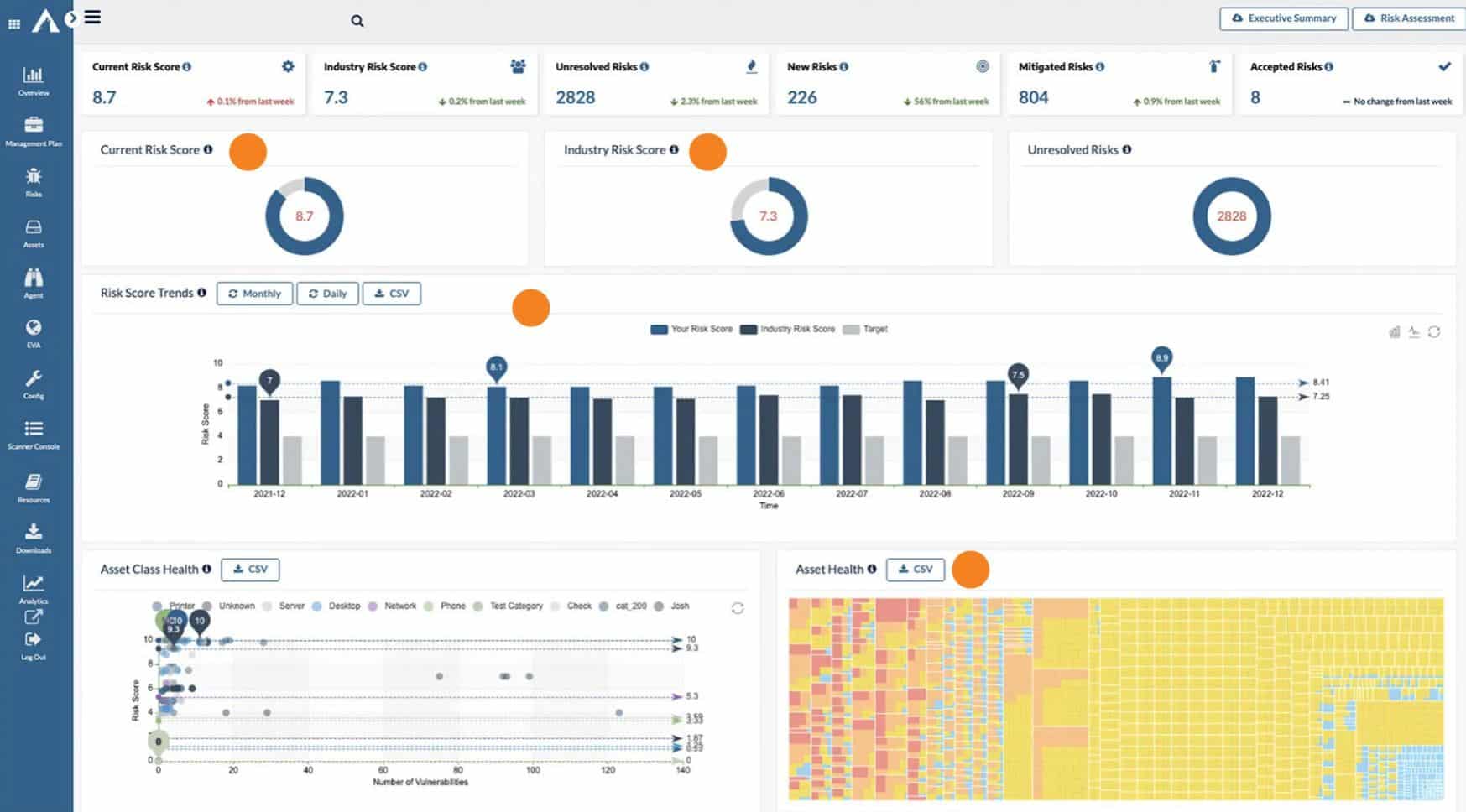
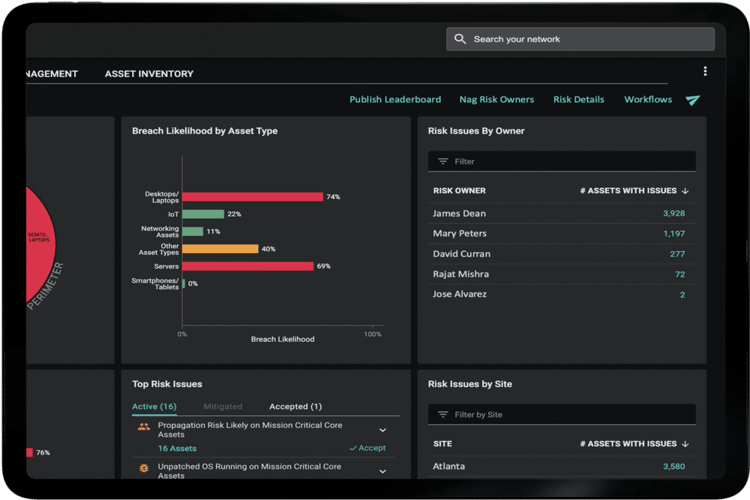
Vulnerability management tools go well beyond patch management and vulnerability scanning tools by discovering security flaws in network and cloud environments and prioritizing and applying fixes.
Many IT departments struggle to stay on top of security vulnerabilities, and many don’t even know every IT asset they own, making comprehensive vulnerability management solutions an increasingly critical cybersecurity tool.
