Endpoint detection and response (EDR) not only helps IT teams identify threats on devices but also helps limit cyber attacks. To help you navigate this growing and fast-changing cybersecurity market, our team has researched and analyzed this list of top EDR vendors. Our analysis includes features buyers should look for and use cases for each top product.
Top EDR Solutions
- Palo Alto Networks Cortex XDR: Best overall
- SentinelOne Singularity: Best for small or junior teams
- CrowdStrike Falcon Insight XDR: Best for advanced response features
- Cynet 360 AutoXDR: Best for customer support
- Trend Micro XDR: Best for SMBs
- Cybereason: Best for tight security
- FortiEDR: Best for existing Fortinet customers
- Trellix: Best for analyzing security procedures
- Microsoft: Best for Microsoft users
- Broadcom Symantec: Best for overall research and development
- Honorable Mentions: Other EDR Solutions
- Key Features of EDR Tools
- How to Choose an EDR Solution
- Bottom Line: EDR Solutions
Palo Alto Networks Cortex XDR
Best overall
Palo Alto Networks has been posting top independent test results for so long that we’ve made the vendor our top overall cybersecurity company. The target market for Cortex XDR is sophisticated security teams, with ML-based behavioral analytics, sandboxing, and sophisticated response, root cause, forensics and investigation tools. But we were surprised to see that users give Cortex pretty high marks for ease of use, a sign that development efforts there have met with some success. And Cortex XDR allows those capabilities to be extended to include network, cloud and third-party data sources.
Pricing goes up as you add services, of course, but surprisingly, users give the company decent marks for value. In Cortex’s case, you get what you pay for. Users report that deployment can be a little challenging, but better than average support can help there.
Key features
- Automated root-cause analysis
- Forensic investigations of endpoint behavior
- Out-of-the-box detection rules as well as custom ones
Pros
- Sophisticated security and response features make Cortex XDR great for SOCs
- More user-friendly and value-conscious than you’d expect
Cons
- Might not be the tool for less sophisticated security teams
- Some implementation challenges
Pricing
Contact Palo Alto’s sales team for a quote for your enterprise. Note that while Palo Alto tends to be on the more expensive side, it’s a valuable solution especially for advanced security teams.
Deployment and integrations
Cortex XDR is installed as a software agent on endpoint devices. It’s a cloud-native platform. The Cortex XDR API allows users to integrate third-party ticketing systems of their choice. Cortex XDR also integrates with some third-party security products, but note that some features aren’t supported.
SentinelOne Singularity
Best for small or junior teams
SentinelOne is doing a lot of things right, between impressive MITRE evaluation scores and happy users. A few may quibble with ease of use and deployment, but those capabilities have plenty of fans too (and as initial deployment is a one-time event, it’s possibly the least important buying criterion, but ongoing ease of use is something all EDR buyers should be looking at).
SentinelOne has assembled an impressive array of offerings, including XDR and managed services, so customers have room to grow. The company offers a range of offerings and pricing, with some cloud and network security features available at additional cost. At higher price points, SentinelOne’s automated security features could be useful for overburdened or less sophisticated security teams.
Key features
- MDR capabilities like remediation and threat hunting
- Both structured and unstructured data integration
- Mobile device support
Pros
- Impressive array of offerings combined with strong security
- Automation features could relieve pressure on security teams
Cons
- Pricing could climb quickly for organizations with more complex security needs
- Some challenges with deployment
Pricing
For enterprise pricing, contact SentinelOne’s sales team. Note that Singularity has cloud and network add-ons, so if your business needs multiple cloud security tools, SentinelOne will likely become expensive.
Deployment and integrations
SentinelOne is deployed as a software agent on endpoint devices.
The Singularity Marketplace is SentinelOne’s dashboard for application integrations from other vendors. Partner integrations include Splunk, ServiceNow, Okta, and Zscaler.
CrowdStrike Falcon Insight XDR
Best for advanced response features
CrowdStrike rivals SentinelOne in popularity, as the two frequently come out on top in user satisfaction surveys. CrowdStrike offers strong security, within a percentage point of the top MITRE scores in our analysis, but where the company really shines is in its management and response capabilities. Unfortunately, security teams are so overwhelmed that they greatly value tools that make their jobs – and cleanup – easier. About the only place CrowdStrike scores below the highest-rated tools in our analysis is in value – those advanced EDR features come at a cost.
Users appreciate the AI- and machine learning-based features. Ease of use is about average for the sector, while ease of deployment and support rank above average. Threat hunting and intelligence, prioritization, containment, and investigation are some of the advanced features, and like most vendors on this list, CrowdStrike is expanding into XDR with cloud, network and managed services.
Key features
- Security posture assessment
- Threat context and awareness
- Falcon Sandbox for analyzing malware
Pros:
- Management and response features are popular with users
- Full range of advanced features
Cons:
- Above average pricing
- MITRE scores a notch below the highest. With any other vendor that would be a positive, but with a high profile comes high expectations.
Pricing
Like Cortex XDR, CrowdStrike is on the more expensive end. Falcon Insight XDR falls under the Falcon Elite plan, which requires potential buyers to contact the CrowdStrike team for exact pricing information.
Deployment and integrations
CrowdStrike is deployed as a software agent on all endpoint devices.
Network detection and response partners supported by CrowdStrike include Darktrace and Gigamon. CrowdStrike also has an API for integrating other third-party solutions.
Choosing between CrowdStrike and Broadcom Symantec? Read our EDR comparison.
Cynet 360 AutoXDR
Best for customer support
The 8-year-old Israeli company has rocketed up the charts, boasting both stellar MITRE results and positive user reviews. Ease of use and deployment are better than the industry average, and perceptions of value are a bit above average too. Like others on this list, Cynet is also making a play for the broader XDR market, and an MDR offering that’s free for users is a very nice added touch.
