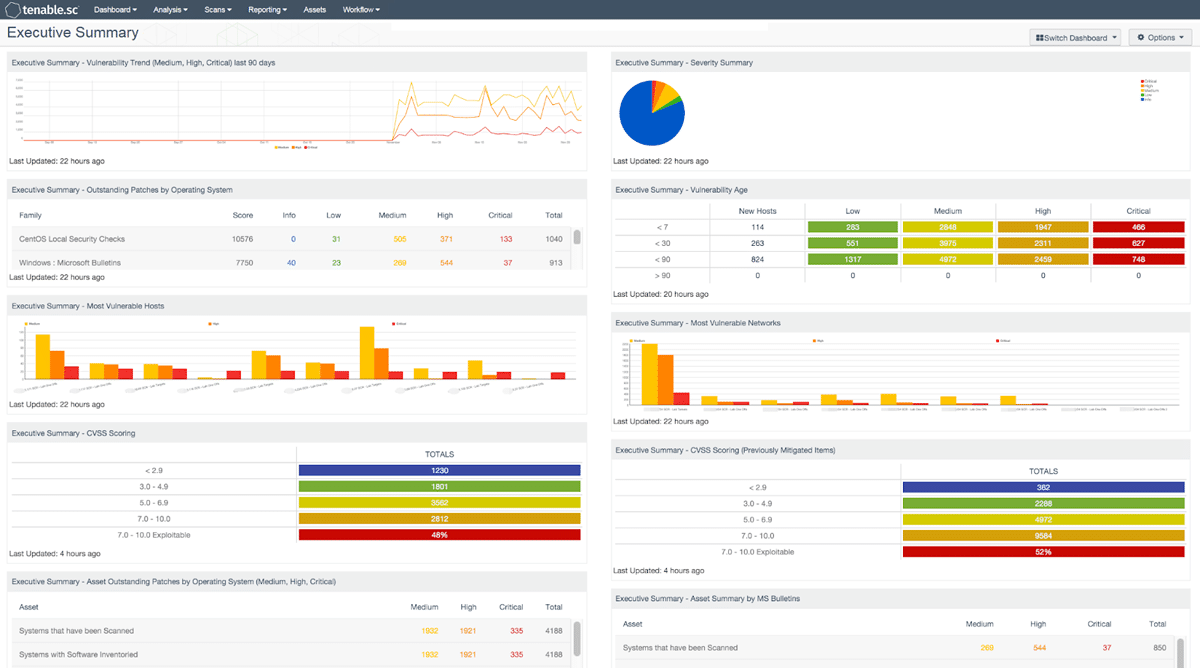
Tenable’s products include:
- Tenable.io, a cloud-based platform for managing security risk
- Tenable.sc, a cloud-based Security Center for visibility and threat response
- Tenable.ot for automated asset identification and classification
- Tenable.cs, a unified cloud security platform that provides organizations with continuous visibility and control of their cloud infrastructure
Tenable has a long history in the vulnerability management space, which now extends into the cloud to help organizations of all sizes protect their workloads.
Key Features
- Cloud protection: Tenable has multiple services on its cloud-based tenable.io platform, including web application scanning, container security and asset management.
- Vulnerability management: The key differentiator for tenable.io is identifying assets and vulnerabilities, giving organizations visibility into their cloud risk.
- Configuration management: The ability to identify potential misconfigurations is also an important feature.
- Broad coverage: Tenable has assessed over 72K vulnerabilities with over 147K plugins.
Pros
- Easy to deploy
- Clear and easy-to-navigate dashboard
- Users find the interface friendly
- Transparent pricing
Cons
- Reporting could be improved
- Support could be better
Pricing
Tenable is generally pretty open about pricing, from its Nessus vulnerability scanning product up through its cloud offerings. Tenable also offers a free trial for all its products, so you can try them before you commit to a plan. Tenable pricing plans include:
Tenable.io vulnerability management
Tenable.io vulnerability management’s pricing plan is based on the number of assets you need to monitor: The more assets, the more you will pay. The minimum number of assets for the Tenable.io vulnerability management plan is 65.