Leading Vulnerability Management Solutions
1 Intruder
Intruder is the top-rated vulnerability scanner. It saves you time by helping prioritize the most critical vulnerabilities, to avoid exposing your systems. Intruder has direct integrations with cloud providers and runs thousands of thorough checks. It will proactively scan your systems for new threats, such as Spring4Shell, giving you peace of mind. Intruder makes it easy to find and fix issues such as misconfigurations, missing patches, application bugs, and more. Try a 14-day free trial.
Best Vulnerability Management Solutions
Jump ahead to:
- Qualys
- Rapid7
- Tenable
- Tripwire
- GFI LanGuard
- BreachLock
- WithSecure
- Holm Security
- Digital Defense
- Arctic Wolf
- Balbix
- Microsoft
We examined the market for vulnerability management tools, looking at product features and applications, user perspectives, ideal use cases, and pricing information. While no list is perfect — there may well be a vendor not on this list who meets your requirements better — here we focused on features and capabilities that stood out from the crowd, such as unique value-adds, scalability, and automation. Out of a market with a number of strong offerings, here are a dozen of the best.
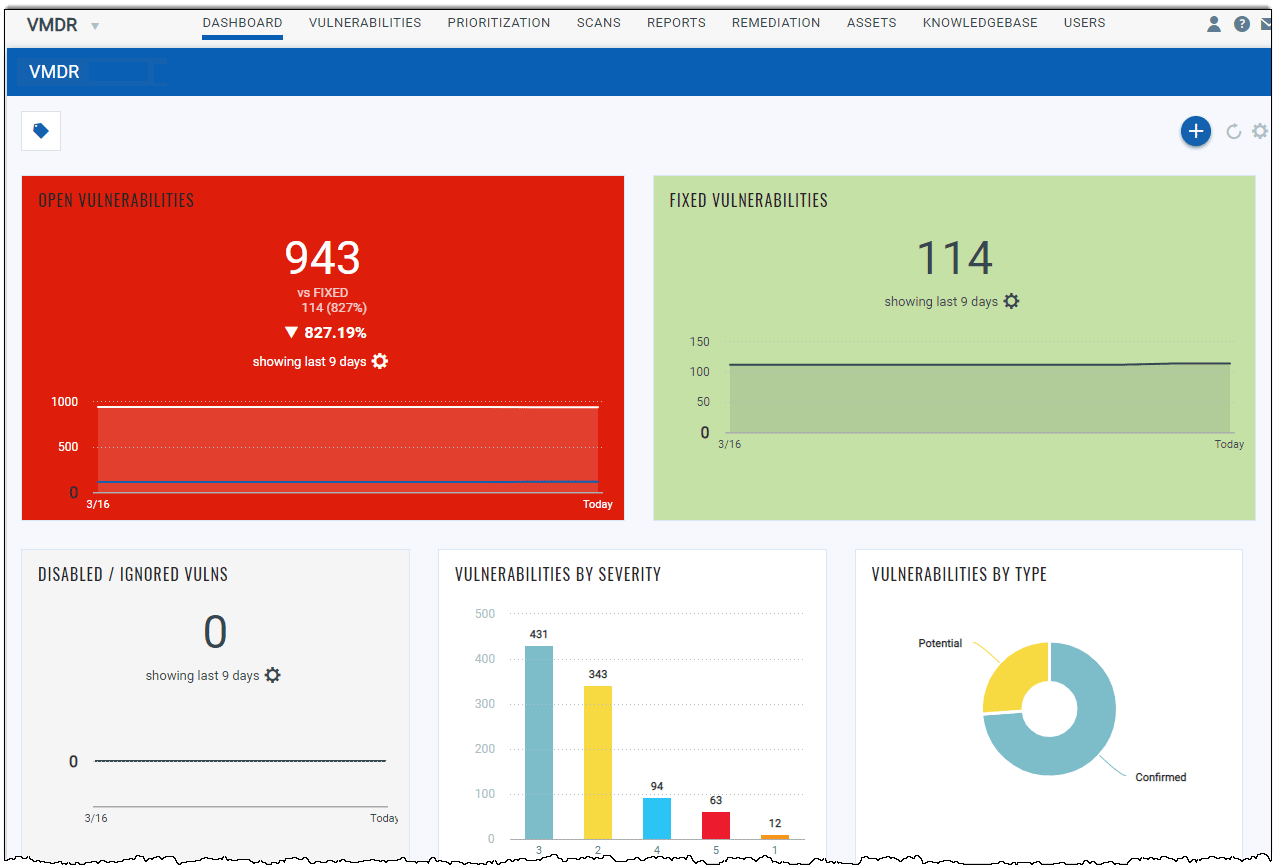
Qualys VMDR 2.0
Best for: Organizations with complex environments and remote users seeking broad vulnerability management capabilities.
Qualys VMDR 2.0 with TruRisk is an enterprise-grade cyber risk management solution. The platform is simple to use and deploy across complex hybrid environments. By providing options to protect remote users, Qualys VMDR 2.0 is among the most popular vulnerability management platforms on the market today, given the increasingly remote-first global workforce.
Key Differentiators
- Powered by the Qualys Cloud Platform, the vulnerability management tool enables you to prioritize assets, groups of assets, and vulnerabilities based on business risk.