Some say the product gives off a few too many false alerts at first, but EDR systems in general tend to require some tuning. So far, user reviews rate the customer support team highly overall. Cynet hasn’t attracted much attention from analysts yet, but that’s likely to change if present trends continue.
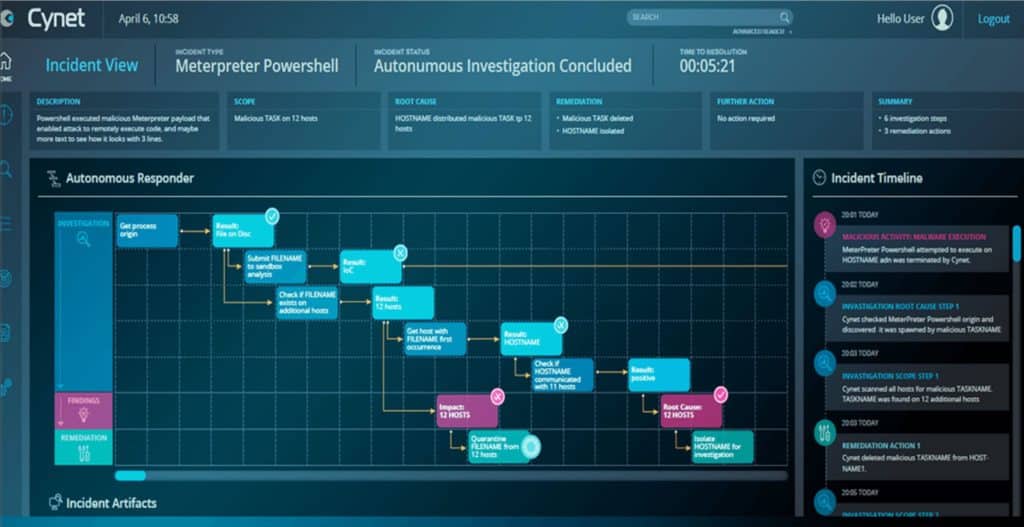
Key features
- Cynet Response Orchestration for remediation of compromised accounts and infections
- Deception technology to catch malicious activity
- Highly reviewed customer support team
Pros
- Strong security, positive user reviews, and broader XDR capability
- Free MDR
Cons:
- Not much analyst coverage yet, so as with all security purchases, talk to reference customers and your own network
Pricing
For specific details about pricing, contact Cynet’s sales team. Cynet offers demos for potential buyers to view.
Note that some features, like log management and enterprise-level support, are add-ons for some of the AutoXDR plans.
Deployment and integrations
Cynet offers on-premises, hybrid, SaaS, and IaaS deployment options.
Cynet has an API for integrations. It also includes integrations with remote monitoring and management (RMM) solutions and an Active Directory integration.
Learn more about deception technology solutions.
Trend Micro XDR
Best for SMBs
A first-gen antivirus vendor, Trend Micro is still going strong in its 33rd year. Independent security tests have been impressive, and users are generally pleased. Pricing can be difficult to compare across EDR vendors, but user perception of value is high, and it’s our impression too that Trend Micro is one of the best bargains on the EDR market.
Basic EDR includes vulnerability protection and data loss prevention (DLP), but pricing goes up for email, mobile, and web protection. Another vendor vying for the XDR space, Trend’s range of security offerings is impressive, spanning cloud, containers, network security, endpoint and more. Its managed XDR services are a good choice for businesses that don’t have an extensive IT team. Trend Micro’s endpoint solution was initially known as Vision One, but now the vendor more frequently references it as Trend Micro XDR.
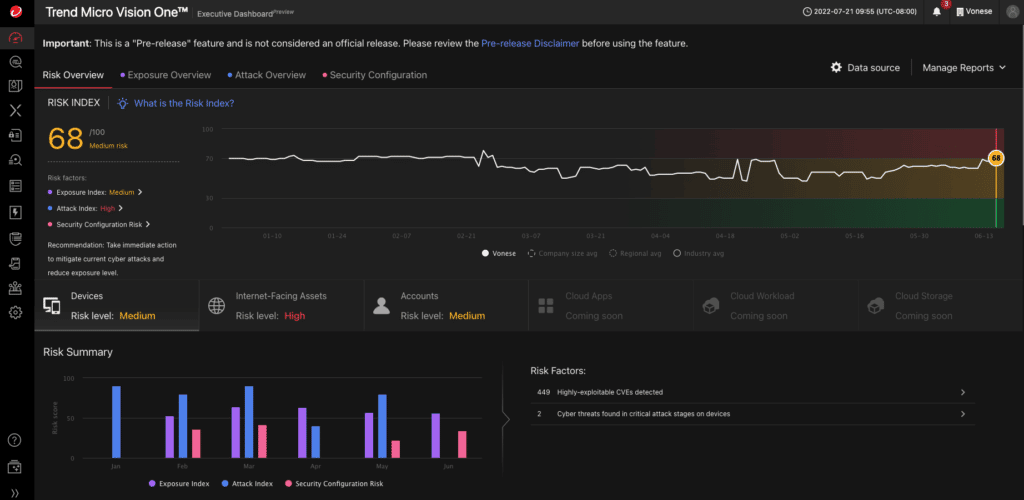
Key features
- Detection rules added based on discoveries from threat experts
- Policy adjustments based on recent insights through Trend Micro XDR
Pros
- Strong security at a good price
- Happy users
- Good XDR capabilities for those who want more
Cons
- Pricing climbs as additional protections are added
Pricing
To receive an exact quote from Trend Micro, contact its sales team. Customers can test drive the XDR solution. Trend Micro also offers a free trial for Vision One.