- 1 Year (65 assets) – $2,934.75
- 2 Years (65 assets) – $5,722.76
- 3 Years (65 assets) – $8,364.04
Tenable.io web app scanning
- 5 FQDNs – $3,846.35
Trend Micro: Best for Hybrid Cloud Security
Trend Micro is a global leader in hybrid cloud security and provides an integrated and automated approach for protecting data, users, and applications, no matter where they are located. Trend Micro Hybrid Cloud Security solutions provide protection across on-premises and cloud environments.
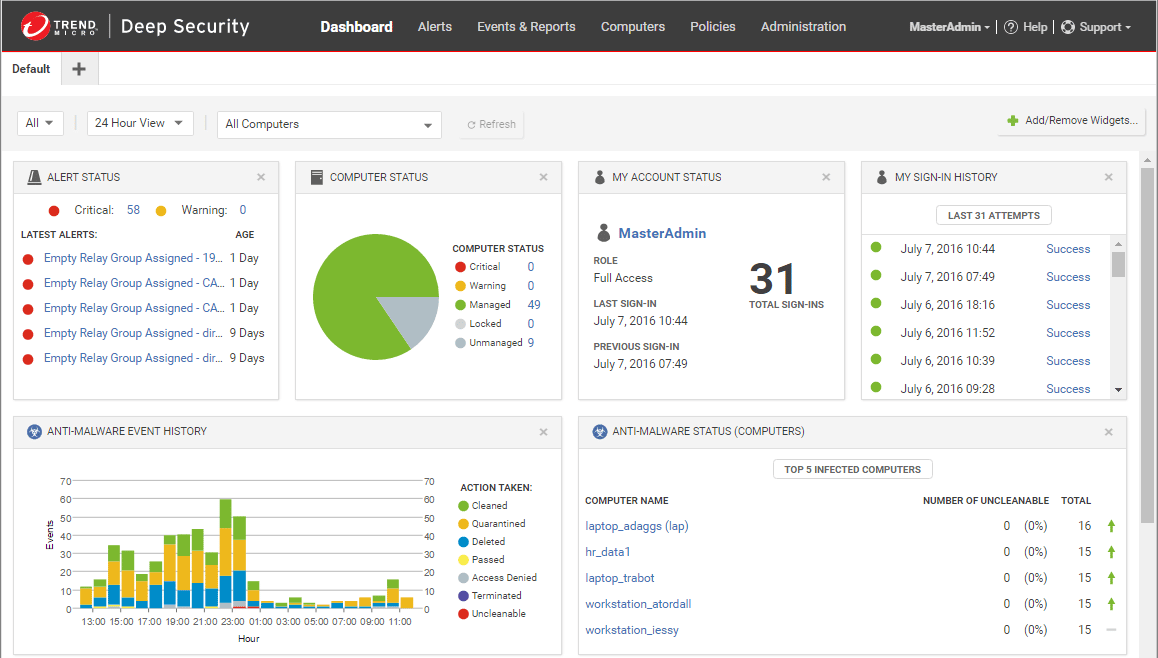
Trend Micro offers advanced security capabilities such as cloud workload protection, network security, file storage protection, application security, and open-source security. It also provides visibility and control over the entire IT environment, allowing organizations to identify, assess, and remediate threats.
Trend Micro is well positioned as a leader in hybrid cloud security, helping organizations to unify policies across both on-premises and public cloud deployments.
Key Features:
- Integrated security: The Trend Micro Cloud One platform integrates workload, storage, network security, and compliance capabilities.
- Hybrid workloads: The workload security feature is a key differentiator for Trend Micro, as it extends the same policy and protection to multiple deployment modalities, including on-premises, private and public cloud workloads.
- Patching: Trend Micro also provides virtual patching for vulnerabilities to help limit risks as rapidly as possible.
- Templates: Security can be codified with templates aligned with leading security standards and deployed with simple AWS CloudFormation templates.
Pros
- Offers runtime protection for workloads, including virtual, physical, cloud, and containers
- Users find the solution easy to scale
- Efficient support
- Secures cloud file and object storage services
Cons
- Users report that the solution can be pricey
- Reporting functionality could be improved
Pricing
Trend Micro does not advertise its prices online and prefers that customers contact its sales team to discuss pricing and tailor a solution to the customer’s needs.