- Proactively alleviate risk exposure and keep track of risk reduction over a period with TruRisk.
- Qualys Flow allows you to automate and orchestrate operational tasks for vulnerability management and patching.
- By leveraging insights from 180k+ vulnerabilities that are sourced from more than 25 threat sources, you’re better prepared to prevent attacks from happening.
- Identify all IoT, OT, and IT assets for a comprehensive, categorized inventory. This includes your on-premises device and application, certificate, cloud, container, and mobile device inventory.
- Automatically detect critical misconfigurations and vulnerabilities per CIS benchmarks, by the asset.
- Rule-based integrations with ITSM tools like JIRA and ServiceNow enable you to swiftly remediate threats at scale.
Pricing: Qualys VMDR 2.0 with TruRisk is priced on a per-asset basis. You can either sign up for a free trial or request a quote from the Qualys sales team.
Rapid7 InsightVM
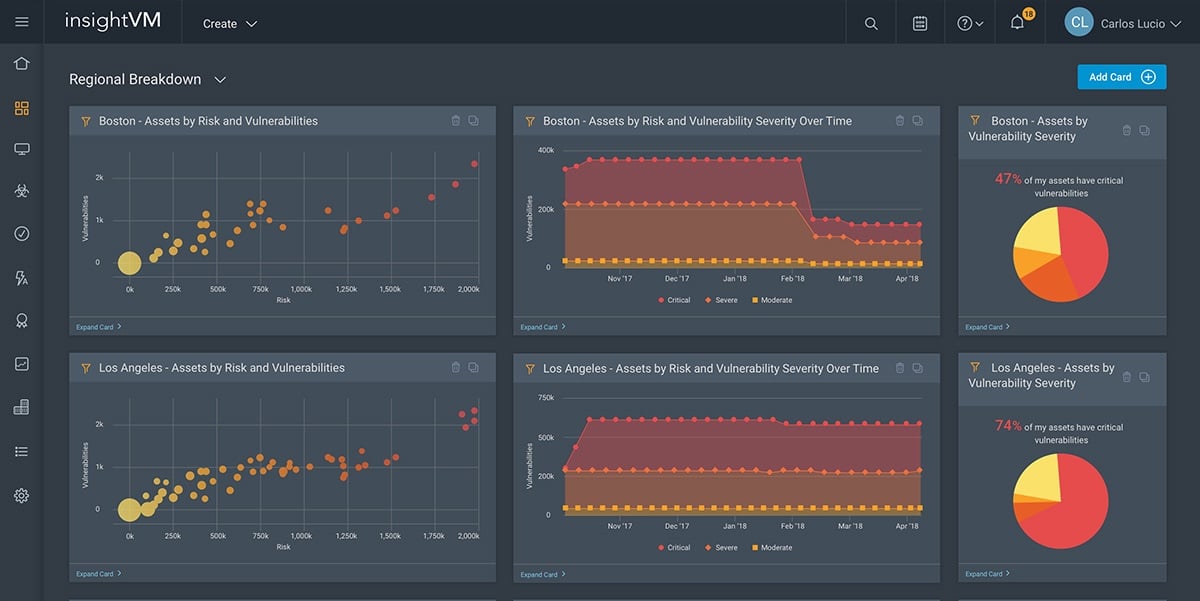
Best for: Smaller businesses and organizations without a sophisticated security team.
Rapid7 InsightVM is a powerful and scalable vulnerability management solution that provides broad enterprise security. One of the most sought-after features of the product is risk prioritization with step-by-step instructions for effective remediation. As an additional benefit, the Rapid7 customer support team is among the best in the business. Good value and automation make InsightVM particularly useful for smaller businesses and those lacking sophisticated security teams, but even organizations with greater expertise could benefit from its risk identification and prioritization capabilities.
Key Differentiators
- Rapid7 InsightVM enables you to identify risks across all your endpoints (including remote workers and sensitive assets) and virtualized and cloud infrastructure.
- Prioritized risks with step-by-step instructions enable IT and DevOps to effectively remediate all vulnerabilities.
- View risks in real time from your customizable and interactive dashboard and track the progress of your security program.
- The Real Risk Score mechanism provides an actionable, 1-1,000 scale for vulnerabilities, enabling real risk prioritization.
- With IT-integrated Remediation Projects, security teams can track and assign remediation duties in real time.
- Project Sonar provides active Attack Surface Monitoring, by gaining insights into global exposure to common vulnerabilities.
- Integrated Threat Feeds provide a dynamic outlook of the threats that are most relevant to you, enabling quick reaction time to potential vulnerabilities.
- The cloud-based vulnerability management tool provides automation-assisted patching.
Pricing: You can get a free trial of Rapid7 InsightVM by filling out a simple form. For a minimum of 250 assets, the platform costs $2.19/asset/month.
Tenable Nessus
Best for: Small businesses, developers, pen testers, and consultants.
Tenable Nessus is a trusted vulnerability assessment platform, built for the modern attack surface. With 0.32 defects per 1 million scans, Tenable Nessus boasts of the industry’s lowest (best) false positive rate with six-sigma accuracy. SMBs, developers, pen testers, and consultants will find Nessus Expert most useful, but features like external attack surface scanning could have broad appeal.
Key Differentiators
- The vulnerability management tool is fully portable and can be deployed on any platform, including Raspberry Pi.