Deployment and integrations
Trend Micro lists multiple third-party security integrations for Vision One, notably Splunk, IBM QRadar, and Palo Alto Cortex XSOAR. Trend Micro also has a Technology Alliance Partner program. Strategic partnerships include Fortinet, HPE, LogRhythm, and VMware.
Learn more about using MITRE ATT&CK to better understand cyber attackers’ behavior.
Cybereason
Best for tight security
By our analysis, Cybereason came away with the highest score in this year’s MITRE evaluations. Given the strong competition in this key cybersecurity market, that’s a noteworthy accomplishment for the 10-year-old Boston-based company. Ease of use and deployment are above average, but user perception of value is about average. Some recent customer reviews noted delays in Cybereason’s support.
As an XDR provider, Cybereason’s platform covers network and cloud security too, plus managed services. While some XDR vendors offer more comprehensive product portfolios, none offer better security Cybereason’s independent security scores have been among the highest on our list.
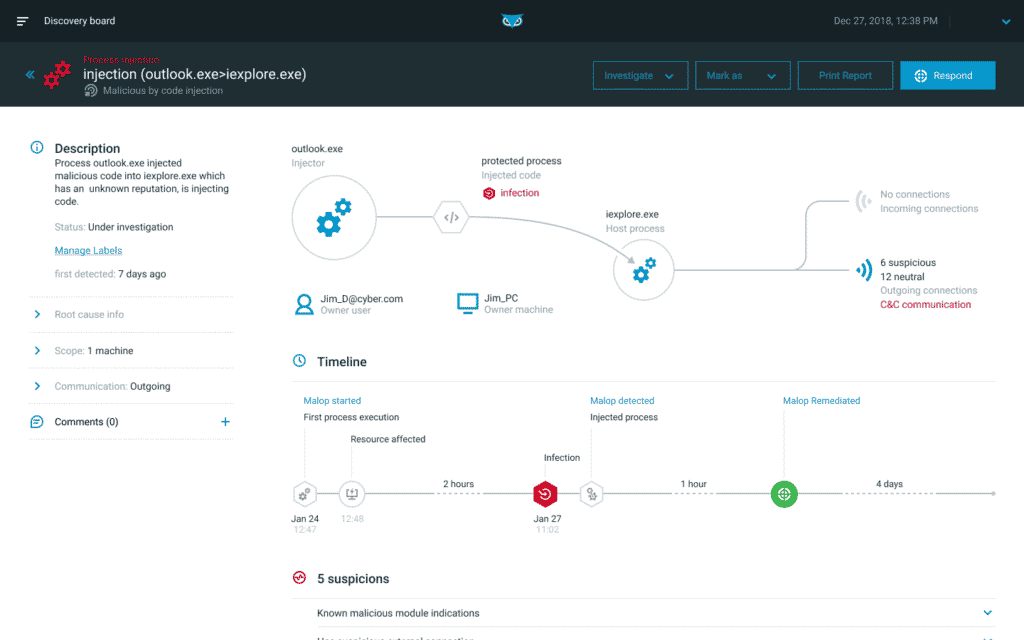
Key features
- Cloud integrations with Google, AWS, and Azure
- Malicious executable file blocking
- Cloud workload and container analysis
Pros
- Strong security combined with ease of use makes for a compelling endpoint security offering.
Cons
- XDR offerings aren’t as broad as other market leaders, and the solution may be less mature since Cybereason is a younger company.
- Some users report recent delays in customer support.
Pricing
Cybereason has four available plans. Pricing information for each is available through a Cybereason representative. Note that incident response is an add-on rather than a native feature in all plans except the most comprehensive, Cybereason Ultimate.
Deployment and integrations
Cybereason can be deployed in:
- Public cloud
- Private cloud
- Hybrid environment
- On-premises data centers
Aside from its major public cloud integrations, Cybereason also integrates with firewall and NDR tools for network content analysis.
FortiEDR
Best for existing Fortinet customers
Fortinet is best known for its firewalls, but endpoint security buyers may be overlooking an EDR product with high security and relatively low cost. MITRE scores have been near the top, and FortiEDR has stopped all 18 of the MITRE protection tests it has faced in the last two years. It’s good for Fortinet users in particular, and XDR buyers in general. If you already have FortiGate firewalls installed, consider expanding your security solutions to other tools in the Fortinet Security Fabric.
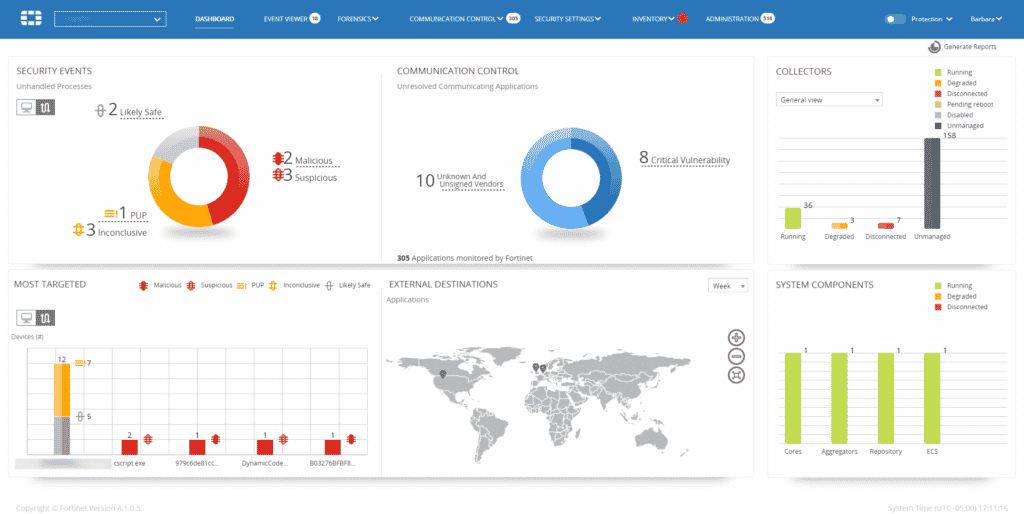
Key features
- Integrations with Fortigate and other Fortinet security products
- Support for role-based access controls and secure remote shell
Pros
- Great endpoint security with reasonable cost from a enterprise-grade firewall vendor
- Good choice for existing Fortinet customers
Cons
- Doesn’t get the visibility it deserves. Limited user reviews may make it challenging to unearth consistent data on user experiences.