However, Trend Micro offers a 30-day free trial of its solutions, so customers can try the solutions before they purchase.
VMware: Best for Multi-Cloud Environments
VMware is a leading provider of virtualization and cloud computing solutions. The company has used that leverage to assemble an impressive array of cloud security solutions to help organizations protect their data and infrastructure in the cloud.
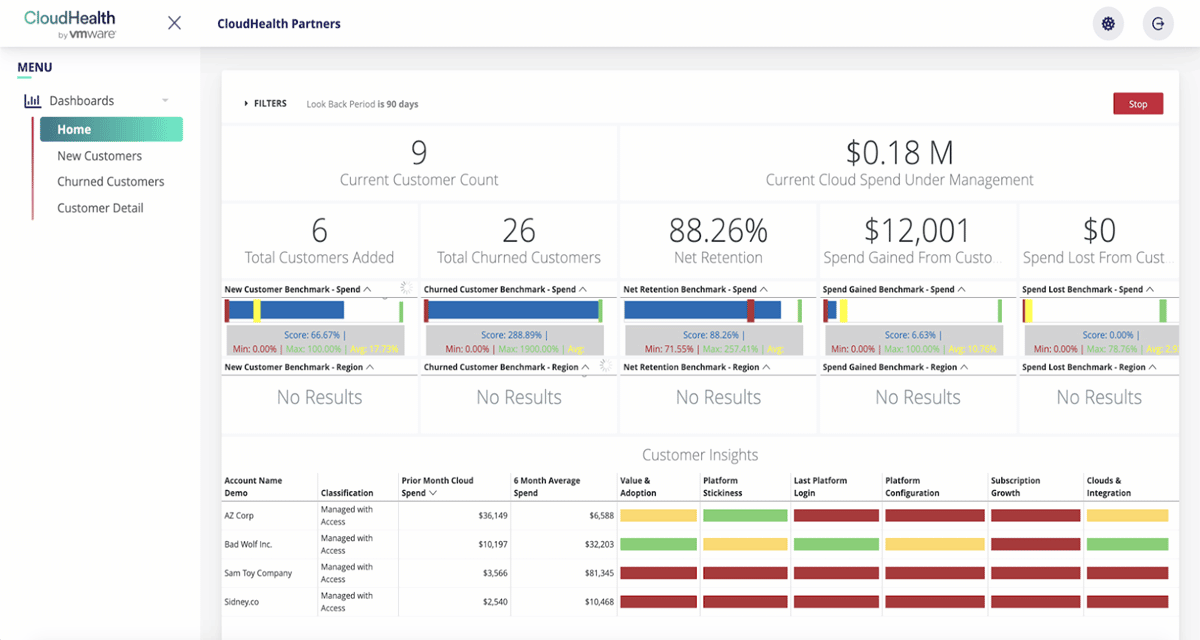
VMware has a global network of SASE points of presence (PoPs) that secure cloud applications and workloads, aligning security and performance. The virtualization pioneer has multiple capabilities for cloud security, including its secure state and CloudHealth products.
Key Features:
- Integrated security: VMware acquired CloudHealth in 2018 and expanded it in 2019 to provide deeper integration with VMware workloads alongside the public cloud.
- Compliance: CloudHealth provides cloud governance features to help organizations align security and regulatory compliance.
- Configuration security: VMware Secure State delivers multi-cloud security posture management that focuses on configuration security.
- Risk assessment: Secure State is particularly good at providing insights into security risks due to connections between cloud objects and services, which can represent a great deal of risk to an organization.
Pros
- Offers visibility, control and compliance
- Reduces CapEx by as much as 75%
- Advanced security for private, public and hybrid cloud workloads
Cons
- The interface could be improved
- Pricey
Pricing
The exact price of VMware products can vary depending on your business’s specific needs and requirements. To get an accurate quote, contact sales directly.
Netskope: Best Overall Cloud Security
Netskope is a cloud security company that provides organizations with enhanced visibility, control, and protection of their cloud applications. The company offers an integrated suite of cloud security solutions built to secure enterprise cloud-based data, applications, and users. Netskope is one of the highest-valued private cybersecurity companies — and has used its funding to assemble an impressive array of cloud security offerings.