- Along with traditional IT assets, find and assess your internet-connected attack surface for comprehensive, all-around protection.
- Dynamically compiled plugins improve scan efficiency and performance.
- Discover security issues as part of the software development lifecycle (SDLC) as soon as possible.
- With industry-leading vulnerability coverage, zero in on risks that matter the most.
- With over 450 pre-configured templates, speedily understand where you have threats.
- Reporting and troubleshooting capabilities can be customized to meet particular needs and are exportable in multiple formats.
- Live Results automatically carries out an offline vulnerability assessment with each plugin update. You can then simply run a scan to confirm the presence of the vulnerability, thereby accelerating the process of detection and remediation.
- With the help of the resource center, receive guidance through the vulnerability management process with actionable tips on steps to take next.
Pricing: A 1-year product license costs $4,990 for five domains, and a 7-day free trial is available.
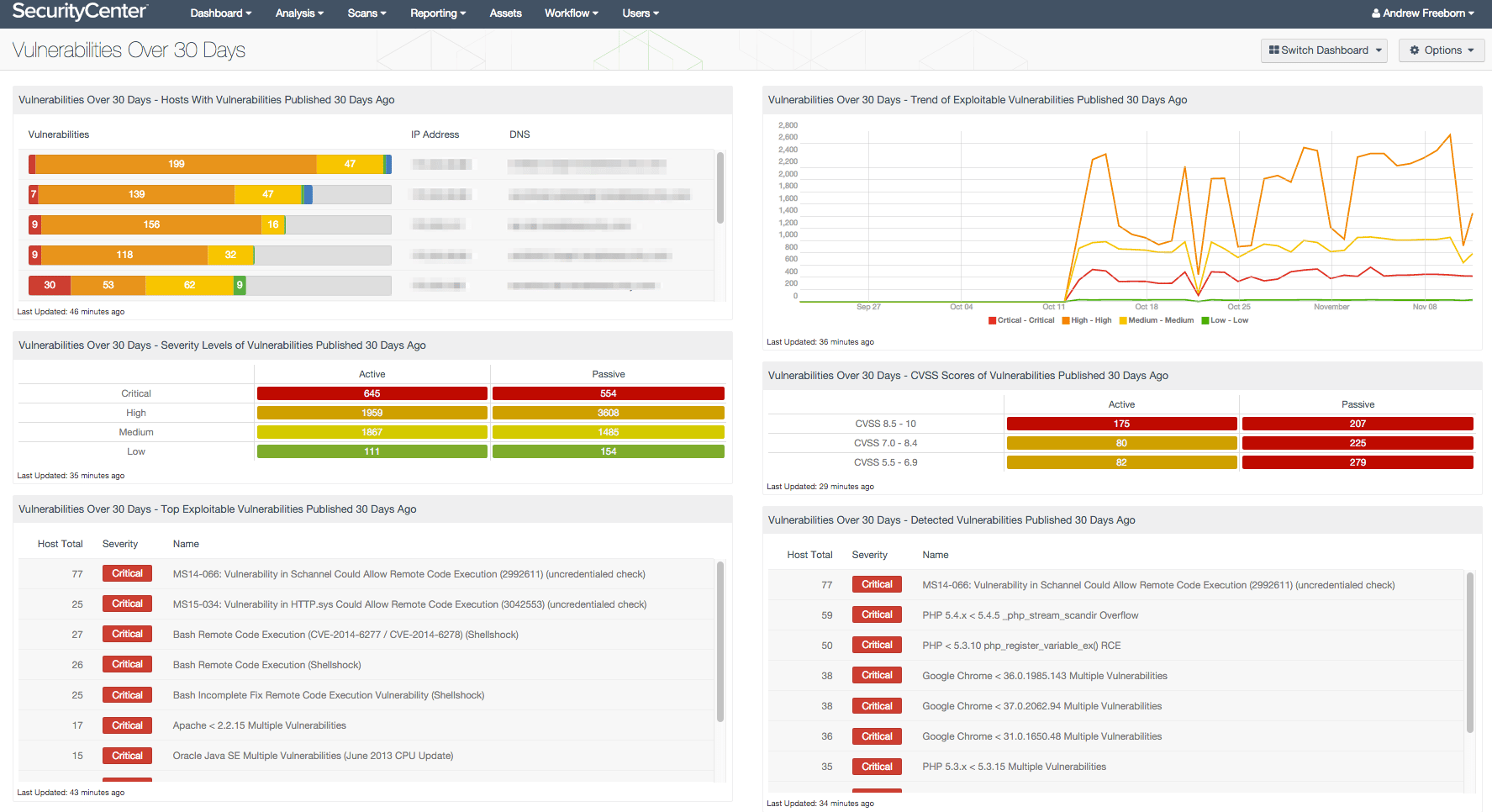
Tripwire IP360
Best for: Large organizations requiring greater security.
Tripwire IP360 is a holistic vulnerability management solution that provides 360-degree on-premises and cloud protection, as the name suggests. The platform’s prioritized vulnerability risk scoring mechanism is its standout feature, along with its scalability and ease of integration with existing solutions. Scalability and Adaptive Threat Protection makes Tripwire an interesting choice for larger organizations requiring greater security, but automation features could interest others too.
Key Differentiators
- Tripwire IP360 provides complete network visibility, including all devices and associated vulnerabilities, applications, and operating systems.
