Despite all the advances in cybersecurity tools, employees remain the weak link in organizations’ digital armor. Fortunately, cybersecurity awareness training programs have grown in both number and sophistication, giving businesses a better chance to keep a single phishing email or malicious link from turning into a crippling cyberattack.
With so many options available, it can be difficult for companies to find the best cybersecurity training tools and services for their needs. Here then are our picks for the best cybersecurity training tools, followed by a discussion of product features and buying considerations.
Top Cybersecurity Training Tools for Employees
The following companies were selected for the quality of their features and content, in particular their training materials related to phishing. Many of them have also scored high on resources like the Gartner Magic Quadrant and the Forrester Wave for Security Awareness Training.
- KnowBe4: Best Overall
- Proofpoint: Best for Customization
- Ninjio: Best for Multilingual Teams
- ESET: Best for Gamification
- Cofense: Best for Phishing
- Lucy: Best for European Businesses
- CybSafe
- Elevate Security
- Mimecast
- Living Security
- SANS Institute
- Infosec IQ
KnowBe4: Best Overall

Key Features:
- Interactive browser-based training
- Skills-based and culture surveys focus on improving security culture
- Custom phishing templates and landing pages
- Employee engagement to report suspected phishing
- Comprehensive training library with fresh content
- AI-driven phishing and training recommendations
- USB test, vishing, and smishing included
In terms of pricing, KnowBe4 offers four pricing tiers for interested buyers, priced per seat per year with scaling rates based on the total number of seats in a class. Each tier offers more security training features to go with the increased price. There are also three add-ons that users of any tier can purchase as part of their subscription. The prices on these also scale with the total number of seats in a class.
Proofpoint: Best for Customization

Key Features:
- Consistent training around the globe with multi-language support
- Track progress with dynamic reporting and a results API
- Integration with Target Attack Protection (TAP)
- Detects Very Attacked People (VAPs) and Top Clickers in the organization, giving insight into the types of threats they’re receiving or engaging with
- ThreatSim Phishing Simulations to understand susceptibility to a variety of phishing attacks
- CyberStrength knowledge assessment tool assesses user vulnerabilities beyond email and USB drives, covering critical security issues such as the use of mobile devices, social engineering scams, passwords, and web browsing
Pricing for Proofpoint’s training is included as part of its Proofpoint Essentials service. Subscribers to that service can access its security awareness training for $1.10 per active user per month. A free trial for the company’s training service is also available.
Need More Ways to Upgrade Your Cybersecurity Knowledge? Take a Look at Top Cybersecurity Podcasts 2023
Ninjio: Best for Multilingual Teams

Key Features:
- Hollywood-style storytelling for better connection and engagement
- Uses real-life examples
- New episodes each month
- Offers a private hosting portal
- Interactive quizzes in multiple languages
Interested buyers should contact Ninjio for pricing information.
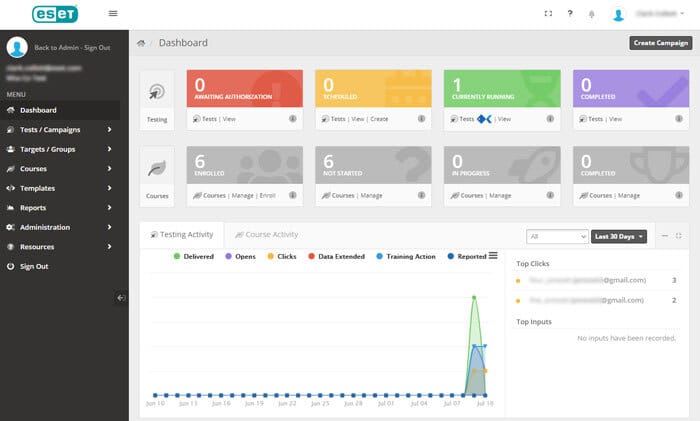
ESET: Best for Gamification
ESET cybersecurity training provides on-demand training that allows employees to follow along at their own pace and repeat courses when they need a refresher. Rather than covering all of the issues surrounding cybersecurity, the courses focus on the ones employees are most likely to face, like phishing, credential theft, and social engineering. There’s a free option that covers the basics and best practices for remote employees, but if you want gamification, email reminders, and a phishing simulator, you’ll need to upgrade.
Key Features:
- Phishing simulator
- Takes less than 90 minutes to complete
- Over 30 years of research and in-house training experience
- Real-time reporting
ESET offers two forms of security awareness training: a free, basic 60-minute course and a paid, premium 90-minute course. The premium course provides additional features like gamification, a phishing simulator, and automatic email reminders. The premium course starts at $250 for training 10 employees and scales up from there, to a maximum of $1625 for training 100 employees.