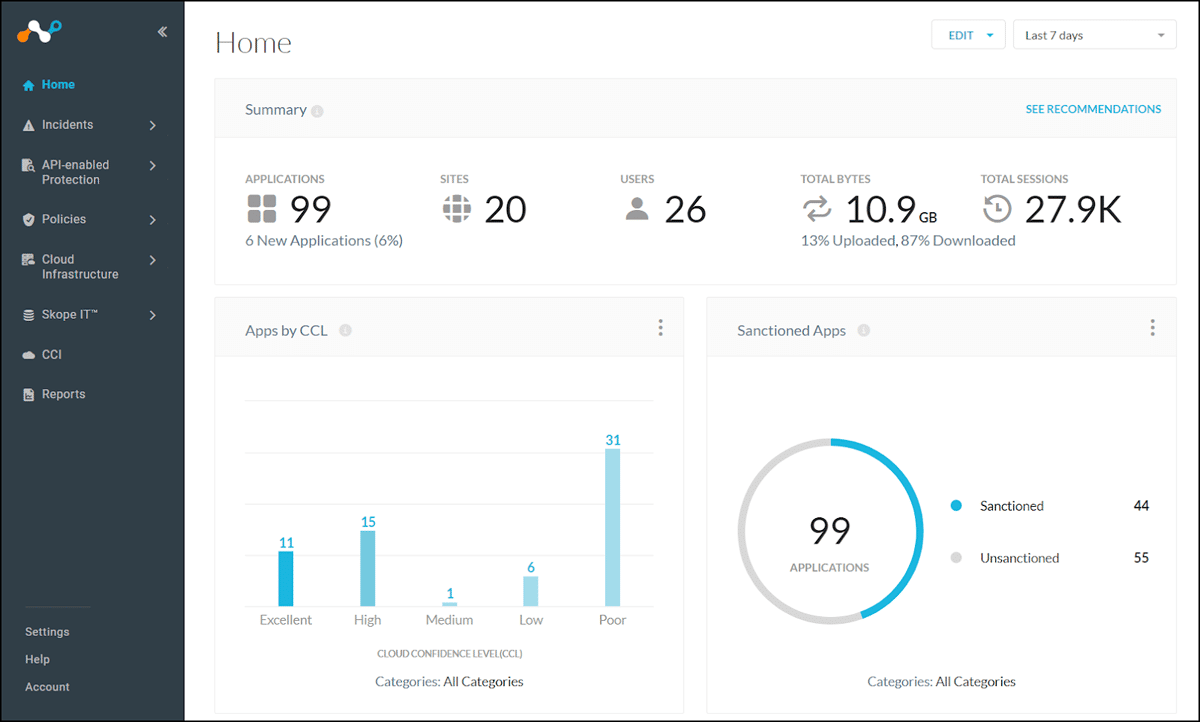
Netskope’s core products include security service edge (SSE), next-gen secure web gateway (SWG), cloud access security broker (CASB), private access for zero trust network access (ZTNA), data loss prevention (DLP), remote browser isolation, SaaS security posture management, and IoT security. Netskope’s analytics engine also gives visibility into user behavior and suspicious activity across the cloud environment.
Key Features:
- Intelligent SSE: Netskope consolidates the capabilities of SWG, CASB and ZTNA to provide comprehensive security across the web, SaaS and public cloud and data centers.
- Analytics and insights: It provides visibility into enterprise cloud usage and identifies potential security risks.
- Compliance: Netskope helps enterprises meet compliance requirements by enforcing data loss protection, access policies, and encrypting sensitive data.
- Performance: Offers 99.999% uptime and availability as well as latency SLAs for traffic processing.
- IoT security: Netskope provides visibility into all enterprise-connected devices and secures them via context-driven classification, risk assessment, segmentation, and access control.
- SSL/TLS inspection: Monitors encrypted web traffic and cloud services for potential data theft, malware, and advanced threats, such as cloud phishing and payload hosting.