- Prioritized vulnerability risk scoring cuts through the noise and provides quick, actionable results.
- Tripwire IP360 ranks vulnerabilities numerically on the basis of age, ease of exploit, and impact.
- The platform’s unique fingerprinting technology curtails scans to relevant application and device types.
- With Tripwire IP360’s open APIs, integrate vulnerability management with asset management, help desk, intrusion detection/prevention, and SIEM solutions, thereby enabling automation.
- Centralized management offers an easy-to-use web interface for workflow, reporting, configuration, and administration.
- The platform is available as a managed service for those who are short-staffed/time-constrained–Tripwire ExpertOps. The service provides cloud-based infrastructure and personalized consulting, is easy to use, and comes with a subscription model and low TCO.
Pricing: Pricing available upon request.
GFI LanGuard
Best for: A good choice for budget-conscious organizations in need of dependable vulnerability protection.
GFI LanGuard is an enterprise-class vulnerability scanning, patch management, and network auditing tool. The solution gets high marks for its patch management capabilities and compliance features and provides all that you expect of a solid vulnerability management solution.
Key Differentiators
- Manage and sustain end-to-end protection of hybrid networks, with automatic visibility into each element.
- You can group network elements for more efficient management and view each element/group from a central management dashboard.
- The solution is relatively easy to use and deploy.
- Scan your network to identify missing patches in third-party software and web browsers.
- By using a list of over 60,000 known issues, identify non-patch vulnerabilities as well.
- Deploy patches automatically and centrally. Alternatively, you can deploy agents on individual machines.
- Install security patches to fix bugs and help applications run better.
- Automated network security reports help you exhibit compliance with requirements such as SOX, HIPAA, DSS, and PCI.
Pricing: You can request a free trial or fill out a form to get in touch with a GFI LanGuard expert for pricing details.
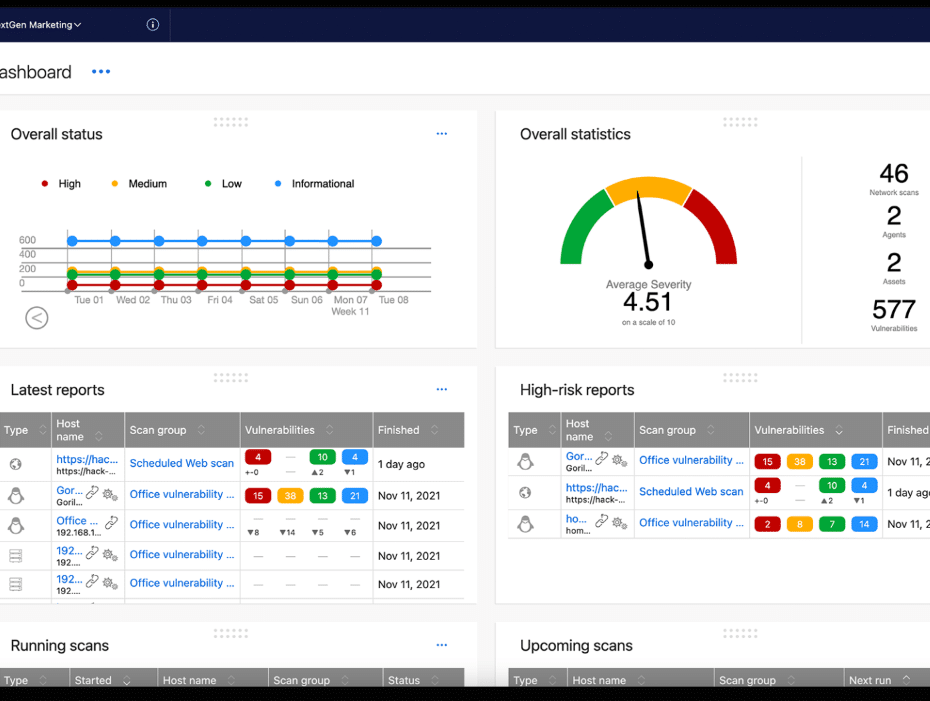
BreachLock Vulnerability Assessment
Best for: DevSecOps and pentesting uses.
BreachLock Vulnerability Assessment is a cloud-based and easy-to-use vulnerability assessment platform that covers all company infrastructure. You can access the platform using any browser, with access protected by 2FA. Additionally, stellar customer support is a big plus, as you can interact with security professionals and support staff directly. BreachLock hosts its SaaS-based solution on AWS and could find favor with organizations of all sizes, but cloud, DevSecOps and pentesting features stand out the most.
Key Differentiators
- Scheduled vulnerability assessment scans run automatically and at regular intervals.
- On-demand scans can be run on one or more assets with a single click.
- The platform’s automated vulnerability scanning and manual penetration capabilities are built with the cloud in mind.
- From the BreachLock cloud platform, vulnerability assessment offerings fit for SaaS, PaaS, and IaaS are delivered.
- The vulnerability management solution is suitable for all cloud environments.
- Quick and reliable vulnerability detection enables you to detect and fix the latest security risks.
- AI and ML algorithm automation helps reduce false positives and look into potential threats at regular intervals.
- Overall, the platform is rapid, scalable, and effective.
Pricing: Users consider BreachLock VM to be one of the best values on the market. Schedule a discovery call to obtain a product quote.