Lucy: Best for European Businesses
Lucy is focused mainly on the European market but has been growing steadily and has established a U.S. office. It consists of a series of modules to test, train, and engage employees as well as test the infrastructure to look for weaknesses. As well as phishing attacks, it educates users on ransomware, portable media attacks, malware simulations, file-based attacks, and spoofing attacks via realistic simulations.
Key Features:
- A variety of predefined, multilingual attack simulations (phishing, malware, smishing, USB attacks, etc.) test whether employees are really familiar with the dangers of the Internet
- More than 200 interactive, web-based training modules (videos, tests, quizzes, games, etc.) on various security topics
- Integrated authoring tool allows companies to create new learning content, or Lucy can create custom content
- The Lucy Mail Plugin for Gmail, Outlook, and Office365 integrates employees into the detection of and fight against cyberattacks
- Monitor attack statistics and eLearning progress in real-time
- Track all attack simulation statistics like the number of emails that were opened, how many links were clicked, and how many attacks were successful
Lucy currently offers three tiers of its training service, but interested customers will need to contact the company directly for pricing details.
Cofense: Best for Phishing
Cofense PhishMe takes a broader view than staff education. In addition to training, it catches the phishing emails that bypass email gateways. It rapidly detects, analyzes, and automatically quarantines phishing attacks. In addition, the company offers PhishMe Playbooks that are 12-month programs with phishing simulation scenarios, landing pages, attachments, and educational content.
Key Features:
- A Smart Suggest capability uses algorithms and best practices to recommend scenarios based on current active threats, industry relevance, and program history
- Cofense Reporter provides detailed reporting on phishing patterns and results
- Cofense PhishMe Catalog has thousands of educational assets, including videos and infographics
- Automated responses to phishing attacks
- Includes technology to detect and catch phishing email attacks to prevent them from reaching users
Interested customers will need to contact Cofense directly for pricing information.
CybSafe
CybSafe offers simulated phishing, training, and the ability to establish risk perception levels. By assessing someone’s basic knowledge of security with a few questions, their perception of different risks, and how confident they are, CybSafe can tailor itself to each person’s needs with personalized awareness training, security advice, and threat updates.
Key Features:
- Data-driven personalization means that each person receives the content they need
- Metrics and insights on what’s working and what’s not
- Understand how people learn best, how well knowledge is retained, and changes in confidence
- NCSC certified training
- Security culture assessment
- Access anywhere on mobile and desktop
CybSafe offers 5 tiers for its training service. The first tier, Starter, is free. Potential customers must contact CybSafe directly for a pricing quote for the remaining 4 tiers.
Elevate Security
The Elevate Security Platform uses benchmarks, tailored security controls, and personalized feedback to focus attention on risky employees. Once again, it is technology backed by user education rather than purely being user security awareness training.
Key Features:
- Orchestration with security controls, decision support systems, and executive dashboards
- The attack surface is analyzed and defended across actions, access, and attacks
- Leverage existing incident data from security technologies and employee data from HR sources
- Creates human risk scores for analysis
- Orchestrate policy and automate response
- Decide which security tools and systems to control, for whom, and at what level
For pricing, Curious buyers will need to get in touch with Elevate Security personally.
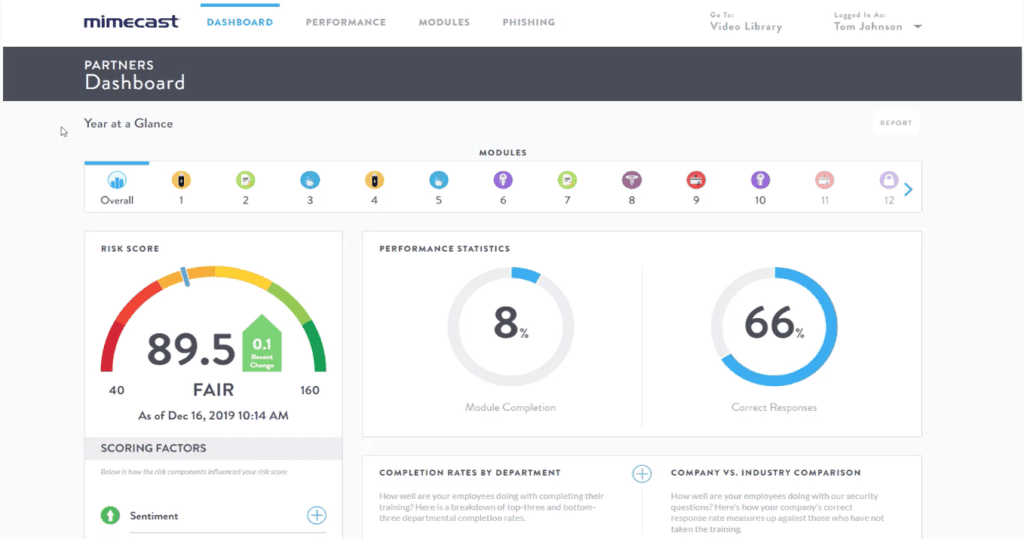
Mimecast
Mimecast Cyber Awareness Training uses humor to engage employees and change behavior via awareness training videos. It uses recurring characters and themes to communicate information with content written and produced by TV and film industry professionals in an effort to maintain employee attention and reinforce training.