Pricing
Fortinet offers a free product demo for FortiEDR. Contact Fortinet’s sales team for specific enterprise pricing details.
Deployment and integrations
FortiEDR offers cloud-based multi-tenant management, with cloud, on-premises, or hybrid management options.
Aside from integrations with Fortigate, FortiSIEM, and FortiGuard services, FortiEDR also allows users to create Custom Integration Connectors, which trigger responses to security incidents in third-party software.
Trellix
Best for analyzing security procedures
The merger of the security product divisions of McAfee Enterprise and FireEye is still shaking out, but there’s no reason to think that Trellix will lose ground in the EDR market. McAfee made this list in 2021, and after posting one of the highest overall scores in MITRE testing last year, Trellix EDR customers have no reason to worry, and adding FireEye expertise can only help.
Trellix has a strong base for its XDR ambitions and offers managed security services too. This an EDR product for sophisticated SOC teams.
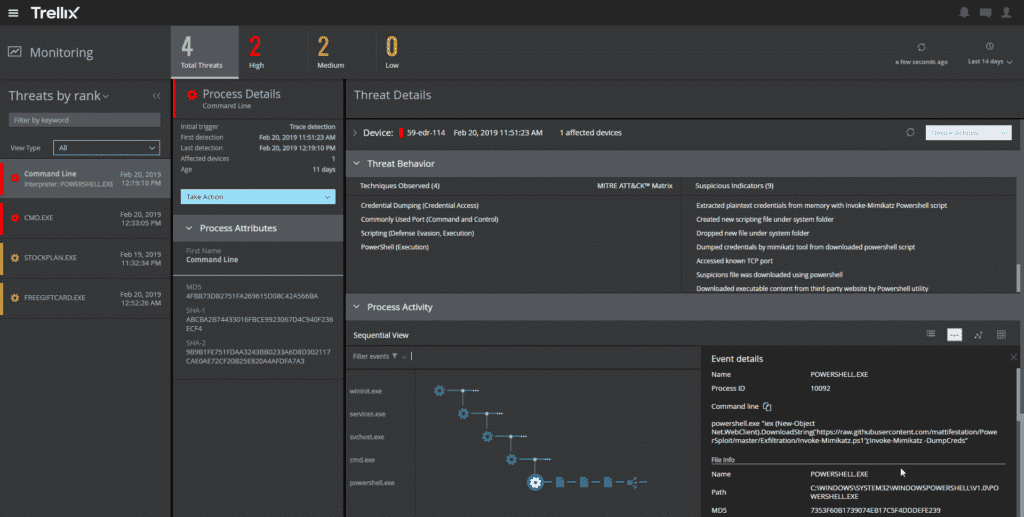
Key features
- Trellix Insights, which predicts whether security measures will be able to halt threats and prioritizes those threats
- Trellix Intelligent Sandbox for intensive malware discovery
Pros
- Very good security
- Comprehensive on-premises product portfolio
Cons
- Management and deployment could be easier
- SASE offerings were spun out as Skyhigh, so Trellix buyers may need to partner for edge and cloud security
Pricing
Potential customers can schedule a demo to learn more about Trellix EDR and must contact an expert at Trellix to receive further pricing information.
Deployment and integrations
Trellix EDR can either be deployed as an on-premises solution or as SaaS.
Notable security partners in Trellix’s Security Innovation Alliance include Fortinet, BeyondTrust, Forcepoint, and CheckPoint.
Microsoft
Best for Microsoft users
Microsoft has built a surprisingly strong security business, and consistently high scores in the MITRE evaluations is evidence of that. Of course, the product’s deep integration with Windows doesn’t hurt, but Microsoft has steadily added support for other operating systems – as evidence, look no further than the company’s successful MITRE protection test for Linux last year.
Microsoft Defender for Endpoint offers good value, and user reviews are pretty good, but ease of use and support have room for improvement. The product offers good vulnerability management and attack surface reduction. P2 is the package where advanced EDR features can be found, including automated incident response and investigation. If your business needs full response functionality, the P2 plan is the better choice.