WithSecure Elements Vulnerability Management
Best for: The security needs of small businesses.
WithSecure Elements Vulnerability Management is an easy-to-deploy vulnerability scanner that covers the breadth of a network, assets, compliance, and the deep web. The vulnerability scanner is a module of the Elements platform, which brings together vulnerability management, continuous behavioral analytics, dynamic threat intelligence, and automated patch management. WithSecure offers a relatively cost-effective cloud-based vulnerability scanner with strong automation features, making it best suited for the security needs of SMBs.
Key Differentiators
- The module provides effective, all-around protection from advanced attacks and ransomware.
- Web crawling technology covers the entire attack surface, including the network, assets, and the deep web.
- WithSecure Elements Vulnerability Management automatically reports activities such as phishing sites, third-party scams, and brand violations.
- The highly automated nature of the module cuts down on time-consuming manual work, potentially proving to be cost-effective in the long run.
- With the help of a centralized management dashboard, monitor the current status of incidents and vulnerabilities and perform vulnerability scans, with help from automated detection and reporting.
- The vulnerability scanner meets PCI DSS compliance requirements.
- The tool can be used in the cloud or as a fully outsourced managed service.
Pricing: Contact the WithSecure sales team for product pricing details.
Holm Security VMP
Best for: Small businesses that want to incorporate employee security awareness too.
Holm Security VMP is a next-generation vulnerability management platform that helps detect vulnerabilities across your enterprise network and human assets in a single integrated platform. Among the platform’s standout features is its phishing module, which is comprehensive and helps build a “human firewall” of sorts. Holm Security VMP is preferred by SMBs thanks to its value and features like phishing awareness, but its broad capabilities also find application in large-scale organizations, governmental facilities, personal security, and educational facilities.
Key Differentiators
- Holm Security VMP leverages threat intelligence, enabling users to understand the complete nature of potential threats by flagging critical vulnerabilities and high-risk users.
- The platform works to secure the entire modern attack surface, from cloud infrastructures such as SaaS, IaaS, and PaaS, to operational technology, containers, and human assets.
- Identify vulnerabilities, assess threats, and prioritize remediation for each asset across your cloud infrastructure and corporate network.
- Offers core capabilities such as phishing awareness, vulnerability management, and cloud security posture management (CSPM) in a single tool.
- The vulnerability assessment tool’s phishing module includes several out-of-the-box phishing scam scenarios and simulations, behavioral reports, and complete employee awareness training.
- Leverage Security Center is a simple-to-use, web-based control panel that offers thorough insights and helps manage detected vulnerabilities.
- Utilize customizable dashboards and reports for smart insights into vulnerabilities and threats.
- Connects SIEM, ticketing, CMDB, notifications, and CI/CD tools to make vulnerability management easier with automation.
Pricing: Get a customized quote for the product features you need.
Digital Defense Frontline Vulnerability Manager
Best for: The vulnerability and penetration testing demands of SMBs.
Digital Defense Frontline Vulnerability Manager (Frontline VM) is a comprehensive and accurate SaaS vulnerability management tool that covers all network assets. Frontline VM is among the most user-friendly tools on this list. Digital Defense Frontline Vulnerability Manager is particularly well suited to the vulnerability and penetration testing demands of SMBs. That said, the on-demand service can meet the demands of a fully-staffed, large-scale organization.
Key Differentiators
- The platform utilizes proprietary scanning technology to perform thorough security assessments and helps prioritize critical threats, track results, and make remediation planning easy.
- Frontline VM’s vulnerability scanning mechanism efficiently detects internal and external vulnerabilities that can be exploited by miscreants.
- The tool helps drive regulatory compliance.
- Automatic smart labels for assets make them easily filterable and groupable.
- Easily track and manage your vulnerability management program from a centralized dashboard.
- Create customizable vulnerability and patch management reports.
- Another standout feature is role-based access control. With this feature, only allow access to assets that are relevant to users.
Pricing: Quotes available upon request.
Arctic Wolf Managed Risk
Best for: The security needs of penetration testers, developers, and SMBs.
Arctic Wolf Managed Risk is a risk-based vulnerability management solution that helps prevent cyberattacks before they occur. The platform provides guided remediation, essentially serving as an extension of your internal team, bringing a wealth of security knowledge and expertise to help harden customers’ IT environments. Arctic Wolf Managed Risk was built for the security needs of penetration testers, developers, and SMBs. The vulnerability management platform adds a services element to this list with a team of highly-skilled security experts.
Key Differentiators
- Arctic Wolf Managed Risk continuously scans your enterprise network, including endpoints and cloud environments to quantify threats.
- Risk monitoring goes beyond traditional vulnerabilities and includes ATO fraud detection, CIS benchmarks, and CSPM.
- The platform helps you determine threat exposure so you can identify and categorize risky accounts, assets, and software.
- From there, your Concierge Security team expert helps prioritize risk remediation to address vulnerabilities and reduce risk.
- All security observations are enriched with case management workflows, meaningful numerical scores, and digital risk information so you can cut through the noise and focus on what is most important.
- The platform’s risk-scoring mechanism helps you determine the most mission-critical vulnerabilities.
- Your assigned security expert creates on-demand executive reporting to help meet compliance needs.
Pricing: Fill out a form to request a demo.