Key Features:
- Each cybersecurity training module takes no longer than three to five minutes to complete
- Reinforces key concepts by delivering training to every employee once a month
- Those who need more help based on test results and risk scoring can receive targeted training
- Multiple languages supported
- Integration with Mimecast email security technology streamlines phish testing and analysis
Interested buyers should contact Mimecast directly for pricing details.
Living Security
Living Security sees security awareness training as a starting point where human risk management is the next evolution in decreasing cyber threats in an organization. It focuses on risk minimization rather than KPIs based on a phishing report. As such, the company provides personalized campaigns of content based on the threat indicators of the customers. This includes live-action experiential learning rather than video training of long modules (10 to 30 minutes). Living Security uses gamification to increase employee engagement.
Key Features:
- Security Awareness Program Owners (those in charge internally in organizations for launching security awareness programs) are provided with internal marketing campaigns to help rally internal end users to willingly do the security training
- Human Risk Management through Living Security UNIFY, an integrated analytics platform that leverages security data to produce insights, enabling targeted interventions and to improve the overall security of an organization
- CyberEscape Online utilizes gamification principles, with storylines, strong narratives, and engaging puzzles
- Company-wide leaderboard that brings employees together while learning how to be more secure
- Specifically developed for CISOs, CIOs, CSOs, IT directors, IT managers, and security awareness program owners
Living Security only makes its pricing information available to users who contact the company directly.
SANS Institute
SANS Technology Institute offers full undergraduate and graduate programs in cybersecurity, but it also offers employee training for businesses. The computer-based training includes different training styles to match your corporate needs and employees’ learning styles. It includes challenging games that keep users involved and helps them retain the information better. Additionally, SANS offers an Insight Risk Assessment, allowing your organization to prioritize training on the threats you’re most likely to face.
Key Features:
- Custom cybersecurity awareness programs
- Knowledge assessment lets organizations avoid wasting time on skills their team has already mastered
- Behavioral awareness tools to assess risk
- Phishing simulator with different tiers of difficulty
- Automated delivery of tests over a 12-month period
SANS Technology Institute has no publicly available pricing information. Prospective buyers should contact the Institute to learn more.
Infosec IQ
Infosec IQ offers pre-built cybersecurity training programs or allows companies to build their own from existing modules. There is a large content library complete with both industry and role-specific training modules to prevent your employees from learning about topics that don’t impact them. The phishing simulator provides instant feedback when a user takes unsafe actions, so they can safely learn from their mistakes. There are over 1,000 pre-built simulations to choose from, but you can also build your own.
Key Features:
- New phishing templates are added weekly
- Infosec team is very involved with implementation
- Flexible and customizable reporting
- Short training videos improve retention
- No tiered access to content
Infosec IQ’s security awareness training comes in three tiers, each with more features than the last. However, the prices on these three tiers are not publicly available. Interested organizations will need to complete a form on Infosec IQ’s website in order to unlock pricing details.
Need More Cybersecurity Training Options? Read Top 15 Cybersecurity Certifications for 2022
What Are Important Security Training Product Features?
The vendors in this field are quite varied. Some are squarely focused on user education while others are developers of security tools that have expanded into the training arena.
Key features from the standpoint of employee security training include:
- Varied training, not one size fits all
- Engaging, educational content that helps employees really understand the cybersecurity essentials
- Simulated phishing capabilities, smishing, vishing
- Single platform as opposed to a few features cobbled together
- Low administrative overhead and no jumping from screen to screen
- Library of training and phishing content
- Ability to customize
- Real brand logos used for phishing
- Multiple languages
- Randomization of phishing campaigns
- Reporting
- Security assessments
How Do You Choose the Right Cybersecurity Training Course?