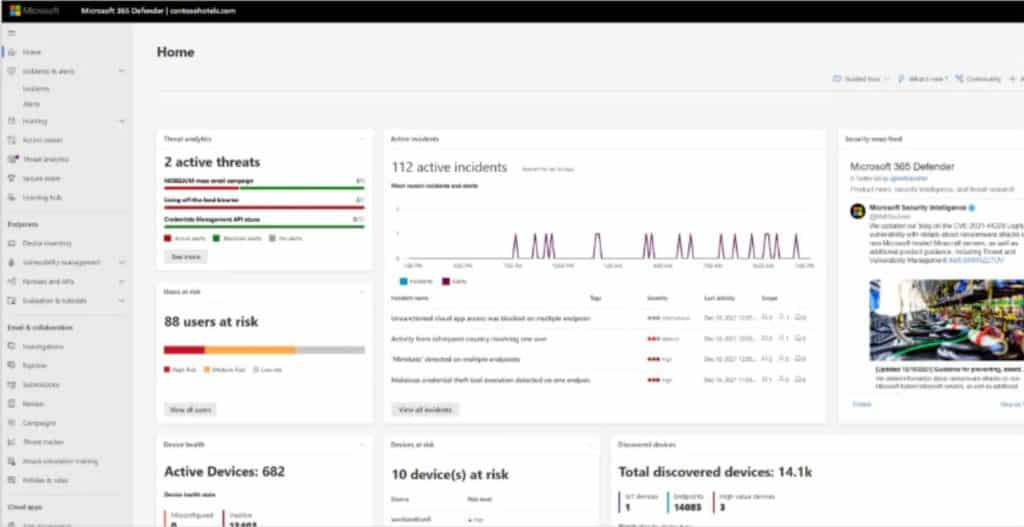
Key features
- Automatic security incident response
- Sandboxing for intensive malware analysis
- Third-party integrations
Pros
- Good security and value
- Deep Windows integration
Cons
- Ease of use and support could be better
Pricing
Microsoft Defender offers a free trial. Contact the vendor for exact pricing plans. Note that Endpoint P2 includes EDR capabilities, but the Defender P1 plan does not include EDR, though it does have anti-malware and network protection controls. If you need response and mitigation features, choose the P2 plan.
Deployment and integrations
Microsoft Defender is deployed as an agent on each registered device.
Along with integrations with other Microsoft solutions, Defender supports third-party integrations with Splunk, Bitdefender GravityZone, and Rapid7 Insight Connect.
Broadcom Symantec
Best for overall research and development
Symantec is another first-gen AV vendor that’s still got game. R&D efforts are well focused, which may give Symantec less flash because it’s not out chasing the latest marketing buzzwords. One example is adaptive protection, a feature that automatically shuts down processes and features that aren’t regularly in use.
Symantec’s endpoint security solutions also cover mobile, containers, servers, Active Directory, remote workers, cloud workloads, applications and storage devices from a single agent and console. AI-based security posture, policy and configuration management is another example of well-focused R&D, contributing to the product’s overall user-friendliness. Oddly, turning off advanced features for the MITRE evaluations may have led to a lower overall score last year after 2021’s terrific results, so don’t worry about that too much, and we’ll soon see MITRE’s 2023 results. Here’s hoping that Broadcom maintains strong security R&D regardless of how the proposed VMware merger shakes out.
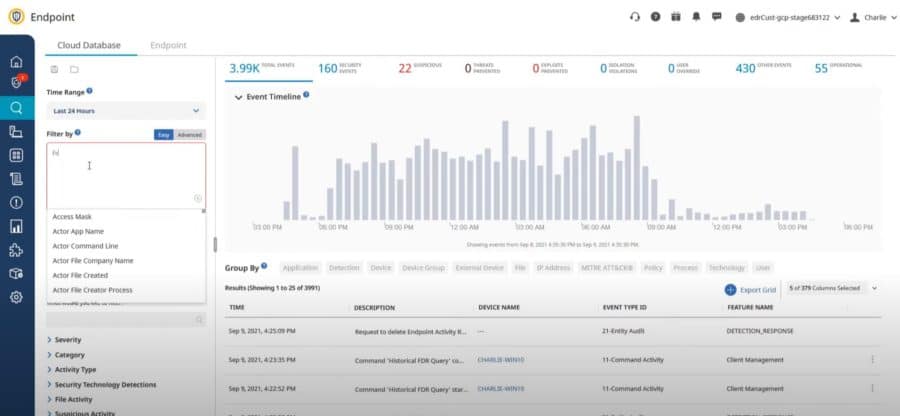
Key features
- Adaptive protection
- Sandboxing designed to detect virtual-machine-aware malware
- Outlier detection based on playbooks that report on anomalies in the infrastructure
Pros:
- Good security, innovation, ease of use and value makes for a strong offering
Cons
- Uncertainty over the proposed VMware acquisition may create near-term questions as users wait to see the development of Broadcom’s EDR lineup.
Pricing
Contact Broadcom’s sales team for EDR pricing.
Deployment and integrations
Symantec EDR can be deployed as a hardware appliance, the S550 series, or a virtual appliance.
For third-party integrations, Symantec Endpoint Security has its own REST API.
Honorable Mentions: Other EDR Solutions
The following endpoint solutions also have strong security and valuable EDR features and merit consideration by any organization in the market for EDR tools.
VMware Carbon Black
Carbon Black offers good security – one of 10 EDR vendors with an overall score of 90 or higher in our analysis of last year’s MITRE evaluations – but user reviews could be better, with ease of use, deployment and support showing room for improvement.