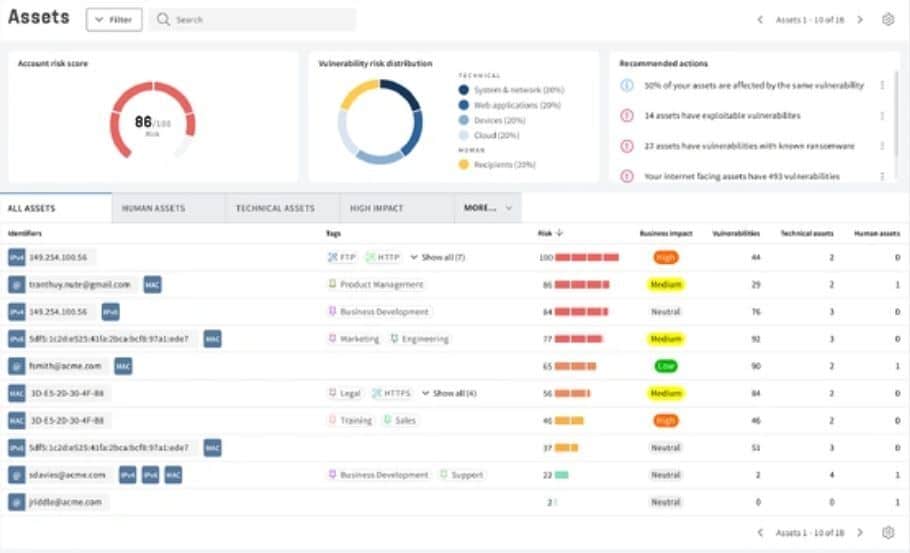
Balbix
Best for: Small businesses in North America and Asia.
Risk-Based Vulnerability Management by Balbix helps prioritize and mitigate risky vulnerabilities before cyber attackers can take advantage of them, as automated vulnerability management features take on a lot of the difficult work of addressing vulnerabilities. Balbix’s risk-based vulnerability management platform is highly rated by SMBs, with deployment heavily focused in North America and Asia. The end-to-end solution provides timely and accurate vulnerability data, and a user-friendly installation procedure makes it easy to get it up and running.
Key Differentiators
- Automated vulnerability management with Balbix, aided by the Balbix Security Cloud, enables continuous vulnerability assessment and the prioritization of vulnerabilities for mitigation.
- Vulnerabilities are prioritized based on security controls, business criticality, asset exposure, threats, and severity.
- With a continuous and automated vulnerability assessment mechanism, manual scans are unnecessary. Balbix offers broad visibility into your attack surface, including cloud and on-premises assets, with easy-to-use and configurable dashboards.
- Easily define remediation groups for business workloads and asset classes and allocate risk to risk owners.
- Systematic and documented exception handling allows you to track and revisit risk exceptions.
- With board-ready reporting, gain insights into risk reduction progress and determine the business value of the vulnerability management tool.
- Balbix has garnered acclaim for providing hassle-free software installation and good customer support.
Pricing: Fill out a short form to request a product demo.
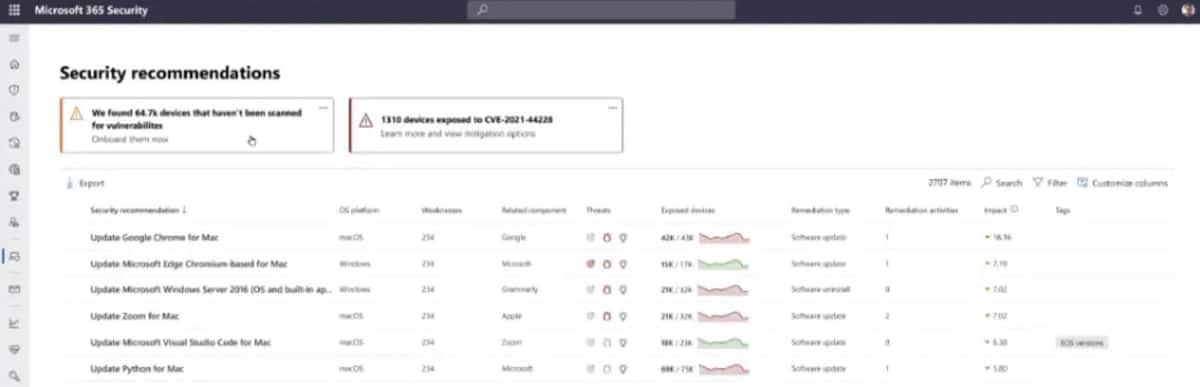
Microsoft Defender Vulnerability Management Tool
Best for: Patch and vulnerability management in PC-centric environments.
Microsoft’s new Defender Vulnerability Management is available for customer testing as both a standalone product and an add on to Microsoft Defender Endpoint. Microsoft also offers separate Defender-based solutions for cloud and containers. While likely best for Windows environments, the product supports macOS, Linux, Android and iOS, and some network devices too. Some early drawbacks are that the product does not currently show information for scanning open ports or detecting security or compliance misconfigurations that are not related to security patches, and information on scanned assets varies by OS, platform, and installed software.