Those considering their security awareness training options should consider the following:
- How is user management handled? Is it a manual process? You want to assess the ease of administration of whatever vendor you choose. If there are multiple systems or consoles, be sure to ask the degree of integration between those systems
- The volume and quality of training content provided. How important is it to your organization to have an ongoing campaign with fresh content? A small training library means stale and infrequent training. And content needs to be engaging, so try it for yourself to get a feel for the vendor’s approach.
- Availability of localized training, phishing content, and international/multilingual content to sustain frequent training.
- Is the vendor dedicated to security awareness training as its core focus, or is it an add-on to a wide variety of products that are bundled as integrated?
- What does customer support look like and how well is it reviewed?
- Find out how many capabilities come with the subscription level, what functionality is included versus what requires managed services and extra fees.
- What reporting and support features are included with the subscription?
- Is customized and branded training content important? If so, check to see if branding capabilities are in the platform.
Phishing and Ransomware are Top Employee Security Concerns
The current focus of most security awareness training initiatives is on phishing – and with good reason. Phishing is responsible for the bulk of breaches. Users get hoodwinked into clicking on a malicious attachment or URL and this inadvertently lets the bad guys in. The never-ending threat posed by careless end users has also raised the profile of other solutions like secure email gateways.
As a productivity tool, the email inbox has proven to be both a blessing and a curse. HP Wolf Security reported that 89% of malware now comes from email—a sign that web and browser security are improving, but email remains the big problem.
Among the types of attacks that workers often fall for, “phishing, spear-phishing and/or whaling” is number one, according to Dan Lohrmann, CSO at security awareness training provider Security Mentor.
“Remember that phishing can happen with people clicking on links in emails, but also via social media and even phone calls,” Lohrmann said. Also, people are still opening attachments from strangers, he added.
Social engineering essentially involves running a con, using email or a phone call, to gain access to a protected system or information through deception, often via spoofing. In the case of spear-phishing or whaling, both terms for more targeted attempts at scamming important high-value individuals, a considerable amount of effort can go into fooling victims.
Lance Spitzner, director of Security Awareness at the SANS Institute, cautioned that scammers like to use social engineering to make their victims jump to attention and get hearts racing.
“The most common tactic cyber attackers use is creating a sense of urgency, pressuring or rushing people into making a mistake,” Spitzner said. “This can be a phone call where the attacker pretends to be the IRS stating your taxes are overdue and demanding you pay them right away, or pretending to be your boss, sending you an urgent email tricking you into making a mistake.”
Research from Cofense, home to the PhishMe simulation program, shows that workers tend to lower their guard when money is involved. John “Lex” Robinson, anti-phishing and information security strategist at Cofense, says, “All these models involve the exchange of money, an emotionally charged topic that elicits strong responses,” he said.
Some attackers don’t care much about stealing valuable information. Instead, they use malware that encrypts a victim’s files and holds them hostage without ever transferring the data. They demand a ransom for the encryption key that restores access to those files, hence the term ransomware.
Approximately 37 percent of global organizations said they were hit by ransomware in 2021, according to an IDC survey.
“Ransomware and phishing continue to be the most common attacks users are falling for,” observed Rob Clyde, chair of ISACA and executive chair of White Cloud Security. “Moreover, attackers often find that it is easier to make money using ransomware attacks.”
Good data protection practices, particularly maintaining reliable backups, can make ransomware more of an inconvenience than a cripplingly expensive cybersecurity incident, although IT security teams and administrators will likely have their hands full sanitizing affected systems.
Employee Security Awareness Tactics That Work
It may seem like an uphill battle, but there are ways businesses can arm their employees against these and other devious methods attackers use to scam businesses out of sensitive information or their cash.
Here’s what to consider while evaluating a security training awareness vendor or creating a program of your own.
1. Start On Day One
When a new employee comes on board, security training typically takes a back seat to filling out HR paperwork, being assigned to a work area, and getting issued a laptop. Brandon Czajka, virtual chief information officer at Switchfast Technologies, believes in getting employees ready for the cybersecurity threats they’ll encounter during any given workday from the moment they accept a job offer.
“There are several security training vectors available out on the market that can easily be incorporated into an organization’s new hire onboarding process or used as a frequent means of keeping these threats front of mind,” Czajka said, noting that many are similar in this regard.
2. Watch Emerging Threats
The cybersecurity landscape can change drastically in no time at all, which is why it’s important to use a security training awareness vendor or service that keeps its finger on the pulse of the market so that employees don’t wind up blindsided by the latest scam.