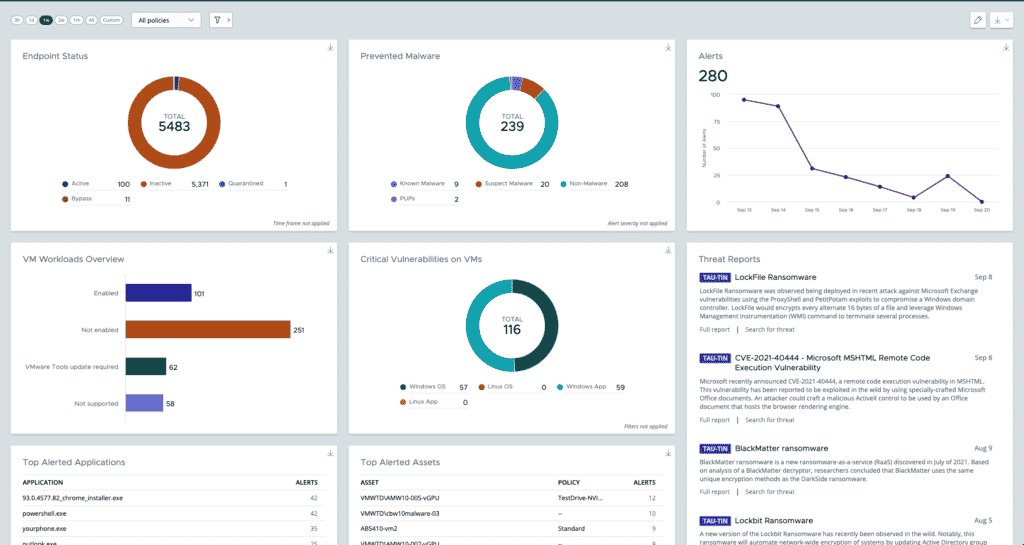
Assessments of the product’s security capabilities tend to be positive, and it’s popular with sophisticated security teams. Investigation, response and threat hunting are standout features. Carbon Black is a good choice for sophisticated security teams, but watch for Broadcom merger-related uncertainties as regulatory review in the U.S. and Europe plays out.
BlackBerry Cylance
BlackBerry Security’s Cylance was another endpoint security solution scoring above 90 in our assessment of last year’s MITRE evaluations, and that includes going 9-for-9 in the important protection steps covering both Windows and Linux. CylancePROTECT – BlackBerry Security’s EPP solution – tends to get better overall user ratings for value and ease of use than CylanceOptics, the company’s EDR tool.
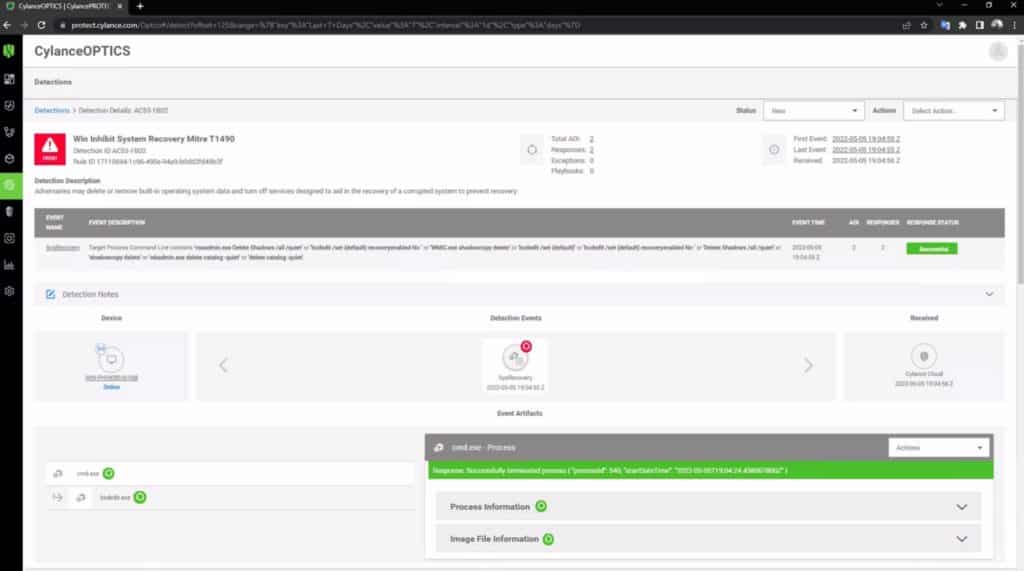
Users rate detection highly for both products, affirming the MITRE results. Investigation features also rank high, but some users reported difficulty with report limitations and issues with technical support.
Malwarebytes
Malwarebytes is highly rated by users, with detection and response capabilities getting high scores in customer reviews, along with ease of use and deployment. Value and investigation features are rated about average, but Malwarebytes prices its solution at about $6 a month per endpoint for the full EDR solution — costing less than some consumer antivirus software. The company’s posted a couple straight years of good MITRE results too, coming in a fraction under 90 last year in our analysis.
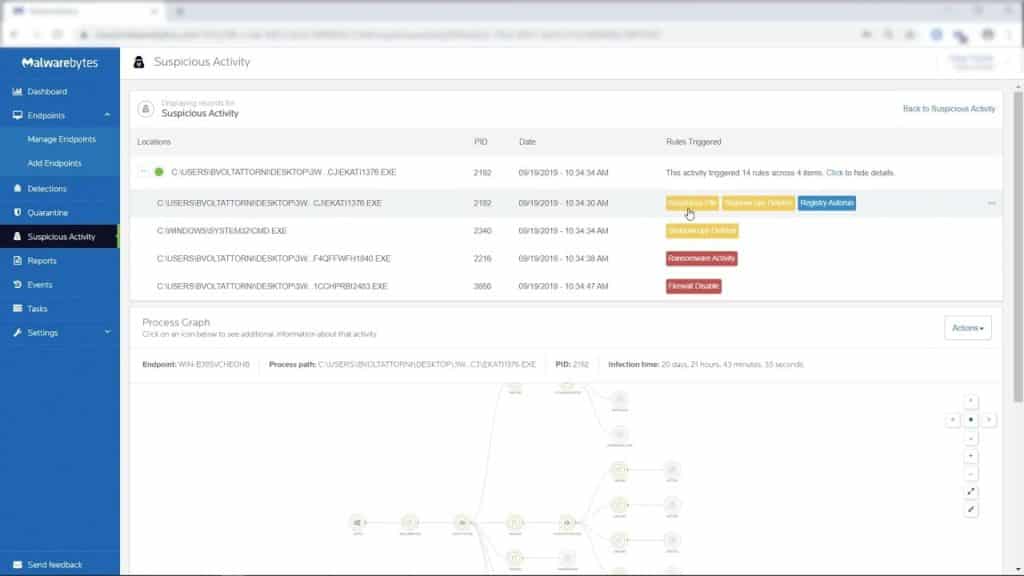
Primarily for Windows environments, Malwarebytes EDR checks a number of boxes, including automated response, guided threat hunting, remote work protection and ransomware rollback. Malwarebytes is a good choice in particular for small businesses that are primarily Windows shops, with some MacOS support available too.