Key Differentiators
- Creates a secure score for devices and multiple sorting options in the dashboard
- Recommends security fixes, can issue security tickets
- Discovers and scans devices and installed software on multiple OS and platforms including: Microsoft Windows 10 Version 1709 or later, macOS “Mojave” and later, some Linux distributions, iOS 12.0+ and Android 6.0+
- Scans selected network devices (currently: Cisco, Juniper, HPE Aruba, and Palo Alto)
- Detects devices not currently protected by Windows Defender as they connect to the network
- Can block use of vulnerable applications
Pricing: The Microsoft Defender Vulnerability Management tool can be obtained for a 120-day public preview trial. There is no licensing cost currently available but pricing will become available when the software moves to general release.
What is Vulnerability Management Software?
Vulnerability management tools proactively look for weaknesses by scanning and identifying assets and vulnerabilities in the network and providing remediation suggestions to mitigate the potential for future security breaches. It is an important way for companies to stay one step ahead of hackers.
Beyond just offering insight into how to remediate potential cybersecurity threats, some vulnerability management tools can assign threat levels to weaknesses, which allows IT teams to prioritize the most significant issues that should be addressed first. Some can even remedy certain vulnerabilities automatically by applying patches and making other fixes.
With thousands of new vulnerabilities affecting sprawling IT infrastructures each year, organizations need tools and services to help them find what needs to be patched and then apply fixes.
Also read: Is the Answer to Vulnerabilities Patch Management as a Service?
How Do Vulnerability Management Tools Work?
There are many approaches employed in vulnerability management.
- Vulnerability scanners scan all endpoints to search for missing patches, security holes, and other vulnerabilities.
- Penetration testing is an approach that uses a hacker’s-eye view of the enterprise to see how and where defenses can be breached.
- Breach and attack simulation (BAS) tools probe for weaknesses and provide a way to prioritize fixes.
- Vulnerability assessments analyze an organization’s overall security posture and vulnerabilities and can prioritize solutions.
- Patch management then applies the fixes prioritized by the vulnerability management tool.
Vulnerability management tools combine several of these approaches and add prioritization and remediation. Some products automate these functions to help ease the burden on overworked security staff.
How Much Do Vulnerability Management Tools Cost?
Some vulnerability management tools are open source, which makes them free. Smart IT and security personnel often keep a few of these tools handy for troubleshooting. Other tools are available on either a subscription basis or as software packages with varying costs. Many vendors publish pricing. Rapid7 InsightVM, for example, costs $23 a year per asset for 500 assets. while Qualys VMDR starts at $199 per asset.
Because of the heavy costs of breaches, almost any cybersecurity product will have a positive ROI, so the right tool is the one that best meets your needs.
Key Features of Vulnerability Management Tools
Vulnerability management requires a robust suite of features to encapsulate all of a company’s enterprise security needs. When deciding which of these cybersecurity solutions is best for your business, consider which of these features are most relevant to your needs.
Note that few tools provide all of these capabilities. Some provide a few, while some provide many of them. But coverage of all areas typically requires the use of several different products.
- Continuous monitoring and scanning for potential vulnerabilities
- Monitoring profile and rule system (IT can determine which systems and assets to monitor)
- Ability to set notification rules
- Attack surface visualization
- Attack vector analytics and modeling
- Risk-scoring
- Patch management
- Automated updates and patching
- Network access path analysis to identify problematic access routes and suggest lower risk traffic redirections
- Reachability analysis for endpoints and secured assets
- Customizable reporting, such as policy-driven compliance reports
- Automated remediation
IT asset management (ITAM) is an increasingly important part of vulnerability management, because organizations aren’t always sure of everything they own. Some vulnerability management tools offer asset discovery features, and also see our picks for the Top IT Asset Management Tools for Security.
Benefits of Vulnerability Management Tools
The benefits of vulnerability management are obvious. Vulnerability management leads to fewer breaches, and it offers a way to assess the organizational perimeter to see how secure it is in reality. It is also a great method of safeguarding data and spotting incipient attacks before they arise.
Most cyber attacks start from within, via email through phishing and social engineering attacks, so vulnerability management tools also plug the holes that allow lateral movement inside your network too.
Besides the protection offered by good vulnerability management software, automated product suites can save staff time that could be spent on more strategic projects. Therefore, a comprehensive vulnerability management package could pay for itself both in data breaches prevented and security staff time saved.
How to Choose a Vulnerability Management System
Those selecting vulnerability management tools should pay attention to the following points:
- What platforms does the tool operate on? Some are Linux only, some Windows only, and some cover multiple OSs.
- What endpoints are covered? Some are focused on servers, PCs, and laptops, while others extend to smartphones and IoT, wireless, and other devices.
- How much can be automated and how much work is required of IT staff?
- How familiar is IT with such tools? Don’t buy a Linux-based scanner if your IT staff are experienced only in Windows.
- Check out costs thoroughly. For paid scanners, pay attention to the fine print such as additional areas of potential extra cost, fees for support, etc.
- Be willing to have more than one solution. Often, a combination of tools is smart practice as one tool may miss something that another picks up.
Bottom Line: Vulnerability Management is Critical
There are roughly 20,000 new vulnerabilities discovered each year — and many of them are zero-day vulnerabilities that aren’t discovered until they’ve been used in a cyber attack. Plugging those holes takes a lot of time and dedication for even the most secure companies and networks. For everyone else, they need all the help they can get from vulnerability management tools and services.
Read next: Vulnerability Management as a Service: Top VMaaS Providers
Surajdeep Singh contributed research and analysis to this report.