“Ultimately, it is best to select a training platform that not only defines past data breaches and how organizations responded to them – learning from past mistakes – but also one that keeps the training material up to date with new breaches as they occur in real-time,” Czajka said.
3. Practice Makes Perfect
Simulations are used to sharpen the reflexes of air pilots and military personnel in challenging situations and to teach them how to respond. Similar information security training can expose employees to the latest deceptions and attacks, helping them guard against risky behaviors that can lead to data breaches.
Cofense’s Robinson advocates a similar “learning by doing” approach to block security threats that workers may encounter during the course of their jobs.
“This is best accomplished through the use of active threat simulations that provide the end-user an experience they will remember and a new action to take; in the case of phishing, the new action is reporting [the threat],” said Robinson. Organizations that fail to instill this mindset lose the ability “to address and mitigate threats in real-time,” he added.
4. Explain Why
Learning with the immediate feedback provided by security simulations can help concepts stick, but companies can go further by making it clear why the training is important.
“User engagement is further driven by transparency within an organization,” Robinson said. “To that end, awareness and training materials need to clearly outline why security is important both at work and at home. In other words, make the training personal.”
5. Fix The Password Problem
Weak, reused, and easily guessed passwords continue to be a major security weak spot. According to First Contact, 51 percent of employees use the same passwords for both personal and work logins. They also show that 57 percent of users who have fallen victim to a phishing attack didn’t change their passwords afterward.
Enforcing password policy is one step enterprises should take, combined with multi-factor authentication.
Training Isn’t the Only Way to Help Employees Fix the Password Problem. Check Out the 8 Best Password Management Software & Tools for 2022.
Elements of a Successful Employee Security Awareness Training Program
If you want employee security awareness training to work, you need to learn what to look for in the programs you’re considering.
Know Your Audience
Messaging matters, and effective training programs let organizations tailor their content to their audiences.
“The message is different for a group of government internal auditors than for a room full of COs from large companies,” Security Mentor’s Lohrmann said. Other factors to consider include jargon, current hot-button issues, the order in which speakers or instructors appear, and topics to broach. Don’t force your entire team to sit through training on issues that only IT will ever have to deal with.
Prioritize Storytelling
Droning on about the technical aspects of a cyberattack is a surefire way to lose an employee’s interest. “Audiences love cyberwar stories,” Lohrmann advised. “People remember stories much more than facts and figures.” Choose training programs that tell stories and can connect with employees in a way they’ll understand.
Choose Interactive Learning
Get the crowd involved to help employees retain the material presented to them. Look at programs that offer interactive modules or simulators to help employees practice what they’re learning. This practice will improve both engagement and retention. At the very least, ask for a show of hands and pepper sessions with questions for a more engaged audience, said Lohrmann.
Quantify Results
What is the point of raising staff security awareness if a program falls short on the “awareness” part?
“You need the ability to measure those changes in behavior and the overall impact those changes are having to your organization,” cautions Spitzner. Your training program should include an analytics module, helping you see how employees are performing on their simulations, so you can address mistakes in a safe environment.
Effective Online Training
The secret to good and effective online training is keeping it “brief, frequent and focused on a single topic,” Lohrmann said. Additionally, it should be ongoing to help users keep up with the latest trends. Echoing some of the themes above, it should also be engaging, entertaining, and interactive.
When looking at training programs, consider how often vendors come out with new content. New threats are always emerging, and your training needs to evolve to keep up with them. Cybersecurity training isn’t a one-time thing, but a constant reminder of the threats your business is facing and how your employees can help guard your data.
Bottomline: Choosing the Best Employee Cybersecurity Training Service
Finding the right cybersecurity training service can be difficult, but there are some things to keep in mind that can help.
Make sure the service is flexible, with features like customizability and varied training routines to make sure the service can be tailor-made for your organization’s needs.
Keep an eye out for services with solid training for phishing. Phishing is one of the biggest dangers that good cybersecurity training can delay or stop entirely, and if a service does not prioritize phishing as a central concern, it might not be worth purchasing.
When you have the right training solutions for your organization, it’s also important to start training employees immediately. From the day a new employee starts with your business, they can be hit with a phishing attack trying to steal their access credentials. By implementing cybersecurity awareness training early and often, you’re better able to keep your organization safe.
These tips and others discussed above will be invaluable in helping you select and implement the best cybersecurity training for your business.
This article was updated by Zephin Livingston on December 27, 2022.