Read more about next-generation antivirus solutions like Malwarebytes.
Check Point
Strong MITRE results, good ease of use, good value – there’s little in Check Point Harmony endpoint solutions that’s not to like. Automated detection, investigation, remediation and forensics – coupled with low cost – makes Check Point a good choice for SMBs in particular, and for existing Check Point customers looking to expand beyond firewalls and network security and into EDR, XDR and cloud security. Check Point is a winning solution for SMBs in particular.
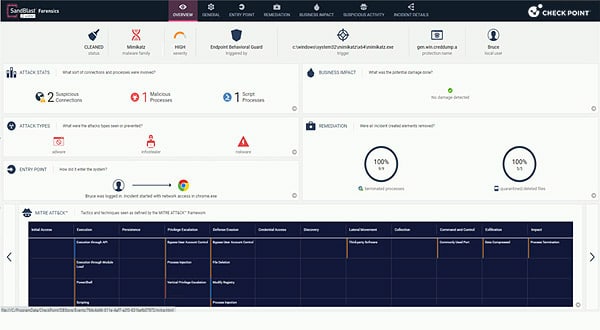
Is your business deciding between two of the major security providers? Read our comparison of Palo Alto and Check Point’s endpoint solutions.
Cisco Secure Endpoint
While Cisco Secure Endpoint (formerly AMP for Endpoints) may primarily appeal to Cisco shops, decent security and low cost coupled with good user scores for ease of use, deployment and support suggest that the product could find favor elsewhere too. Cisco has been steadily gaining in security, with zero trust, network security and XDR other areas to watch, but it remains to be seen if the company can move significantly beyond its formidable networking presence.
Sophos
Yet another first-gen antivirus software vendor that’s still going strong. Sophos hasn’t posted terribly impressive MITRE results in the last couple of years, but that hasn’t stopped users from being very happy – they rate Sophos Intercept X highly for value, ease of deployment, support and overall security. Threat hunting, automated response and root-cause analysis are a few of the standout features.
Deep Instinct
This 7-year-old NYC-based cybersecurity vendor wowed us with an 85 in last year’s MITRE evaluations, including an 8-for-8 performance in Windows protection tests. User reviews, while not numerous, are positive. This is one we’ll keep watching, and you should too.
Key Features of EDR Tools
Use this list of EDR capabilities to determine which your business most needs. Then you’ll be better able to choose EDR software that’s a good fit based on its features.
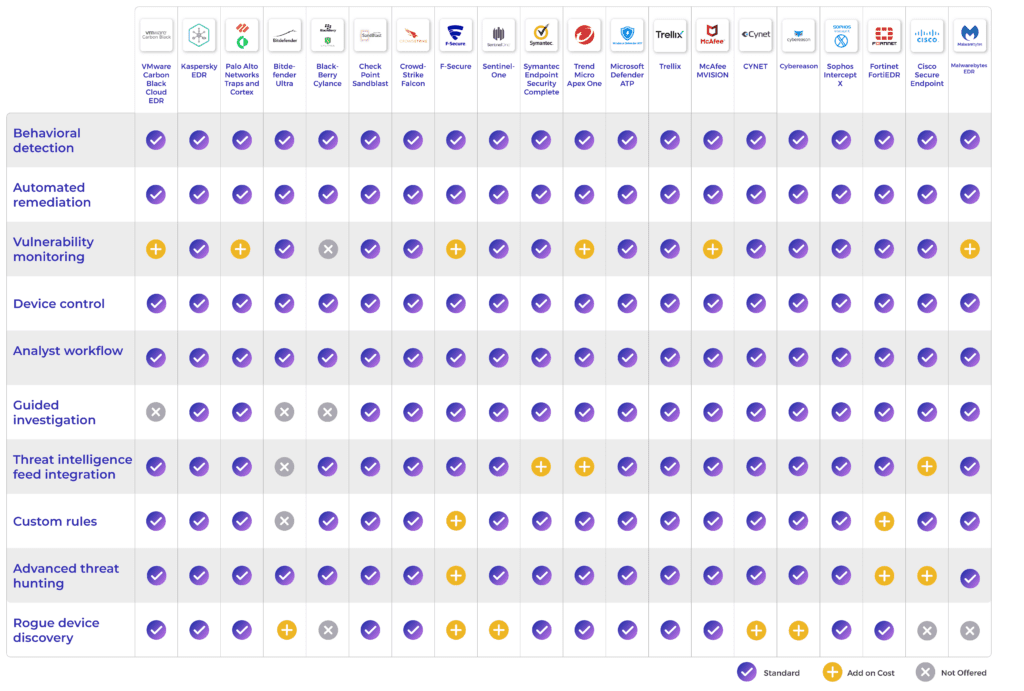
Compare Features Of EDR Software
Behavioral detection
Behavioral analytics use machine learning technology, which studies thousands to millions of user and device behaviors to identify abnormal patterns. These patterns could indicate a malicious user or a downloaded strain of malware. Behavioral detection is a key EDR feature because it uses an immense amount of data to automatically locate potential threats that would take much more time to detect manually, and can be helpful in zero-day attacks too.