Pros
- Provides visibility into enterprise cloud application usage and risks
- Netskope zero trust principles enable remote employees to access the web, cloud, and private applications securely
- Provides continuous monitoring to detect user behavior anomalies, app risks, and unknown data movement
- Reduced attack surface
- Strong SASE offerings
Cons
- The customer support process could be improved
- Users report that Netskope solutions can be pricey
Pricing
Netskope doesn’t reveal the price of its products. Potential buyers can request a demo to explore product capabilities and contact sales for custom quotes.
Zscaler: Best for Advanced Threat Protection
Zscaler is a cloud-based security company that protects users, data, and applications from cyberattacks. Its services cover the full spectrum of security needs, including network security, web application firewalls, intrusion prevention, malware protection, zero trust and data loss prevention, to secure access for remote users and compliance with industry regulations. Zscaler provides SWG, ATP, cloud sandboxing, and CASB services to protect users, devices, and data from cyber threats. Detection, deception technology and ease of use are just a few features praised by users.
Key features
- Contextual alerts: Provides alerts that give insight into threat scores, affected assets, and severity.
- AI-powered phishing detection: The solution detects and blocks patient-zero phishing pages using advanced AI-based detection.
- Browser isolation: With Zscaler internet access, you can create a virtual air gap between users, the web, and SaaS to mitigate web-based attacks and prevent data loss.
- Segmentation: Zscaler private access connects users directly to private apps, services, and OT systems with user identity-based authentication and access policies. It also allows direct connection to IIoT/OT devices for remote operators and admins.
Pros
- AI-powered advanced threat protection
- Broad cloud security platform
- Strong deception technology
- Ease of use
Cons
- Reporting feature could be improved
- Users report that the solution can be pricey
Pricing
Potential customers should contact the Zscaler sales team for custom quotes.
How We Evaluated the Top Cloud Security Companies
In evaluating the cloud security market, we examined the breadth and quality of each vendor’s products and services, customer reviews, analyst reports, market traction and growth, independent test reports, pricing, and more.
Understanding Cloud Security Technologies
When considering cloud security products, it’s important to recognize and understand the different categories of solutions that are available to help organizations reduce risk and improve security. Among them are:
- Cloud access security brokers (CASB): A primary category of cloud security solutions is cloud access security broker (CASB) platforms, which monitor activity and enforce cloud access security policies. For more on CASB vendors, see our guide to the top CASB vendors.
- Cloud workload protection platforms: Cloud workload protection technologies (CWPPs) work with both cloud infrastructure and virtual machines, providing monitoring and threat prevention features.
- Cloud-native platforms: Cloud-native application protection platforms (CNAP or CNAPP) combine cloud security posture management (CSPM) and CWPP in a single, unified solution to provide visibility and security control management across all cloud functions.
- SaaS security: Multiple types of security technologies are also delivered as a service from the cloud, to help secure both on-premises and cloud workloads.
It’s also important to note that each of the major public cloud providers (Amazon Web Services, Google Cloud Platform and Microsoft Azure) also have their own native cloud security controls and services that organizations can enable. Understanding your responsibilities on these platforms under the shared responsibility model of cloud security is critically important.
Choosing a Cloud Security Company
With the wide variety of options available for users, it can often be a confusing and time-intensive task to select an appropriate offering. When looking at cloud security, there are several key considerations:
- Scope: It’s important to understand what’s at risk and what the organization is trying to protect. Often one or more services will be needed to protect an entire cloud deployment.
- Policy Integration: Making sure that a given cloud security solution can integrate with existing policy systems, whether they are on-premises or in the cloud, is important for enabling a uniform policy for an enterprise.
- Multi-Cloud Protection: The ability to work across multiple cloud providers and different types of deployments is important, since few organizations want to be locked in to any one vendor or cloud.
Bottom Line: Cloud Security Companies
As companies increasingly store and process critical data and assets in the cloud, it’s important that they have the right cloud security tools to secure those assets.
Cloud security companies give businesses the security solutions to meet those needs, ranging from risk assessment, auditing, data encryption, user authentication, access control, and more. They can also advise on how best to secure cloud systems and protect data.
Read next: 12 Cloud Security Best Practices
This updates a March 11, 2021 article by Sean Michael Kerner.