Automated remediation
By setting remediation rules and actions in advance or using prebuilt ones, security teams can configure automatic threat remediation. A particular action on an endpoint triggers a predefined remediation policy, and without any human interaction, the EDR tool sets remediation in motion. Automation is a helpful tool because it significantly reduces manual remediation work for security admins and also responds more quickly to threats. It’s a particularly good feature for overwhelmed or less sophisticated security teams.
Vulnerability monitoring
EDR solutions consistently monitor endpoints, alerting security teams when the software unearths vulnerabilities that could be exploited. These can include outdated operating systems, backdoors, and misconfigurations. Automated searches for vulnerabilities are more efficient, allowing IT and security teams to catch them more quickly and spend their time on other tasks.
Device control
EDR solutions monitor USB devices and other direct-attached storage for malicious behavior. Threat actors use USB and flash drives to infect systems with malware, and employees often plug unfamiliar storage devices into computers without knowing what’s on them. EDR tools allow admins to set strict policies for device use and determine when to give remote access permissions to USB devices.
Analyst workflow
EDR solutions help security analysts create workflows to understand threats and then remediate them. This includes ranking threats by severity and viewing all events involved in a security incident. Some EDR solutions also allow analysts to create reports of the workflow so they can map the entire remediation process.
Guided investigation
A typical guided investigation in EDR helps walk IT or security personnel through studying threat data. Though it may look different for different vendors, guided investigation generally helps security teams and analysts study a threat and determine its root cause. This can include using machine learning tactics to point out threat details that humans might not observe, like frequency or timing.
Threat intelligence feed integration
Threat intelligence feeds are essential because they compile threats, Indicators of Compromise (IoC), and more in a format that can be ingested by a security system. Many EDR tools integrate with third-party threat intel solutions to give security systems even more behaviors and threats to look for. A broader range of threat information can help keep your business on top of threats.
Third-party integrations
EDR solutions usually can’t work in a vacuum — most businesses use other security tools, and it’s beneficial when they integrate with each other and can share data. Additionally, integrations with non-security software, like Slack or Microsoft 365, can be helpful for monitoring threats or communicating alerts.
Custom rules
Creating custom rules within your EDR helps businesses fit the security solution to their specific business needs. For example, if a security team notices a particular malicious behavior frequently, they may want to set specific detection and alerting rules based on the characteristics of that behavior to catch it earlier. Experienced security and IT teams in particular may want the ability to customize the solution.
Advanced threat hunting
EDR solutions continuously look for possible security threats on endpoints and computer systems. Advanced threat hunting features can help security teams find advanced persistent threats lurking in their systems. APTs are notoriously hard to find because they can reside in systems with little visible footprint.
Rogue device discovery
Many EDR tools track when a rogue device tries to access the network. Rogue devices are usually access points or computers that can serve as access points. They don’t have the same level of security as an EDR-protected device, and if connected wirelessly to an enterprise network, they can receive or initiate insecure data transmissions. These devices can be unsecured BYOD technology as well.
How to Choose an EDR Solution
The cybersecurity market is filled with highly-rated endpoint security software, which can make choosing one very overwhelming. This guide covers essential steps of selecting the appropriate EDR solution for your organization as well as recommendations for improving security overall.
Look at price
While good security is critical for all businesses regardless of budget, don’t ignore what your organization can reasonably afford. Some EDR solutions cost more than others. And just because they cost more doesn’t mean they’re automatically the best endpoint platform for every enterprise.
Additionally, consider whether the features you need are native to the EDR system or are priced as add-ons. While a plan might seem affordable at first, make sure that any response capabilities or other desired features won’t exceed your budget.
Consider team experience
Some EDR solutions are easier to learn than others. For IT and security teams with inexperienced personnel, you’ll want to select an easy-to-use platform. For highly experienced security technicians, a more customizable solution gives them more flexibility to design the EDR platform for your business’s needs. Also consider how challenging it may be to configure integrations. Some may only require a few clicks, but third-party integrations through APIs will need more intensive work.
Prioritize your most-needed features
Before buying an EDR solution, make sure you know which endpoint security features your business most needs. Do you want guidelines for your analysts to prioritize risks? Does your team need integrations with multiple threat intelligence feeds or with other security solutions like SIEM? Ensure that the EDR tools you’re considering have the capabilities your business most needs.
Don’t neglect user training
An EDR solution, though immensely helpful, will not solve all your security problems for you. It will take time to implement and understand — weeks, possibly months, and for some junior employees, probably years. But aside from that, it’s often business users and partners that make computer systems so vulnerable.
Hand in hand with EDR technology is employee training. In the excitement of an endpoint platform, don’t forget to eliminate some of the most basic endpoint security issues by keeping your employees aware and alert. They should know about:
- Email security — avoiding suspicious links
- Physical premises security — keeping uncredentialed strangers out of the office or data center
- Rogue device security — avoiding all unfamiliar USB drives and keeping them from company systems
- Password security — exchanging passwords over secured channels only and using different ones for all systems
Bottom Line: EDR Solutions
EDR is a foundational enterprise cybersecurity technology, as important as firewalls and SIEM. It’s important to choose the EDR system that best meets your organization’s needs and budget.
EDR tools provide businesses with both broad and granular views of their threat landscape — overall threat patterns as well as specific behavior on a single endpoint. They’re critical for enterprises with many endpoint devices, including but not limited to servers, desktops, and laptops.
Don’t rely on your EDR to immediately fix everything for you. It takes time to learn, implement, and tune any endpoint platform, but the long-term benefits are worthwhile, including the experience security staff will gain from using any EDR software. As your IT and security teams learn to recognize behavioral and threat patterns, your enterprise will be more prepared overall to secure your endpoints and broader infrastructure.
Considering a broader range of security solutions? Read more about the best cybersecurity software for businesses.